-
Couldn't load subscription status.
- Fork 720
Add 'expireIn=' option and use in the openssl command #1154
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Add 'expireIn=' option and use in the openssl command #1154
Conversation
|
Hey @icyrizard, can you please refrain from linking to an issue in commit messages? It messes up the history/conversation in GitHub. See the log in #1153 |
|
@driesvints Ah I see, my bad, I honestly thought that was a useful feature before you mentioned this. I'll squash the commits into one. |
4e0ad6d to
4283dae
Compare
|
Thanks @icyrizard! This looks great. Per @driesvints's suggestion, I'd also like to see if we can use some of this same code to allow people to update expired/expiring certificates per #1103 |
|
Not sure if this was meant to fix it or if this caused it, but I just reinstalled my local setup due to a PHP version upgrade and started getting this after I tried to ➜ samuel@MacBook-Pro ~/Sites/helpdesk git:(master) ✗ valet secure
Enter PEM pass phrase:
In Nginx.php line 138:
Nginx cannot start; please check your nginx.conf [1: nginx: [emerg] cannot load certificate "/Users/samuel/.config/valet/Certificates/helpdesk.test.crt": BIO_new_file() failed (SSL: error:02001002:system library:fopen:No such file or directory:fopen('/Users/samuel/.config/valet/Certificates/helpdesk.test.crt','r') error:2006D080:BIO routines:BIO_new_file:no such file)
nginx: configuration file /usr/local/etc/nginx/nginx.conf test failed
].
secure [--expireIn EXPIREIN] [--] [<domain>]Was pretty confusing to debug, but after adding some And therefore only creating the Passing the number of days manually using My guess is that the issue is caused by this line having Line 182 in 8ff6840
So if you have time right now, please test if you can reproduce this and if setting I wanted to open an issue pointing this out and saying that passing the Either way, it would be great to patch this at least somehow and tag a new release, since right now running |
|
Figured that I can fix this faster than someone else having to reinstall valet to try reproducing it. Linked PR changes the default value which fully fixes the openssl issue. |
This pr is meant to overcome an issue in concerning Chrome v58 and up.
The tests I've conducted are:
Test the default setting
$ valet unparkexpireInshould go to default.$ valet secure <my_laravel_project>Test with a too high
expireIn$ valet unpark$ valet secure --expireIn=730 <my_laravel_project>net::ERR_CERT_VALIDITY_TOO_LONGTest with a lower
expireIn$ valet unparkexpireIn,$ valet secure --expireIn=120 <my_laravel_project>Extra test is done by checking Mac's Keychain Access for default option, 368 days counting from December 13 2021
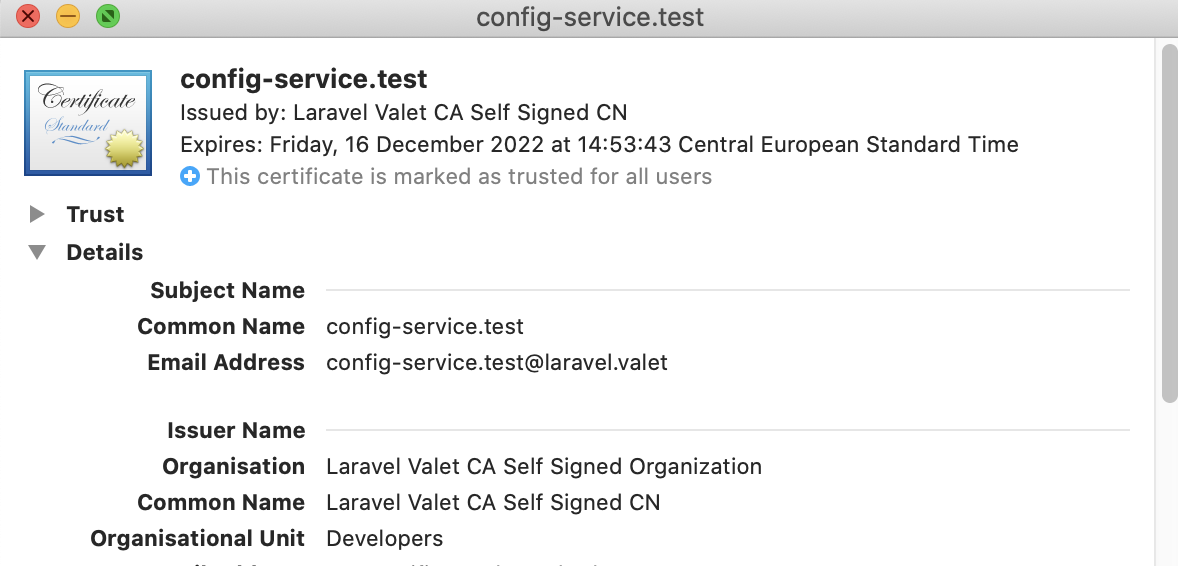
The expireIn option that can be passed to
$ valet secure <domain> --expireIn=<nDays>can be used to overcome the aforementioned issue.