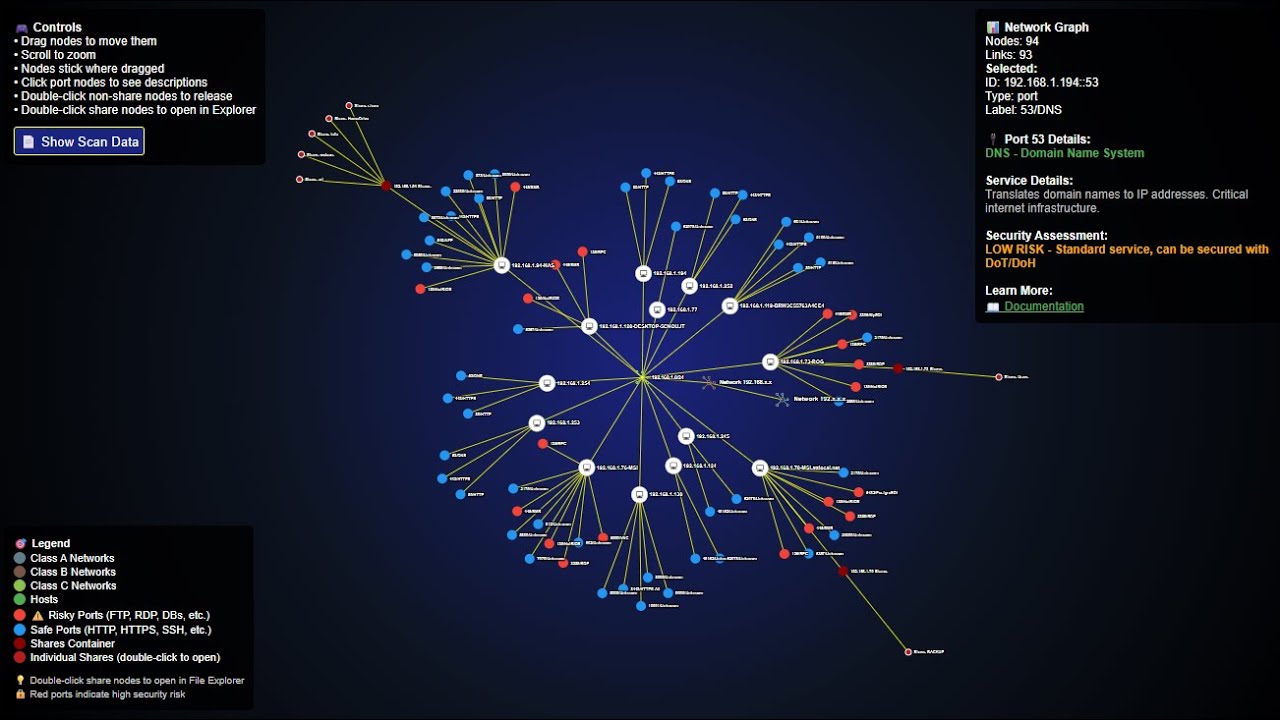
Advanced Network Topology Scanner with Interactive D3.js Visualization
Network Vector is a powerful, Python-based network scanning tool that performs comprehensive TCP port discovery without relying on external tools like nmap or masscan. It creates beautiful, interactive D3.js visualizations to map network topology and security posture.
Click the image above to watch Network Vector scanning and visualizing enterprise networks
- Raw TCP Port Scanning - Scans 750 unique ports without external dependencies
- Multi-threaded Performance - Up to 1000 concurrent threads for fast scanning
- Randomized Scanning - Randomizes IP and port scan order to evade detection patterns
- Stealth Mode - Optional random delays between hosts for IDS evasion
- Network Topology Discovery - Automatic CIDR-based network hierarchy visualization
- Interactive D3.js Graphs - Professional force-directed network visualizations
- SMB Share Enumeration - Cross-platform Windows/Linux share discovery
- Hostname Resolution - Automatic reverse DNS lookup for discovered hosts
- Comprehensive OS Detection - Advanced fingerprinting using 100+ port signatures
- Host Categorization - Visual host coloring based on detected operating systems
- Professional Network Icons - SVG-based network topology representation
- Host Icons - PNG icons with embedded base64 encoding for self-contained HTML
- Color-coded Security - Risk-based port classification (red=dangerous, blue=safe)
- Interactive Port Information - Double-click ports for detailed descriptions and security assessments
- Sticky Node Behavior - Drag-and-drop node positioning with persistence
- Collapsible UI Panels - Hide/show Controls, Info Panel, and Legend to maximize graph space
- Collapse/Expand - Right-click network nodes to manage complexity
- Self-contained Output - HTML files with embedded assets, no external dependencies
- Embedded Scan Data - Complete scan results embedded in HTML with "Show Scan Data" button
- CSV Data Export - Download comprehensive scan data as CSV for analysis in Excel/databases
- Comprehensive Database - Detailed information for 130+ common services
- Security Assessment - Risk levels and vulnerability information for each port
- Educational Links - Direct links to service documentation and security resources
- Service Detection - Automatic identification of running services
- Real-time Display - Interactive port information on double-click
- Python 3.8 or higher (for source code)
- Windows, Linux, or macOS
- OR use the pre-built executable (no Python required!)
