You can check my blog series out on this here!
The System Call Integrity Layer (SCIL) is designed to be a subsystem within the Kernel which allows an EDR from Userland to hook System Calls via Alt Syscalls. The EDR can mark which processes are to be hooked, and can designate only particular System Service Numbers to hook.
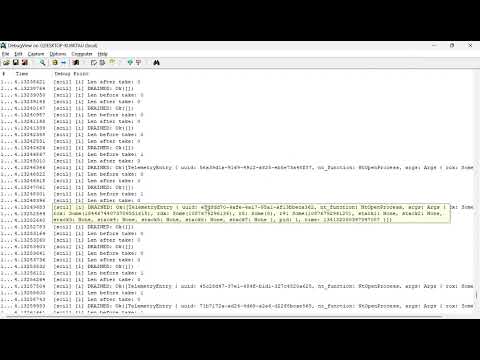
Video demo of logging syscalls (YouTube):
Architecturally the ideal secure solution to this would look as follows:
The SCIL subsystem then has two main functions when it is in motion:
- Log system calls and parameters (this is essentially a similar feed to Events Tracing for Windows: Threat Intelligence).
- For processes / system calls which require deep inspection:
- Suspend the system call temporarily via a synchronisation object.
- Communicate with the userland EDR application (EDR no longer in the kernel for this) notifying of a Pending Syscall Object (PSO). I haven't yet designed exactly what PSOs will contain / point to.
- The user-mode EDR application can then do EDR things it would ordinarily do in ntdll etc before allowing a syscall to dispatch.
- If the EDR ok's it, signal back to the SCIL subsystem to release the synchronisation object, which allows the syscall to continue dispatching.
The subsystem in practice would also need short-circuits in the event the EDR user-land handler of the malfunctioning / taking too long. Any such cases can then still have telemetry ingest to the EDR via point 1 above with the signal emission. This process in practice would look as follows (for this I am not using VBS):