-
Notifications
You must be signed in to change notification settings - Fork 603
[Rule Tuning] Ensure host information is in endpoint rule queries #2593
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[Rule Tuning] Ensure host information is in endpoint rule queries #2593
Conversation
…tform # Conflicts: # rules/windows/collection_posh_clipboard_capture.toml # rules/windows/collection_posh_mailbox.toml # rules/windows/credential_access_lsass_memdump_file_created.toml # rules/windows/credential_access_shadow_credentials.toml # rules/windows/credential_access_wireless_creds_dumping.toml # rules/windows/defense_evasion_amsi_bypass_dllhijack.toml # rules/windows/defense_evasion_amsi_bypass_powershell.toml # rules/windows/defense_evasion_disable_posh_scriptblocklogging.toml # rules/windows/defense_evasion_network_connection_from_windows_binary.toml # rules/windows/discovery_files_dir_systeminfo_via_cmd.toml # rules/windows/execution_suspicious_psexesvc.toml
|
Pending @w0rk3r datasources review and the weird parsing error, this is ready for review |
|
@w0rk3r can you also add |
|
@brokensound77 I think we should modify the index |
That makes sense to me, for those targeting the |
|
Thanks for adding the sample logs @w0rk3r! |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
- I modified a rule and ran pytest which successfully caught the missing field.
Pytest Output
(detection_dev) ➜ detection-rules git:(2286-add-os-and-platform) ✗ pytest
======================================================================================================================================================================================================================================================================= test session starts =======================================================================================================================================================================================================================================================================
platform darwin -- Python 3.10.9, pytest-7.1.2, pluggy-1.0.0
rootdir: /Users/stryker/workspace/Community/brokensound77/detection-rules, configfile: pyproject.toml
plugins: typeguard-2.13.3, profiling-1.7.0
collected 118 items
tests/test_all_rules.py ..................s..........F [ 25%]
tests/test_gh_workflows.py . [ 26%]
tests/test_mappings.py ... [ 28%]
tests/test_packages.py ..... [ 33%]
tests/test_schemas.py .......... [ 41%]
tests/test_toml_formatter.py ... [ 44%]
tests/test_utils.py .... [ 47%]
tests/test_version_locking.py . [ 48%]
tests/kuery/test_dsl.py ....... [ 54%]
tests/kuery/test_eql2kql.py ......... [ 61%]
tests/kuery/test_evaluator.py ............. [ 72%]
tests/kuery/test_kql2eql.py .......... [ 81%]
tests/kuery/test_lint.py ............ [ 91%]
tests/kuery/test_parser.py .......... [100%]
============================================================================================================================================================================================================================================================================ FAILURES =============================================================================================================================================================================================================================================================================
_________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________ TestEndpointQuery.test_os_and_platform_in_query _________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________
self = <tests.test_all_rules.TestEndpointQuery testMethod=test_os_and_platform_in_query>
def test_os_and_platform_in_query(self):
"""Test that all endpoint rules have an os defined and linux includes platform."""
for rule in self.production_rules:
if not rule.contents.data.get('language') in ('eql', 'kuery'):
continue
if rule.path.parent.name not in ('windows', 'macos', 'linux'):
# skip cross-platform for now
continue
ast = rule.contents.data.ast
fields = [str(f) for f in ast if isinstance(f, (kql.ast.Field, eql.ast.Field))]
err_msg = f'{self.rule_str(rule)} missing required field for endpoint rule'
> self.assertIn('host.os.type', fields, err_msg)
E AssertionError: 'host.os.type' not found in ['event.action', 'process.name', 'process.Ext.effective_parent.name', 'process.Ext.effective_parent.executable'] : 1dee0500-4aeb-44ca-b24b-4a285d7b6ba1 - Suspicious Inter-Process Communication via Outlook -> missing required field for endpoint rule
tests/test_all_rules.py:836: AssertionError
===================================================================================================================================================================================================================================================================== short test summary info =====================================================================================================================================================================================================================================================================
FAILED tests/test_all_rules.py::TestEndpointQuery::test_os_and_platform_in_query - AssertionError: 'host.os.type' not found in ['event.action', 'process.name', 'process.Ext.effective_parent.name', 'process.Ext.effective_parent.executable'] : 1dee0500-4aeb-44ca-b24b-4a285d7b6ba1 - Suspicious Inter-Process Communication via Outlook -> missing required field for endpoint rule
============================================================================================================================================================================================================================================================ 1 failed, 116 passed, 1 skipped in 43.96s ============================================================================================================================================================================================================================================================
(detection_dev) ➜ detection-rules git:(2286-add-os-and-platform) ✗
- I saw a task item in the original issue to
verify consistency of all these fields across data sources, but I don't see mention of that in this PR. Is there more to do? - Still need to discuss adding the
host.os.platformfield to linux rules but here is some initial feedback.
| # skip cross-platform for now | ||
| continue |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Is there any reason why we can't add the new field to the cross-platform rules?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
There is a bit more inconsistency in how these rules are written. So, while we could use their tags to choose which type to enforce, the problem is a bit more complex, especially for sequence rules.
If a sequence rule is multi datasource, we will not have absolute knowledge of where to enforce the specific host check within the respective events, making it difficult to unit test.
There are few enough that I think we are safe to ignore those for now
Go to the description of this PR and expand all the individual @w0rk3r did an awesome job analyzing all the unique datasources used in our endpoint rules
I am going to open a dedicated issue for this to ensure it gets the proper discussion |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
LGTM!