# Clone the repository
git clone https://github.com/artofscripting/networkvector.git
cd networkvector
# Download the latest executable from Releases tab on GitHub
# Or build it yourself using the instructions below
# Run immediately with no setup required
./nvector.exe 192.168.1.0/24
# All features included: 1000 threads, embedded data, interactive visualizationNote: Pre-built executables are available in the Releases section of this repository.
# Clone the repository
git clone https://github.com/artofscripting/networkvector.git
cd networkvector
# Install dependencies (none required - uses only Python standard library!)
# Run a basic scan (uses 1000 threads by default for maximum speed)
python src/nvector.py 192.168.1.1
# Scan entire network with full features
python src/nvector.py 192.168.1.0/24 --resolve-hostnames --enumerate-shares
# Use the pre-built executable (no Python required!)
./nvector.exe 192.168.1.0/24# Install PyInstaller
pip install pyinstaller
# Navigate to source directory
cd src
# Build standalone executable with all dependencies
pyinstaller --onefile --add-data "custom_d3_graph.py;." --hidden-import=webbrowser --name="nvector" nvector.py
# Run the executable
./dist/nvector.exe 192.168.1.0/24Pre-built Executable Available: A ready-to-use nvector.exe is included in the repository for immediate use without Python installation.
# Scan a single host (uses 1000 threads by default)
python src/nvector.py 192.168.1.100
# Or use the pre-built executable
./nvector.exe 192.168.1.100
# Scan a network range
python src/nvector.py 192.168.1.0/24# Full feature scan with hostname resolution and SMB enumeration (default 1000 threads)
python src/nvector.py 192.168.1.0/24 --resolve-hostnames --enumerate-shares
# Reduce threads for stealth scanning
python src/nvector.py 192.168.1.0/24 --threads 50
# Stealth mode with randomized scanning and delays
python src/nvector.py 192.168.1.0/24 --scan-delay 1.0 --threads 50
# Disable randomization for fastest scanning
python src/nvector.py 192.168.1.0/24 --no-randomize
# Custom port range
python src/nvector.py 192.168.1.1 --ports 22 80 443 3389 5432
# Custom timeout for slow networks
python src/nvector.py 192.168.1.0/24 --timeout 2.0
# Maximum stealth scanning
python src/nvector.py 192.168.1.0/24 --scan-delay 2.0 --threads 20 --timeout 1.5
# Maximum performance with executable
./nvector.exe 192.168.1.0/24 --threads 1000 --no-randomize# Skip graph generation and export to CSV instead
python src/nvector.py 192.168.1.0/24 --no-graph
# Disable specific features
python src/nvector.py 192.168.1.0/24 --no-resolve-hostnames --no-enumerate-shares| Option | Description | Default |
|---|---|---|
target |
IP address or network (e.g., 192.168.1.1 or 192.168.1.0/24) | Required |
--timeout |
Connection timeout in seconds | 0.5 |
--threads |
Maximum number of scanning threads | 1000 |
--ports |
Custom ports to scan | 750 common ports |
--no-graph |
Skip D3.js visualization generation and export to CSV | Enabled |
--no-resolve-hostnames |
Disable reverse DNS lookup | Enabled |
--no-enumerate-shares |
Disable SMB share enumeration | Enabled |
--no-randomize |
Disable randomized scanning order | Randomization enabled |
--scan-delay |
Max random delay between hosts (seconds) for stealth | 0.0 |
Network Vector includes advanced stealth features to evade network security detection:
# Default behavior - randomizes host and port order
python src/nvector.py 192.168.1.0/24
# Disable randomization for fastest performance
python src/nvector.py 192.168.1.0/24 --no-randomizeBenefits:
- ✅ Evades predictable scan pattern detection
- ✅ Reduces IDS/IPS signature matching
- ✅ Makes traffic analysis more difficult
- ✅ No performance impact on scan speed
# Add random delays up to 1 second between hosts
python src/nvector.py 192.168.1.0/24 --scan-delay 1.0
# Maximum stealth configuration
python src/nvector.py 192.168.1.0/24 --scan-delay 2.0 --threads 20 --timeout 1.5Stealth Features:
- 🎯 Random Host Order - Scans hosts in unpredictable sequence
- 🎲 Random Port Order - Randomizes port scanning sequence per host
- ⏰ Variable Timing - Random delays between hosts (0 to
--scan-delayseconds) - 🔄 Thread Limiting - Reduces concurrent connections for lower footprint
| Technique | Purpose | Command Example |
|---|---|---|
| Randomized Order | Avoid pattern detection | --scan-delay 0.0 (default) |
| Slow Scanning | Evade rate-based detection | --scan-delay 2.0 --threads 50 |
