Description
Masquerading as Elastic Endpoint Processes is a defense option (e.g. via Process Hollowing or RunPE where binary path and file system details are identical) that may bring some behavior detection or prevention advantages to an attacker. This rule looks for suspicious parent processes.
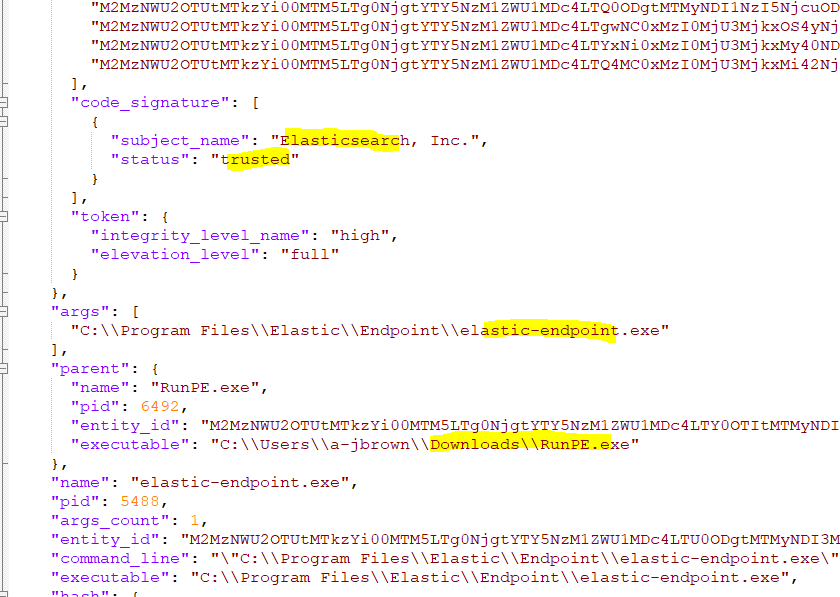
Required Info
- Target Operating Systems:
- Target ECS Version: x.x.x
- New fields required in ECS for this?
- Related issues or PRs
Optional Info
Example Data