-
Notifications
You must be signed in to change notification settings - Fork 6.7k
fix(deps): update dependency torch to v2.6.0 [security] #13309
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
fix(deps): update dependency torch to v2.6.0 [security] #13309
Conversation
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Hello @renovate-bot, I'm Gemini Code Assist1! I'm currently reviewing this pull request and will post my feedback shortly. In the meantime, here's a summary to help you and other reviewers quickly get up to speed!
Summary of Changes
This pull request updates the torch dependency from version 2.2.0 to 2.6.0 in the pyproject.toml file. This update is classified as a security update, addressing CVE-2025-32434, a Remote Command Execution (RCE) vulnerability. The PR was automatically generated by Mend Renovate.
Highlights
- Dependency Update: Updates the
torchdependency from version 2.2.0 to 2.6.0. - Security Fix: Addresses CVE-2025-32434, a Remote Command Execution vulnerability in
torch.
Changelog
- people-and-planet-ai/weather-forecasting/serving/weather-model/pyproject.toml
- Updates
torchdependency from 2.2.0 to 2.6.0 to address a security vulnerability.
- Updates
Using Gemini Code Assist
The full guide for Gemini Code Assist can be found on our documentation page, here are some quick tips.
Invoking Gemini
You can request assistance from Gemini at any point in your pull request via creating an issue comment (i.e. comment on the pull request page) using either /gemini <command> or @gemini-code-assist <command>. Below is a summary of the supported commands.
| Feature | Command | Description |
|---|---|---|
| Code Review | /gemini review |
Performs a code review for the current pull request in its current state. |
| Pull Request Summary | /gemini summary |
Provides a summary of the current pull request in its current state. |
| Comment | @gemini-code-assist | Responds in comments when explicitly tagged, both in issue comments and review comments. |
| Help | /gemini help |
Displays a list of available commands. |
Customization
To customize Gemini Code Assist for GitHub experience, repository maintainers can create a configuration file and/or provide a custom code review style guide (such as PEP-8 for Python) by creating and adding files to a .gemini/ folder in the base of the repository. Detailed instructions can be found here.
Limitations & Feedback
Gemini Code Assist is currently in preview and may make mistakes. Please leave feedback on any instances where its feedback is incorrect or counter productive. You can react with 👍 and 👎 on @gemini-code-assist comments to provide feedback.
You can also get AI-powered code generation, chat, as well as code reviews directly in the IDE at no cost with the Gemini Code Assist IDE Extension.
A
torchupdate's call,
Stops RCE for all.
New version's bright,
Securing the night,
No commands remotely install.
Footnotes
-
Review the Privacy Notices, Generative AI Prohibited Use Policy, Terms of Service, and learn how to configure Gemini Code Assist in GitHub here. Gemini can make mistakes, so double check it and use code with caution. ↩
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Code Review
This PR updates the torch dependency from version 2.2.0 to 2.6.0, addressing a security vulnerability (CVE-2025-32434) that allows for Remote Command Execution (RCE) even when using torch.load with weights_only=True. The update is reflected in the pyproject.toml file. This is a critical update due to the security implications.
Summary of Findings
- Security Vulnerability: The PR addresses a critical security vulnerability (CVE-2025-32434) in the
torchlibrary, which could lead to Remote Command Execution (RCE). This vulnerability exists even when usingtorch.loadwithweights_only=True, which was previously considered a safe mitigation. - Dependency Update: The
torchdependency is updated from version 2.2.0 to 2.6.0 in thepyproject.tomlfile. This update is crucial to mitigate the identified security vulnerability. - Notebook Consistency: The comment in
pyproject.tomlreminds to ensure thetorchversion matches thecontainer_uriinnotebooks/3-training.ipynb. It's important to verify this consistency to avoid potential compatibility issues.
Merge Readiness
The pull request addresses a critical security vulnerability and updates the torch dependency accordingly. Given the severity of the vulnerability, it is highly recommended to merge this PR as soon as possible after verifying the consistency of the torch version across the project, especially in the notebooks/3-training.ipynb file. I am unable to directly approve this pull request, and strongly recommend that others review and approve this code before merging. The security fix warrants immediate attention and deployment.
This PR contains the following updates:
==2.2.0->==2.6.0Warning
Some dependencies could not be looked up. Check the Dependency Dashboard for more information.
GitHub Vulnerability Alerts
CVE-2025-32434
Description
I found a Remote Command Execution (RCE) vulnerability in the PyTorch. When load model using torch.load with weights_only=True, it can still achieve RCE.
Background knowledge
https://github.com/pytorch/pytorch/security
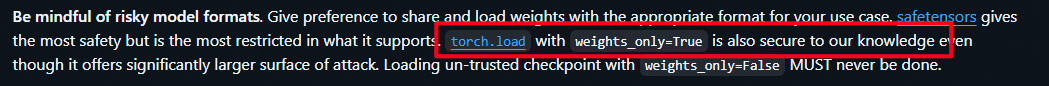
As you can see, the PyTorch official documentation considers using
torch.load()withweights_only=Trueto be safe.Since everyone knows that weights_only=False is unsafe, so they will use the weights_only=True to mitigate the security issue.
But now, I just proved that even if you use weights_only=True, it still can achieve RCE.
So it is time to update your PyTorch version~.
Credit
This vulnerability was found by Ji'an Zhou.
Configuration
📅 Schedule: Branch creation - At any time (no schedule defined), Automerge - At any time (no schedule defined).
🚦 Automerge: Disabled by config. Please merge this manually once you are satisfied.
♻ Rebasing: Never, or you tick the rebase/retry checkbox.
🔕 Ignore: Close this PR and you won't be reminded about this update again.
This PR was generated by Mend Renovate. View the repository job log.