HDDS-5193. change to use getShortUserName instead of getUsername#2343
HDDS-5193. change to use getShortUserName instead of getUsername#2343pakapoj-tul wants to merge 6 commits intoapache:masterfrom
Conversation
…e we'd like to leverage `auth_to_local` property translate identities between pakapoj_tul@DEV.TAP(auth:KERB) and pakapoj_tul(auth:TOKEN) when create file from spark cluster mode.
| * */ | ||
| private List<OzoneAcl> getAclList() { | ||
| return OzoneAclUtil.getAclList(ugi.getUserName(), ugi.getGroupNames(), | ||
| return OzoneAclUtil.getAclList(ugi.getShortUserName(), ugi.getGroupNames(), |
There was a problem hiding this comment.
Thanks @pakapoj-tul for reporting the issue and the detailed investigation report. The current change can't fully address the token user problem.
The token ugi from the client side may not have the proper short user name. For example: you have a token for user
alice@EXAMPLE.COM but the local OS user is bob, ugi.getSHortUserName() will give you bob instead of alice.
After the token is validated on the server side secret manager, the RPC server will recreate a token UGI that has the proper user name as alice@EXAMPLE.COM.
So I think we should move the user/owner ACL from client to server side upon Volume/Bucket/Key request processing.
There was a problem hiding this comment.
Hi @xiaoyuyao , thank for the reply, I was unable to response earlier due to the workload.
yeah, I think the id should be from the server side also. donno the process earlier :) let me check then.
There was a problem hiding this comment.
Hi @xiaoyuyao as i checked the ACLs assignment was happened here and where ACLs was given from the client side so just wanna confirm with you first that we ignore this and build a new one from userInfo?
Request payload.txt
Another question is where should I call the getRemoteUser()?, I try to called it in here but it failed tho.
There was a problem hiding this comment.
Hi, seem to be very odd if the ACL was set using authenticated user ugi.
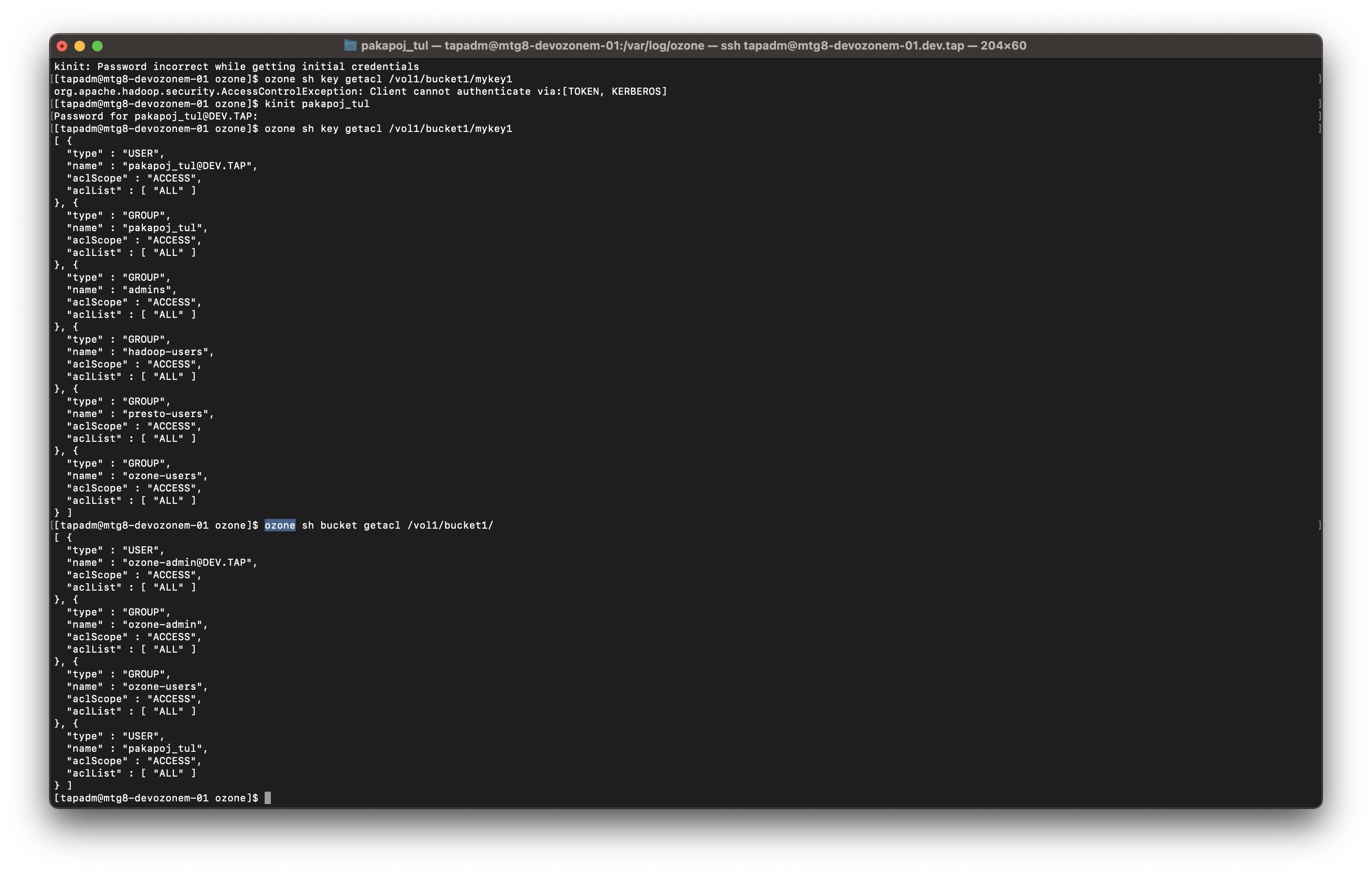
My thoughts was if we have data_pipeline user as a writer who write data to /vol1/bucket1/mykey and data_sci as a reader who read data at /vol1/bucket1/mykey , we have to reassign /vol1/bucket1/mykey acl = /vol1/bucket1/ anyway…
There was a problem hiding this comment.
Ref to the case above, user can't to inherit the acl to the children so I think we should inherit the acl
What’s the meaning of aclscope ACCESS and DEFAULT tho?
enum OzoneAclScope {
