The tool was used for a blind SQL injection vulnerability. The application uses a tracking cookie for analytics, and performs an SQL query containing the value of the submitted cookie.
The results of the SQL query are not returned, and the application does not respond any differently based on whether the query returns any rows. If the SQL query causes an error, then the application returns a custom error message.
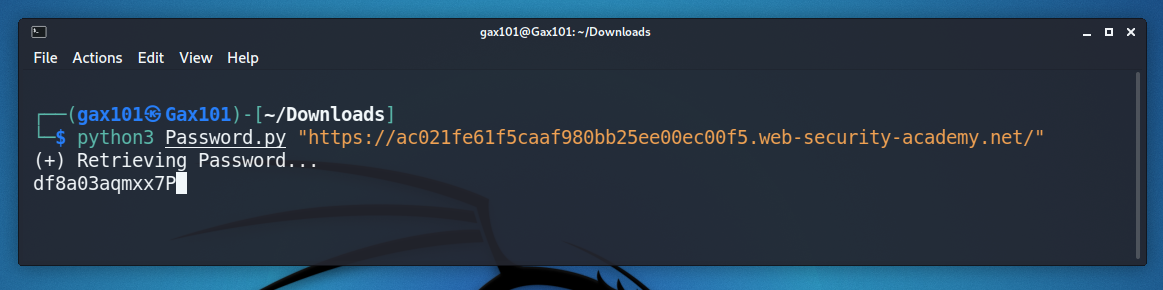
The tool Brute-force multiple requests trying all the alphanumeric characters based on the ascii table. when any charicter matches the first letter of the password it moves on to checkes the secound charcter and so on until the full password is identified.
-
Setup your burpsuite proxy to
127.0.0.1:8080 -
Write the SQLi query and paste it in the
sqli_payloadparamenter
for i in range(1,21): # Lenght of the password
for j in range(32,126): # ascii character in decimal
sqli_payload = " Paste Here " % (i,j)- Paste the value of all the cookies in the
cookies_sqliparamenter
cookies_sqli = {'TrackingId': 'Paste Here' + sqli_payload_encoded, 'session': 'Paste Here'}Use this command to run the python tool you just setup:
Python3 File-Name.py "Vulnerable URL"
| Screenshot |
|---|
 |