-
Notifications
You must be signed in to change notification settings - Fork 2.8k
fix(http-logger): explicitly read the req body in rewrite phase #7891
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
 spacewander
left a comment
spacewander
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Personally, I don't like this change. It will force Nginx to read unused body, even from an untrusted client.
Maybe we can add it as a case "request body is missing" in the doc: https://github.com/apache/apisix/blob/master/docs/en/latest/plugins/http-logger.md#attributes
|
@spacewander |
|
If the authentication plugin goes ahead and Nginx reads the body, it should be available in the logger, unless the body is too big or proxy_request_buffering is disabled. It is not a good idea to force reading an unused body just because the logger needs it. |
|
hi , @spacewander oh yes, I see what you mean. |
If you always need to read the body in your scenario, you can try the |
|
@tzssangglass Is it more unfriendly to control through lua_need_request_body command |
|
From the perspective of the logger plugin only, include_req_body = true. |
I was thinking maybe we could try |
|
Copy that. I'll try. Is there any better plan @tzssangglass |
No more idea for now, let's hear from others. |
 spacewander
left a comment
spacewander
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I don't think it needs to be fixed.
The log code should avoid changing the behavior of the normal code.
When event A happens, we can log event A down. But we can't say because we want to log event A, so event A should happen.
There are many situations that
Not every situation needs to be "fixed" |
|
This pull request has been marked as stale due to 60 days of inactivity. It will be closed in 4 weeks if no further activity occurs. If you think that's incorrect or this pull request should instead be reviewed, please simply write any comment. Even if closed, you can still revive the PR at any time or discuss it on the dev@apisix.apache.org list. Thank you for your contributions. |