ACCESS = 0;
DEFAULT = 1;
}
b/c it filter only DEFAULT acl from what I see here
| RequestContext context) throws OMException { | ||
| String[] userGroups = context.getClientUgi().getGroupNames(); | ||
| String userName = context.getClientUgi().getUserName(); | ||
| String userName = context.getClientUgi().getShortUserName(); |
There was a problem hiding this comment.
In the failed acceptance test, acls were added with the Full principle name (links.robot line 45-49) so changing the compare here with shortName will mismatch and fail.
------------------------------------------------------------------------------
Can follow link with read access | FAIL |
‘PERMISSION_DENIED User testuser2/scm@EXAMPLE.COM doesn’t have READ permission to access volume 04714-target null null’ does not contain ‘key-in-readable-bucket’
------------------------------------------------------------------------------
There was a problem hiding this comment.
note for reproduce the test case
cd compose/ozonesecure
docker-compose up -d
docker-compose --scale datanode=3
docker-compose exec scm bash
robot smoketest/basic/links.robot
… it should be resolved from the server side
…manager, not related to scope of change
|
hey @pakapoj-tul ~ would you mind rebasing this PR with the latest master branch? Some links referenced from your comments seemed to mismatch with the current master branch codes~ (Tried to follow up with your above comments & found that) Thanks! |
|
As the user name related part of this PR is already included in #2466 and we have recent progress on that one, and also because the rest of the patch should not be pulled in (see below) I would suggest to close this PR for now. On the ACL inheritance: |
HDDS-5193. change to use getShortUserName instead of getUsername
What changes were proposed in this pull request?
IMHO, in kerberized cluster identity
pakapoj_tul@DEV.TAPandpakapoj_tulare equal so I propose to usegetShortUsername()instead ofgetShortUsername()from UGI interface when assign and/or compare any ACLs. To leverage auth_to_local property to translate any identity fromauth:KERBEROSto plain username which should be consistent with identity fromauth:TOKENWhat is the link to the Apache JIRA
https://issues.apache.org/jira/browse/HDDS-5193
Please replace this section with the link to the Apache JIRA)
How was this patch tested?
I manually tested on my ozone cluster, bare metal deployment. there are following tests
also test by running spark application in cluster mode
given