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Left some suggestions around unintended replacements, duplicated logic, and missing bumps on updated_date
| severity = "medium" | ||
| tags = ["Elastic", "Elastic Endgame", "Host", "Linux", "Threat Detection", "Credential Access"] | ||
| timestamp_override = "event.ingested" | ||
| type = "eql" |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Missing updated_date bump
rules/windows/command_and_control_certutil_network_connection.toml
Outdated
Show resolved
Hide resolved
rules/windows/command_and_control_certutil_network_connection.toml
Outdated
Show resolved
Hide resolved
rules/windows/persistence_evasion_registry_startup_shell_folder_modified.toml
Outdated
Show resolved
Hide resolved
rules/windows/persistence_priv_escalation_via_accessibility_features.toml
Outdated
Show resolved
Hide resolved
Co-authored-by: Jonhnathan <26856693+w0rk3r@users.noreply.github.com>
Co-authored-by: Jonhnathan <26856693+w0rk3r@users.noreply.github.com>
…hildless.toml Co-authored-by: Jonhnathan <26856693+w0rk3r@users.noreply.github.com>
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Just some bumps on updated_date and I think we are ready to go
| severity = "high" | ||
| tags = ["Elastic", "Host", "Windows", "Threat Detection", "Credential Access", "Investigation Guide"] | ||
| timestamp_override = "event.ingested" | ||
| type = "eql" |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Missing bump on updated_date
| severity = "medium" | ||
| tags = ["Elastic", "Host", "Windows", "Threat Detection", "Discovery", "Investigation Guide"] | ||
| timestamp_override = "event.ingested" | ||
| type = "eql" |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Missing bump on updated_date
| "Elastic Endgame", | ||
| ] | ||
| timestamp_override = "event.ingested" | ||
| type = "eql" |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Missing bump on updated_date
| rule_id = "83e9c2b3-24ef-4c1d-a8cd-5ebafb5dfa2f" | ||
| severity = "low" | ||
| tags = ["Elastic", "Host", "Linux", "Threat Detection", "Defense Evasion"] | ||
| timestamp_override = "event.ingested" |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Missing bump on updated_date
Thanks! Just verified all the dates in them reflect 22 Feb 23, which was the original bump date in this PR, so should be g2g |
) * add unit tests to ensure host type and platform are included * add host.os.name 'linux' to all linux rules * add host.os.name macos to mac rules * add host.os.name to windows rules; fix linux dates * update from host.os.name to host.os.type Co-authored-by: brokensound77 <brokensound77@users.noreply.github.com> Co-authored-by: Jonhnathan <26856693+w0rk3r@users.noreply.github.com> Removed changes from: - rules/linux/command_and_control_connection_attempt_by_non_ssh_root_session.toml - rules/linux/command_and_control_linux_iodine_activity.toml - rules/linux/command_and_control_tunneling_via_earthworm.toml - rules/linux/credential_access_bruteforce_password_guessing.toml - rules/linux/credential_access_collection_sensitive_files.toml - rules/linux/credential_access_credential_dumping.toml - rules/linux/credential_access_potential_linux_ssh_bruteforce.toml - rules/linux/credential_access_potential_linux_ssh_bruteforce_root.toml - rules/linux/credential_access_ssh_backdoor_log.toml - rules/linux/defense_evasion_attempt_to_disable_iptables_or_firewall.toml - rules/linux/defense_evasion_attempt_to_disable_syslog_service.toml - rules/linux/defense_evasion_base16_or_base32_encoding_or_decoding_activity.toml - rules/linux/defense_evasion_chattr_immutable_file.toml - rules/linux/defense_evasion_disable_selinux_attempt.toml - rules/linux/defense_evasion_file_deletion_via_shred.toml - rules/linux/defense_evasion_file_mod_writable_dir.toml - rules/linux/defense_evasion_hidden_file_dir_tmp.toml - rules/linux/defense_evasion_hidden_shared_object.toml - rules/linux/defense_evasion_kernel_module_removal.toml - rules/linux/defense_evasion_log_files_deleted.toml - rules/linux/discovery_kernel_module_enumeration.toml - rules/linux/discovery_linux_hping_activity.toml - rules/linux/discovery_linux_nping_activity.toml - rules/linux/discovery_virtual_machine_fingerprinting.toml - rules/linux/execution_abnormal_process_id_file_created.toml - rules/linux/execution_file_transfer_or_listener_established_via_netcat.toml - rules/linux/execution_perl_tty_shell.toml - rules/linux/execution_process_started_from_process_id_file.toml - rules/linux/execution_process_started_in_shared_memory_directory.toml - rules/linux/execution_python_tty_shell.toml - rules/linux/execution_reverse_shell_via_named_pipe.toml - rules/linux/execution_shell_evasion_linux_binary.toml - rules/linux/execution_tc_bpf_filter.toml - rules/linux/impact_process_kill_threshold.toml - rules/linux/lateral_movement_telnet_network_activity_external.toml - rules/linux/lateral_movement_telnet_network_activity_internal.toml - rules/linux/persistence_chkconfig_service_add.toml - rules/linux/persistence_credential_access_modify_ssh_binaries.toml - rules/linux/persistence_dynamic_linker_backup.toml - rules/linux/persistence_etc_file_creation.toml - rules/linux/persistence_insmod_kernel_module_load.toml - rules/linux/persistence_kde_autostart_modification.toml - rules/linux/persistence_shell_activity_by_web_server.toml - rules/linux/privilege_escalation_ld_preload_shared_object_modif.toml - rules/linux/privilege_escalation_pkexec_envar_hijack.toml - rules/linux/privilege_escalation_shadow_file_read.toml - rules/linux/privilege_escalation_unshare_namesapce_manipulation.toml - rules/macos/credential_access_access_to_browser_credentials_procargs.toml - rules/macos/credential_access_credentials_keychains.toml - rules/macos/credential_access_dumping_hashes_bi_cmds.toml - rules/macos/credential_access_dumping_keychain_security.toml - rules/macos/credential_access_kerberosdump_kcc.toml - rules/macos/credential_access_keychain_pwd_retrieval_security_cmd.toml - rules/macos/credential_access_mitm_localhost_webproxy.toml - rules/macos/credential_access_potential_macos_ssh_bruteforce.toml - rules/macos/credential_access_promt_for_pwd_via_osascript.toml - rules/macos/credential_access_systemkey_dumping.toml - rules/macos/defense_evasion_apple_softupdates_modification.toml - rules/macos/defense_evasion_attempt_del_quarantine_attrib.toml - rules/macos/defense_evasion_attempt_to_disable_gatekeeper.toml - rules/macos/defense_evasion_install_root_certificate.toml - rules/macos/defense_evasion_modify_environment_launchctl.toml - rules/macos/defense_evasion_privacy_controls_tcc_database_modification.toml - rules/macos/defense_evasion_privilege_escalation_privacy_pref_sshd_fulldiskaccess.toml - rules/macos/defense_evasion_safari_config_change.toml - rules/macos/defense_evasion_sandboxed_office_app_suspicious_zip_file.toml - rules/macos/defense_evasion_tcc_bypass_mounted_apfs_access.toml - rules/macos/defense_evasion_unload_endpointsecurity_kext.toml - rules/macos/discovery_users_domain_built_in_commands.toml - rules/macos/execution_defense_evasion_electron_app_childproc_node_js.toml - rules/macos/execution_initial_access_suspicious_browser_childproc.toml - rules/macos/execution_installer_package_spawned_network_event.toml - rules/macos/execution_script_via_automator_workflows.toml - rules/macos/execution_scripting_osascript_exec_followed_by_netcon.toml - rules/macos/execution_shell_execution_via_apple_scripting.toml - rules/macos/initial_access_suspicious_mac_ms_office_child_process.toml - rules/macos/lateral_movement_credential_access_kerberos_bifrostconsole.toml - rules/macos/lateral_movement_mounting_smb_share.toml - rules/macos/lateral_movement_remote_ssh_login_enabled.toml - rules/macos/lateral_movement_vpn_connection_attempt.toml - rules/macos/persistence_account_creation_hide_at_logon.toml - rules/macos/persistence_creation_change_launch_agents_file.toml - rules/macos/persistence_creation_hidden_login_item_osascript.toml - rules/macos/persistence_creation_modif_launch_deamon_sequence.toml - rules/macos/persistence_credential_access_authorization_plugin_creation.toml - rules/macos/persistence_crontab_creation.toml - rules/macos/persistence_defense_evasion_hidden_launch_agent_deamon_logonitem_process.toml - rules/macos/persistence_directory_services_plugins_modification.toml - rules/macos/persistence_docker_shortcuts_plist_modification.toml - rules/macos/persistence_emond_rules_file_creation.toml - rules/macos/persistence_emond_rules_process_execution.toml - rules/macos/persistence_enable_root_account.toml - rules/macos/persistence_evasion_hidden_launch_agent_deamon_creation.toml - rules/macos/persistence_finder_sync_plugin_pluginkit.toml - rules/macos/persistence_folder_action_scripts_runtime.toml - rules/macos/persistence_login_logout_hooks_defaults.toml - rules/macos/persistence_loginwindow_plist_modification.toml - rules/macos/persistence_modification_sublime_app_plugin_or_script.toml - rules/macos/persistence_periodic_tasks_file_mdofiy.toml - rules/macos/persistence_screensaver_engine_unexpected_child_process.toml - rules/macos/persistence_screensaver_plist_file_modification.toml - rules/macos/persistence_suspicious_calendar_modification.toml - rules/macos/persistence_via_atom_init_file_modification.toml - rules/macos/privilege_escalation_applescript_with_admin_privs.toml - rules/macos/privilege_escalation_explicit_creds_via_scripting.toml - rules/macos/privilege_escalation_exploit_adobe_acrobat_updater.toml - rules/macos/privilege_escalation_local_user_added_to_admin.toml - rules/macos/privilege_escalation_root_crontab_filemod.toml - rules/windows/collection_email_outlook_mailbox_via_com.toml - rules/windows/collection_email_powershell_exchange_mailbox.toml - rules/windows/collection_mailbox_export_winlog.toml - rules/windows/collection_posh_audio_capture.toml - rules/windows/collection_posh_clipboard_capture.toml - rules/windows/collection_posh_keylogger.toml - rules/windows/collection_posh_mailbox.toml - rules/windows/collection_posh_screen_grabber.toml - rules/windows/collection_winrar_encryption.toml - rules/windows/command_and_control_certreq_postdata.toml - rules/windows/command_and_control_certutil_network_connection.toml - rules/windows/command_and_control_common_webservices.toml - rules/windows/command_and_control_dns_tunneling_nslookup.toml - rules/windows/command_and_control_encrypted_channel_freesslcert.toml - rules/windows/command_and_control_iexplore_via_com.toml - rules/windows/command_and_control_ingress_transfer_bits.toml - rules/windows/command_and_control_port_forwarding_added_registry.toml - rules/windows/command_and_control_rdp_tunnel_plink.toml - rules/windows/command_and_control_remote_file_copy_desktopimgdownldr.toml - rules/windows/command_and_control_remote_file_copy_mpcmdrun.toml - rules/windows/command_and_control_remote_file_copy_powershell.toml - rules/windows/command_and_control_remote_file_copy_scripts.toml - rules/windows/command_and_control_sunburst_c2_activity_detected.toml - rules/windows/command_and_control_teamviewer_remote_file_copy.toml - rules/windows/credential_access_bruteforce_admin_account.toml - rules/windows/credential_access_bruteforce_multiple_logon_failure_followed_by_success.toml - rules/windows/credential_access_bruteforce_multiple_logon_failure_same_srcip.toml - rules/windows/credential_access_cmdline_dump_tool.toml - rules/windows/credential_access_copy_ntds_sam_volshadowcp_cmdline.toml - rules/windows/credential_access_credential_dumping_msbuild.toml - rules/windows/credential_access_dcsync_newterm_subjectuser.toml - rules/windows/credential_access_dcsync_replication_rights.toml - rules/windows/credential_access_disable_kerberos_preauth.toml - rules/windows/credential_access_domain_backup_dpapi_private_keys.toml - rules/windows/credential_access_dump_registry_hives.toml - rules/windows/credential_access_generic_localdumps.toml - rules/windows/credential_access_iis_apppoolsa_pwd_appcmd.toml - rules/windows/credential_access_iis_connectionstrings_dumping.toml - rules/windows/credential_access_kerberoasting_unusual_process.toml - rules/windows/credential_access_ldap_attributes.toml - rules/windows/credential_access_lsass_handle_via_malseclogon.toml - rules/windows/credential_access_lsass_loaded_susp_dll.toml - rules/windows/credential_access_lsass_memdump_file_created.toml - rules/windows/credential_access_lsass_memdump_handle_access.toml - rules/windows/credential_access_mimikatz_memssp_default_logs.toml - rules/windows/credential_access_mimikatz_powershell_module.toml - rules/windows/credential_access_mod_wdigest_security_provider.toml - rules/windows/credential_access_moving_registry_hive_via_smb.toml - rules/windows/credential_access_persistence_network_logon_provider_modification.toml - rules/windows/credential_access_posh_invoke_ninjacopy.toml - rules/windows/credential_access_posh_minidump.toml - rules/windows/credential_access_posh_request_ticket.toml - rules/windows/credential_access_potential_lsa_memdump_via_mirrordump.toml - rules/windows/credential_access_relay_ntlm_auth_via_http_spoolss.toml - rules/windows/credential_access_remote_sam_secretsdump.toml - rules/windows/credential_access_saved_creds_vault_winlog.toml - rules/windows/credential_access_saved_creds_vaultcmd.toml - rules/windows/credential_access_seenabledelegationprivilege_assigned_to_user.toml - rules/windows/credential_access_shadow_credentials.toml - rules/windows/credential_access_spn_attribute_modified.toml - rules/windows/credential_access_suspicious_comsvcs_imageload.toml - rules/windows/credential_access_suspicious_lsass_access_generic.toml - rules/windows/credential_access_suspicious_lsass_access_memdump.toml - rules/windows/credential_access_suspicious_lsass_access_via_snapshot.toml - rules/windows/credential_access_suspicious_winreg_access_via_sebackup_priv.toml - rules/windows/credential_access_symbolic_link_to_shadow_copy_created.toml - rules/windows/credential_access_via_snapshot_lsass_clone_creation.toml - rules/windows/credential_access_wireless_creds_dumping.toml - rules/windows/defense_evasion_adding_the_hidden_file_attribute_with_via_attribexe.toml - rules/windows/defense_evasion_amsi_bypass_dllhijack.toml - rules/windows/defense_evasion_amsi_bypass_powershell.toml - rules/windows/defense_evasion_amsienable_key_mod.toml - rules/windows/defense_evasion_clearing_windows_console_history.toml - rules/windows/defense_evasion_clearing_windows_event_logs.toml - rules/windows/defense_evasion_clearing_windows_security_logs.toml - rules/windows/defense_evasion_code_signing_policy_modification_builtin_tools.toml - rules/windows/defense_evasion_code_signing_policy_modification_registry.toml - rules/windows/defense_evasion_create_mod_root_certificate.toml - rules/windows/defense_evasion_cve_2020_0601.toml - rules/windows/defense_evasion_defender_disabled_via_registry.toml - rules/windows/defense_evasion_defender_exclusion_via_powershell.toml - rules/windows/defense_evasion_delete_volume_usn_journal_with_fsutil.toml - rules/windows/defense_evasion_disable_posh_scriptblocklogging.toml - rules/windows/defense_evasion_disable_windows_firewall_rules_with_netsh.toml - rules/windows/defense_evasion_disabling_windows_defender_powershell.toml - rules/windows/defense_evasion_disabling_windows_logs.toml - rules/windows/defense_evasion_dns_over_https_enabled.toml - rules/windows/defense_evasion_dotnet_compiler_parent_process.toml - rules/windows/defense_evasion_enable_inbound_rdp_with_netsh.toml - rules/windows/defense_evasion_enable_network_discovery_with_netsh.toml - rules/windows/defense_evasion_execution_control_panel_suspicious_args.toml - rules/windows/defense_evasion_execution_lolbas_wuauclt.toml - rules/windows/defense_evasion_execution_msbuild_started_by_office_app.toml - rules/windows/defense_evasion_execution_msbuild_started_by_script.toml - rules/windows/defense_evasion_execution_msbuild_started_by_system_process.toml - rules/windows/defense_evasion_execution_msbuild_started_renamed.toml - rules/windows/defense_evasion_execution_msbuild_started_unusal_process.toml - rules/windows/defense_evasion_execution_suspicious_explorer_winword.toml - rules/windows/defense_evasion_execution_windefend_unusual_path.toml - rules/windows/defense_evasion_file_creation_mult_extension.toml - rules/windows/defense_evasion_from_unusual_directory.toml - rules/windows/defense_evasion_hide_encoded_executable_registry.toml - rules/windows/defense_evasion_iis_httplogging_disabled.toml - rules/windows/defense_evasion_injection_msbuild.toml - rules/windows/defense_evasion_installutil_beacon.toml - rules/windows/defense_evasion_masquerading_as_elastic_endpoint_process.toml - rules/windows/defense_evasion_masquerading_renamed_autoit.toml - rules/windows/defense_evasion_masquerading_suspicious_werfault_childproc.toml - rules/windows/defense_evasion_masquerading_trusted_directory.toml - rules/windows/defense_evasion_masquerading_werfault.toml - rules/windows/defense_evasion_microsoft_defender_tampering.toml - rules/windows/defense_evasion_misc_lolbin_connecting_to_the_internet.toml - rules/windows/defense_evasion_ms_office_suspicious_regmod.toml - rules/windows/defense_evasion_msbuild_making_network_connections.toml - rules/windows/defense_evasion_mshta_beacon.toml - rules/windows/defense_evasion_msxsl_network.toml - rules/windows/defense_evasion_network_connection_from_windows_binary.toml - rules/windows/defense_evasion_parent_process_pid_spoofing.toml - rules/windows/defense_evasion_persistence_account_tokenfilterpolicy.toml - rules/windows/defense_evasion_posh_assembly_load.toml - rules/windows/defense_evasion_posh_compressed.toml - rules/windows/defense_evasion_posh_encryption.toml - rules/windows/defense_evasion_posh_process_injection.toml - rules/windows/defense_evasion_potential_processherpaderping.toml - rules/windows/defense_evasion_powershell_windows_firewall_disabled.toml - rules/windows/defense_evasion_process_termination_followed_by_deletion.toml - rules/windows/defense_evasion_proxy_execution_via_msdt.toml - rules/windows/defense_evasion_rundll32_no_arguments.toml - rules/windows/defense_evasion_scheduledjobs_at_protocol_enabled.toml - rules/windows/defense_evasion_sdelete_like_filename_rename.toml - rules/windows/defense_evasion_sip_provider_mod.toml - rules/windows/defense_evasion_solarwinds_backdoor_service_disabled_via_registry.toml - rules/windows/defense_evasion_suspicious_certutil_commands.toml - rules/windows/defense_evasion_suspicious_execution_from_mounted_device.toml - rules/windows/defense_evasion_suspicious_managedcode_host_process.toml - rules/windows/defense_evasion_suspicious_process_access_direct_syscall.toml - rules/windows/defense_evasion_suspicious_process_creation_calltrace.toml - rules/windows/defense_evasion_suspicious_scrobj_load.toml - rules/windows/defense_evasion_suspicious_short_program_name.toml - rules/windows/defense_evasion_suspicious_wmi_script.toml - rules/windows/defense_evasion_suspicious_zoom_child_process.toml - rules/windows/defense_evasion_system_critical_proc_abnormal_file_activity.toml - rules/windows/defense_evasion_timestomp_sysmon.toml - rules/windows/defense_evasion_unsigned_dll_loaded_from_suspdir.toml - rules/windows/defense_evasion_untrusted_driver_loaded.toml - rules/windows/defense_evasion_unusual_ads_file_creation.toml - rules/windows/defense_evasion_unusual_dir_ads.toml - rules/windows/defense_evasion_unusual_network_connection_via_dllhost.toml - rules/windows/defense_evasion_unusual_network_connection_via_rundll32.toml - rules/windows/defense_evasion_unusual_process_network_connection.toml - rules/windows/defense_evasion_unusual_system_vp_child_program.toml - rules/windows/defense_evasion_via_filter_manager.toml - rules/windows/defense_evasion_workfolders_control_execution.toml - rules/windows/defense_evasion_wsl_bash_exec.toml - rules/windows/defense_evasion_wsl_child_process.toml - rules/windows/defense_evasion_wsl_enabled_via_dism.toml - rules/windows/defense_evasion_wsl_filesystem.toml - rules/windows/defense_evasion_wsl_kalilinux.toml - rules/windows/defense_evasion_wsl_registry_modification.toml - rules/windows/discovery_adfind_command_activity.toml - rules/windows/discovery_admin_recon.toml - rules/windows/discovery_command_system_account.toml - rules/windows/discovery_enumerating_domain_trusts_via_dsquery.toml - rules/windows/discovery_enumerating_domain_trusts_via_nltest.toml - rules/windows/discovery_files_dir_systeminfo_via_cmd.toml - rules/windows/discovery_group_policy_object_discovery.toml - rules/windows/discovery_net_view.toml - rules/windows/discovery_peripheral_device.toml - rules/windows/discovery_posh_invoke_sharefinder.toml - rules/windows/discovery_posh_suspicious_api_functions.toml - rules/windows/discovery_post_exploitation_external_ip_lookup.toml - rules/windows/discovery_privileged_localgroup_membership.toml - rules/windows/discovery_remote_system_discovery_commands_windows.toml - rules/windows/discovery_security_software_wmic.toml - rules/windows/discovery_system_service_discovery.toml - rules/windows/discovery_system_time_discovery.toml - rules/windows/discovery_whoami_command_activity.toml - rules/windows/execution_apt_solarwinds_backdoor_child_cmd_powershell.toml - rules/windows/execution_apt_solarwinds_backdoor_unusual_child_processes.toml - rules/windows/execution_com_object_xwizard.toml - rules/windows/execution_command_prompt_connecting_to_the_internet.toml - rules/windows/execution_command_shell_started_by_svchost.toml - rules/windows/execution_command_shell_started_by_unusual_process.toml - rules/windows/execution_command_shell_via_rundll32.toml - rules/windows/execution_enumeration_via_wmiprvse.toml - rules/windows/execution_from_unusual_path_cmdline.toml - rules/windows/execution_html_help_executable_program_connecting_to_the_internet.toml - rules/windows/execution_ms_office_written_file.toml - rules/windows/execution_pdf_written_file.toml - rules/windows/execution_posh_hacktool_functions.toml - rules/windows/execution_posh_portable_executable.toml - rules/windows/execution_posh_psreflect.toml - rules/windows/execution_psexec_lateral_movement_command.toml - rules/windows/execution_register_server_program_connecting_to_the_internet.toml - rules/windows/execution_scheduled_task_powershell_source.toml - rules/windows/execution_shared_modules_local_sxs_dll.toml - rules/windows/execution_suspicious_cmd_wmi.toml - rules/windows/execution_suspicious_image_load_wmi_ms_office.toml - rules/windows/execution_suspicious_pdf_reader.toml - rules/windows/execution_suspicious_powershell_imgload.toml - rules/windows/execution_suspicious_psexesvc.toml - rules/windows/execution_via_compiled_html_file.toml - rules/windows/execution_via_hidden_shell_conhost.toml - rules/windows/execution_via_xp_cmdshell_mssql_stored_procedure.toml - rules/windows/impact_backup_file_deletion.toml - rules/windows/impact_deleting_backup_catalogs_with_wbadmin.toml - rules/windows/impact_modification_of_boot_config.toml - rules/windows/impact_stop_process_service_threshold.toml - rules/windows/impact_volume_shadow_copy_deletion_or_resized_via_vssadmin.toml - rules/windows/impact_volume_shadow_copy_deletion_via_powershell.toml - rules/windows/impact_volume_shadow_copy_deletion_via_wmic.toml - rules/windows/initial_access_evasion_suspicious_htm_file_creation.toml - rules/windows/initial_access_script_executing_powershell.toml - rules/windows/initial_access_scripts_process_started_via_wmi.toml - rules/windows/initial_access_suspicious_ms_exchange_files.toml - rules/windows/initial_access_suspicious_ms_exchange_process.toml - rules/windows/initial_access_suspicious_ms_exchange_worker_child_process.toml - rules/windows/initial_access_suspicious_ms_office_child_process.toml - rules/windows/initial_access_suspicious_ms_outlook_child_process.toml - rules/windows/initial_access_unusual_dns_service_children.toml - rules/windows/initial_access_unusual_dns_service_file_writes.toml - rules/windows/initial_access_via_explorer_suspicious_child_parent_args.toml - rules/windows/lateral_movement_cmd_service.toml - rules/windows/lateral_movement_dcom_hta.toml - rules/windows/lateral_movement_dcom_mmc20.toml - rules/windows/lateral_movement_dcom_shellwindow_shellbrowserwindow.toml - rules/windows/lateral_movement_defense_evasion_lanman_nullsessionpipe_modification.toml - rules/windows/lateral_movement_direct_outbound_smb_connection.toml - rules/windows/lateral_movement_dns_server_overflow.toml - rules/windows/lateral_movement_evasion_rdp_shadowing.toml - rules/windows/lateral_movement_executable_tool_transfer_smb.toml - rules/windows/lateral_movement_execution_from_tsclient_mup.toml - rules/windows/lateral_movement_execution_via_file_shares_sequence.toml - rules/windows/lateral_movement_incoming_winrm_shell_execution.toml - rules/windows/lateral_movement_incoming_wmi.toml - rules/windows/lateral_movement_mount_hidden_or_webdav_share_net.toml - rules/windows/lateral_movement_powershell_remoting_target.toml - rules/windows/lateral_movement_rdp_enabled_registry.toml - rules/windows/lateral_movement_rdp_sharprdp_target.toml - rules/windows/lateral_movement_remote_file_copy_hidden_share.toml - rules/windows/lateral_movement_remote_service_installed_winlog.toml - rules/windows/lateral_movement_remote_services.toml - rules/windows/lateral_movement_remote_task_creation_winlog.toml - rules/windows/lateral_movement_scheduled_task_target.toml - rules/windows/lateral_movement_service_control_spawned_script_int.toml - rules/windows/lateral_movement_suspicious_rdp_client_imageload.toml - rules/windows/lateral_movement_via_startup_folder_rdp_smb.toml - rules/windows/persistence_ad_adminsdholder.toml - rules/windows/persistence_adobe_hijack_persistence.toml - rules/windows/persistence_app_compat_shim.toml - rules/windows/persistence_appcertdlls_registry.toml - rules/windows/persistence_appinitdlls_registry.toml - rules/windows/persistence_dontexpirepasswd_account.toml - rules/windows/persistence_driver_newterm_imphash.toml - rules/windows/persistence_evasion_hidden_local_account_creation.toml - rules/windows/persistence_evasion_registry_ifeo_injection.toml - rules/windows/persistence_evasion_registry_startup_shell_folder_modified.toml - rules/windows/persistence_gpo_schtask_service_creation.toml - rules/windows/persistence_local_scheduled_job_creation.toml - rules/windows/persistence_local_scheduled_task_creation.toml - rules/windows/persistence_local_scheduled_task_scripting.toml - rules/windows/persistence_ms_office_addins_file.toml - rules/windows/persistence_ms_outlook_vba_template.toml - rules/windows/persistence_msds_alloweddelegateto_krbtgt.toml - rules/windows/persistence_powershell_exch_mailbox_activesync_add_device.toml - rules/windows/persistence_powersshell_profiles.toml - rules/windows/persistence_priv_escalation_via_accessibility_features.toml - rules/windows/persistence_registry_uncommon.toml - rules/windows/persistence_remote_password_reset.toml - rules/windows/persistence_run_key_and_startup_broad.toml - rules/windows/persistence_runtime_run_key_startup_susp_procs.toml - rules/windows/persistence_scheduled_task_creation_winlog.toml - rules/windows/persistence_scheduled_task_updated.toml - rules/windows/persistence_sdprop_exclusion_dsheuristics.toml - rules/windows/persistence_service_dll_unsigned.toml - rules/windows/persistence_service_windows_service_winlog.toml - rules/windows/persistence_services_registry.toml - rules/windows/persistence_startup_folder_file_written_by_suspicious_process.toml - rules/windows/persistence_startup_folder_file_written_by_unsigned_process.toml - rules/windows/persistence_startup_folder_scripts.toml - rules/windows/persistence_suspicious_com_hijack_registry.toml - rules/windows/persistence_suspicious_image_load_scheduled_task_ms_office.toml - rules/windows/persistence_suspicious_scheduled_task_runtime.toml - rules/windows/persistence_suspicious_service_created_registry.toml - rules/windows/persistence_system_shells_via_services.toml - rules/windows/persistence_temp_scheduled_task.toml - rules/windows/persistence_time_provider_mod.toml - rules/windows/persistence_user_account_added_to_privileged_group_ad.toml - rules/windows/persistence_user_account_creation.toml - rules/windows/persistence_via_application_shimming.toml - rules/windows/persistence_via_bits_job_notify_command.toml - rules/windows/persistence_via_hidden_run_key_valuename.toml - rules/windows/persistence_via_lsa_security_support_provider_registry.toml - rules/windows/persistence_via_telemetrycontroller_scheduledtask_hijack.toml - rules/windows/persistence_via_update_orchestrator_service_hijack.toml - rules/windows/persistence_via_windows_management_instrumentation_event_subscription.toml - rules/windows/persistence_via_wmi_stdregprov_run_services.toml - rules/windows/persistence_webshell_detection.toml - rules/windows/privilege_escalation_create_process_as_different_user.toml - rules/windows/privilege_escalation_credroaming_ldap.toml - rules/windows/privilege_escalation_disable_uac_registry.toml - rules/windows/privilege_escalation_group_policy_iniscript.toml - rules/windows/privilege_escalation_group_policy_privileged_groups.toml - rules/windows/privilege_escalation_group_policy_scheduled_task.toml - rules/windows/privilege_escalation_installertakeover.toml - rules/windows/privilege_escalation_krbrelayup_service_creation.toml - rules/windows/privilege_escalation_lsa_auth_package.toml - rules/windows/privilege_escalation_named_pipe_impersonation.toml - rules/windows/privilege_escalation_persistence_phantom_dll.toml - rules/windows/privilege_escalation_port_monitor_print_pocessor_abuse.toml - rules/windows/privilege_escalation_posh_token_impersonation.toml - rules/windows/privilege_escalation_printspooler_registry_copyfiles.toml - rules/windows/privilege_escalation_printspooler_service_suspicious_file.toml - rules/windows/privilege_escalation_printspooler_suspicious_file_deletion.toml - rules/windows/privilege_escalation_printspooler_suspicious_spl_file.toml - rules/windows/privilege_escalation_rogue_windir_environment_var.toml - rules/windows/privilege_escalation_samaccountname_spoofing_attack.toml - rules/windows/privilege_escalation_suspicious_dnshostname_update.toml - rules/windows/privilege_escalation_tokenmanip_sedebugpriv_enabled.toml - rules/windows/privilege_escalation_uac_bypass_com_clipup.toml - rules/windows/privilege_escalation_uac_bypass_com_ieinstal.toml - rules/windows/privilege_escalation_uac_bypass_com_interface_icmluautil.toml - rules/windows/privilege_escalation_uac_bypass_diskcleanup_hijack.toml - rules/windows/privilege_escalation_uac_bypass_dll_sideloading.toml - rules/windows/privilege_escalation_uac_bypass_event_viewer.toml - rules/windows/privilege_escalation_uac_bypass_mock_windir.toml - rules/windows/privilege_escalation_uac_bypass_winfw_mmc_hijack.toml - rules/windows/privilege_escalation_unusual_parentchild_relationship.toml - rules/windows/privilege_escalation_unusual_printspooler_childprocess.toml - rules/windows/privilege_escalation_unusual_svchost_childproc_childless.toml - rules/windows/privilege_escalation_via_ppid_spoofing.toml - rules/windows/privilege_escalation_via_rogue_named_pipe.toml - rules/windows/privilege_escalation_via_token_theft.toml - rules/windows/privilege_escalation_windows_service_via_unusual_client.toml (selectively cherry picked from commit 59da2da)