|
This pull request/issue has been closed due to lack of activity. If you think that is incorrect, or the pull request requires review, you can revive the PR at any time. |
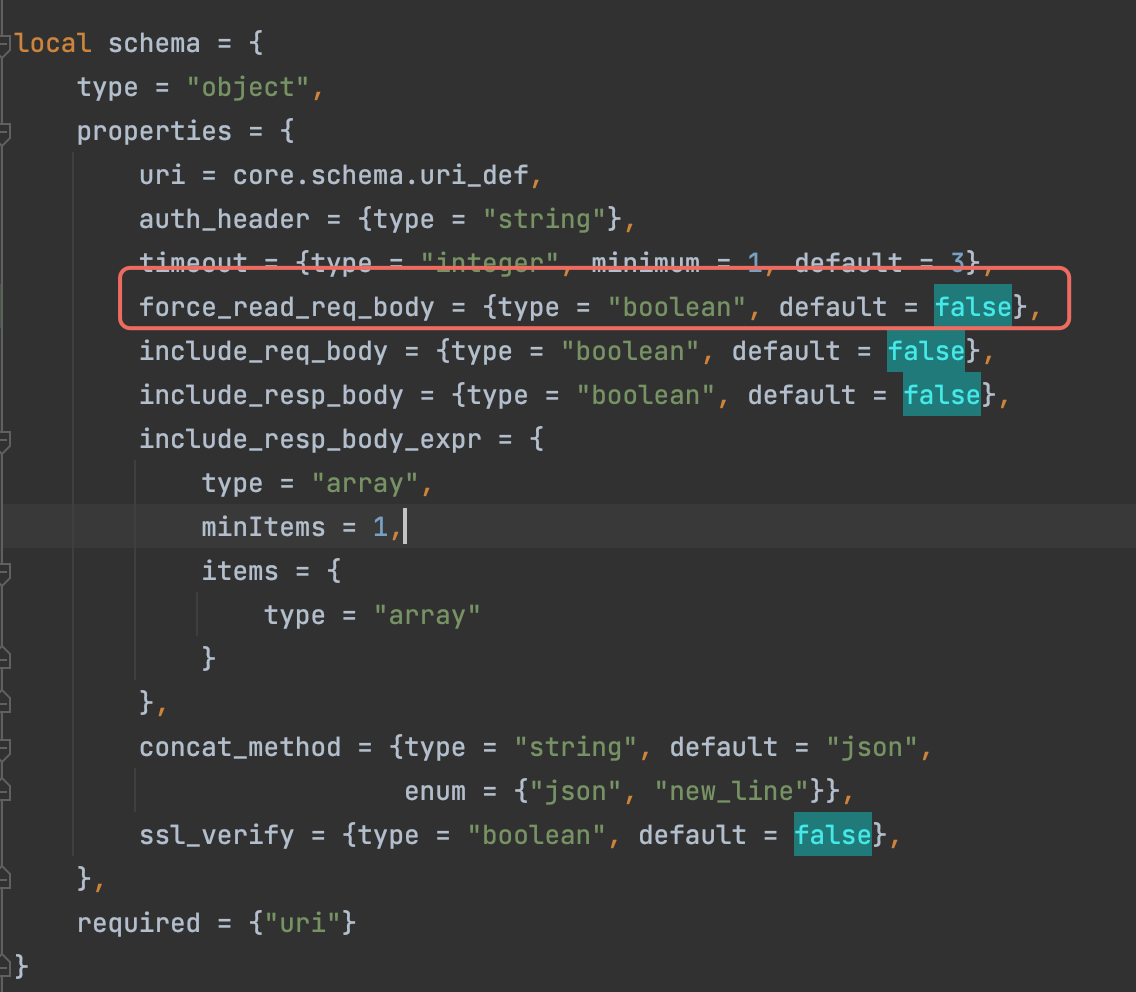
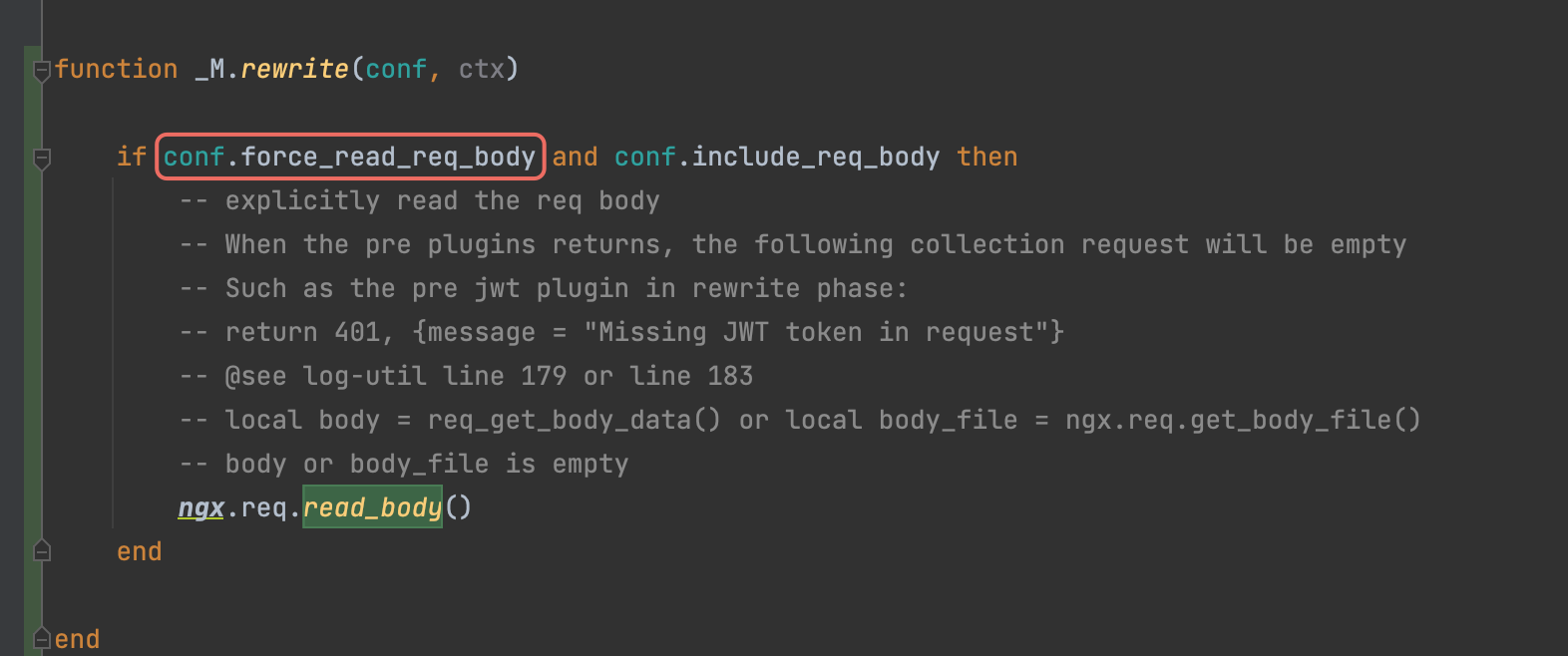
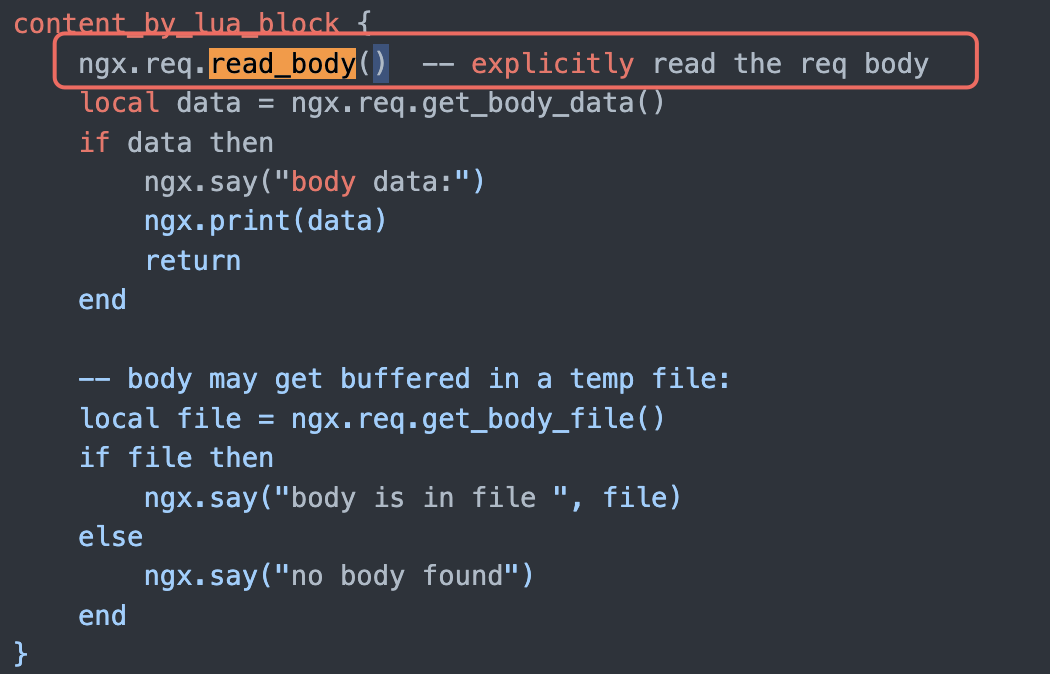
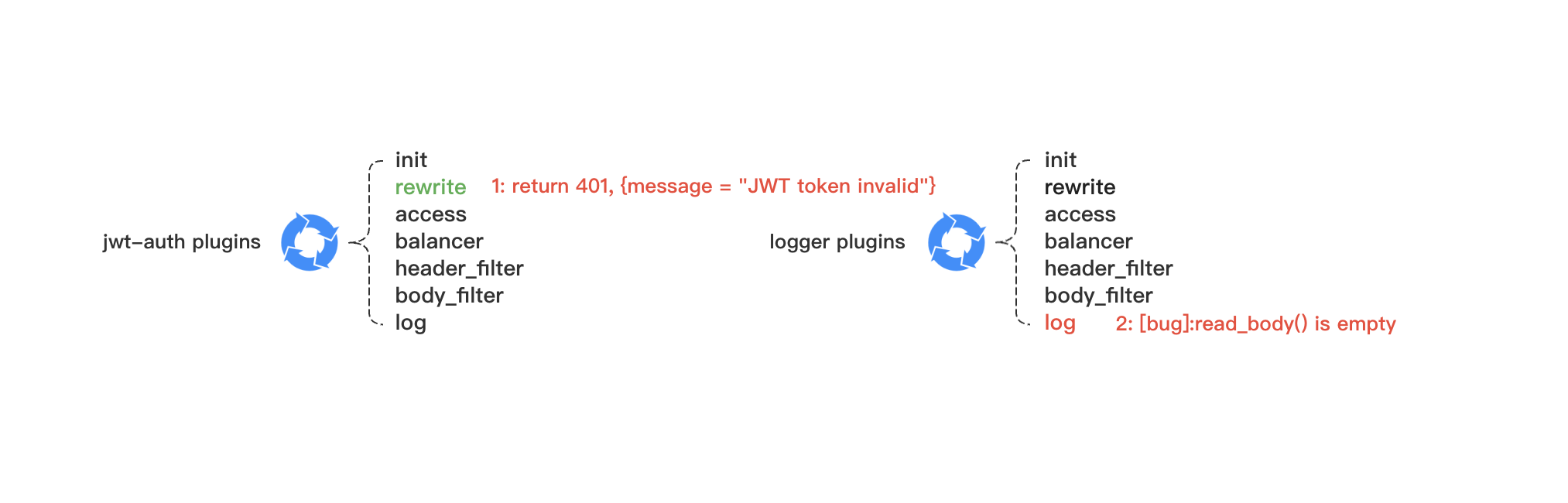
Description
Explicitly read the req body:
When the pre plugins returns, the following collection request will be empty
Such as the pre jwt plugin in rewrite phase:
return 401, {message = "Missing JWT token in request"}@see log-util line 179 or line 183
local body = req_get_body_data() or local body_file = ngx.req.get_body_file()body or body_file is empty
如果使用了前置jwt-plugin或者其他自定义的鉴权插件,使用如下的退出
return 401, {message = "Missing JWT token in request"}会导致在log阶段调用 log-util 179行 或者 183行读取请求体为空
local body = req_get_body_data() or local body_file = ngx.req.get_body_file()Fixes #7890
Checklist