| Low Profile | Minimize concurrent connections | --threads 10 --timeout 2.0 |
| Targeted Scanning | Reduce noise with specific ports | --ports 80 443 22 |
Network Vector generates a single, self-contained HTML file with:
- Force-directed network graph with D3.js v7
- Professional network topology representation with SVG icons
- Interactive port information with security details for 875+ ports
- Collapsible UI controls - Hide/show panels with keyboard shortcuts (Alt+C, Alt+I, Alt+L)
- CSV data export - Download complete scan data for spreadsheet analysis
- Embedded scan data - complete analysis data built into the HTML file
- Show Scan Data button - view raw scan results without separate JSON files
- Responsive design for desktop and mobile viewing
- Timestamped filename for historical tracking (e.g.,
network_scan_20251106_141532.html) - No external dependencies - works offline with all assets embedded
When using --no-graph, Network Vector automatically exports results to CSV:
- Automatic Generation - CSV file created immediately after scan completion
- Comprehensive Data - All scan results, host details, and metadata included
- Timestamped Files - Format:
network_scan_YYYYMMDD_HHMMSS.csv - Ready for Analysis - Compatible with Excel, Google Sheets, databases
- No Manual Export - Eliminates need for manual CSV download from HTML
- Drag-and-drop nodes with sticky positioning
- Right-click collapse/expand for network organization
- Double-click port details with security assessments
- Color-coded risk levels (red for dangerous, blue for safe ports)
- Network hierarchy visualization with CIDR-based topology
- CSV data export - Complete scan data export with:
- Separate rows for ports and SMB shares (no mixing)
- Host details (IP, hostname, response times)
- Port information (port number, service name) in dedicated rows
- SMB shares in their own dedicated rows
- OS detection results
- Scan metadata and configuration
- Timestamped filenames for historical analysis
- Pure Python Implementation - No external scanning tools required
- Socket-based Scanning - Raw TCP connection attempts
- Multi-threaded Design - Concurrent scanning for performance
- Modular Structure - Separate scanning and visualization components
Network Vector scans 998 unique ports covering:
- System Services (1-1024): SSH, HTTP, HTTPS, FTP, Telnet, etc.
- Database Ports (1433, 3306, 5432, etc.): SQL Server, MySQL, PostgreSQL
- Application Services (8080, 9000, etc.): Web applications and APIs
- Development Ports (3000-4000): Node.js, Rails, Django applications
- Enterprise Services (389, 636, etc.): LDAP, Active Directory
- D3.js v7 - Latest version for maximum compatibility
- Force-directed Layout - Automatic node positioning with physics simulation
- SVG Rendering - Scalable vector graphics for crisp visuals
- Base64 Embedding - Self-contained HTML with no external dependencies
- Educational Purpose - Designed for learning network security concepts
- Authorized Testing Only - Only scan networks you own or have permission to test
- Responsible Disclosure - Report vulnerabilities through proper channels
Network Vector performs basic TCP scanning which may be detected by:
- Intrusion Detection Systems (IDS)
- Firewall logs
- Network monitoring tools
For stealth scanning, consider:
- Reducing thread count (
--threads 1-10) - Increasing timeout values (
--timeout 2.0) - Scanning during low-traffic periods
We welcome contributions! Please see our contributing guidelines:
- Fork the repository
- Create a feature branch (
git checkout -b feature/amazing-feature) - Commit your changes (
git commit -m 'Add amazing feature') - Push to the branch (
git push origin feature/amazing-feature) - Open a Pull Request
# Clone your fork
git clone https://github.com/yourusername/networkvector.git
cd networkvector
# Create development branch
git checkout -b feature/your-feature
# Make changes and test
python src/nvector.py 127.0.0.1 --threads 10This project is licensed under the MIT License - see the LICENSE file for details.
- D3.js Community - For the incredible visualization framework
- Python Community - For the robust standard library that makes this possible
- Network Security Community - For inspiration and best practices
- Open Source Contributors - For making tools like this possible
- Issues: GitHub Issues
- Discussions: GitHub Discussions
- Documentation: Project Wiki
Network Vector - Mapping networks, visualizing security, empowering defenders.
Made with ❤️ by the ArtOfScripting community