) * add unit tests to ensure host type and platform are included * add host.os.name 'linux' to all linux rules * add host.os.name macos to mac rules * add host.os.name to windows rules; fix linux dates * update from host.os.name to host.os.type Co-authored-by: brokensound77 <brokensound77@users.noreply.github.com> Co-authored-by: Jonhnathan <26856693+w0rk3r@users.noreply.github.com> Removed changes from: - rules/linux/command_and_control_connection_attempt_by_non_ssh_root_session.toml - rules/linux/command_and_control_linux_iodine_activity.toml - rules/linux/command_and_control_tunneling_via_earthworm.toml - rules/linux/credential_access_bruteforce_password_guessing.toml - rules/linux/credential_access_collection_sensitive_files.toml - rules/linux/credential_access_credential_dumping.toml - rules/linux/credential_access_potential_linux_ssh_bruteforce.toml - rules/linux/credential_access_potential_linux_ssh_bruteforce_root.toml - rules/linux/credential_access_ssh_backdoor_log.toml - rules/linux/defense_evasion_attempt_to_disable_iptables_or_firewall.toml - rules/linux/defense_evasion_attempt_to_disable_syslog_service.toml - rules/linux/defense_evasion_base16_or_base32_encoding_or_decoding_activity.toml - rules/linux/defense_evasion_chattr_immutable_file.toml - rules/linux/defense_evasion_disable_selinux_attempt.toml - rules/linux/defense_evasion_file_deletion_via_shred.toml - rules/linux/defense_evasion_file_mod_writable_dir.toml - rules/linux/defense_evasion_hidden_file_dir_tmp.toml - rules/linux/defense_evasion_hidden_shared_object.toml - rules/linux/defense_evasion_kernel_module_removal.toml - rules/linux/defense_evasion_log_files_deleted.toml - rules/linux/discovery_kernel_module_enumeration.toml - rules/linux/discovery_linux_hping_activity.toml - rules/linux/discovery_linux_nping_activity.toml - rules/linux/discovery_virtual_machine_fingerprinting.toml - rules/linux/execution_abnormal_process_id_file_created.toml - rules/linux/execution_file_transfer_or_listener_established_via_netcat.toml - rules/linux/execution_perl_tty_shell.toml - rules/linux/execution_process_started_from_process_id_file.toml - rules/linux/execution_process_started_in_shared_memory_directory.toml - rules/linux/execution_python_tty_shell.toml - rules/linux/execution_reverse_shell_via_named_pipe.toml - rules/linux/execution_shell_evasion_linux_binary.toml - rules/linux/execution_tc_bpf_filter.toml - rules/linux/impact_process_kill_threshold.toml - rules/linux/lateral_movement_telnet_network_activity_external.toml - rules/linux/lateral_movement_telnet_network_activity_internal.toml - rules/linux/persistence_chkconfig_service_add.toml - rules/linux/persistence_credential_access_modify_ssh_binaries.toml - rules/linux/persistence_dynamic_linker_backup.toml - rules/linux/persistence_etc_file_creation.toml - rules/linux/persistence_insmod_kernel_module_load.toml - rules/linux/persistence_kde_autostart_modification.toml - rules/linux/persistence_shell_activity_by_web_server.toml - rules/linux/privilege_escalation_ld_preload_shared_object_modif.toml - rules/linux/privilege_escalation_pkexec_envar_hijack.toml - rules/linux/privilege_escalation_shadow_file_read.toml - rules/linux/privilege_escalation_unshare_namesapce_manipulation.toml - rules/macos/credential_access_access_to_browser_credentials_procargs.toml - rules/macos/credential_access_credentials_keychains.toml - rules/macos/credential_access_dumping_hashes_bi_cmds.toml - rules/macos/credential_access_dumping_keychain_security.toml - rules/macos/credential_access_kerberosdump_kcc.toml - rules/macos/credential_access_keychain_pwd_retrieval_security_cmd.toml - rules/macos/credential_access_mitm_localhost_webproxy.toml - rules/macos/credential_access_potential_macos_ssh_bruteforce.toml - rules/macos/credential_access_promt_for_pwd_via_osascript.toml - rules/macos/credential_access_systemkey_dumping.toml - rules/macos/defense_evasion_apple_softupdates_modification.toml - rules/macos/defense_evasion_attempt_del_quarantine_attrib.toml - rules/macos/defense_evasion_attempt_to_disable_gatekeeper.toml - rules/macos/defense_evasion_install_root_certificate.toml - rules/macos/defense_evasion_modify_environment_launchctl.toml - rules/macos/defense_evasion_privacy_controls_tcc_database_modification.toml - rules/macos/defense_evasion_privilege_escalation_privacy_pref_sshd_fulldiskaccess.toml - rules/macos/defense_evasion_safari_config_change.toml - rules/macos/defense_evasion_sandboxed_office_app_suspicious_zip_file.toml - rules/macos/defense_evasion_tcc_bypass_mounted_apfs_access.toml - rules/macos/defense_evasion_unload_endpointsecurity_kext.toml - rules/macos/discovery_users_domain_built_in_commands.toml - rules/macos/execution_defense_evasion_electron_app_childproc_node_js.toml - rules/macos/execution_initial_access_suspicious_browser_childproc.toml - rules/macos/execution_installer_package_spawned_network_event.toml - rules/macos/execution_script_via_automator_workflows.toml - rules/macos/execution_scripting_osascript_exec_followed_by_netcon.toml - rules/macos/execution_shell_execution_via_apple_scripting.toml - rules/macos/initial_access_suspicious_mac_ms_office_child_process.toml - rules/macos/lateral_movement_credential_access_kerberos_bifrostconsole.toml - rules/macos/lateral_movement_mounting_smb_share.toml - rules/macos/lateral_movement_remote_ssh_login_enabled.toml - rules/macos/lateral_movement_vpn_connection_attempt.toml - rules/macos/persistence_account_creation_hide_at_logon.toml - rules/macos/persistence_creation_change_launch_agents_file.toml - rules/macos/persistence_creation_hidden_login_item_osascript.toml - rules/macos/persistence_creation_modif_launch_deamon_sequence.toml - rules/macos/persistence_credential_access_authorization_plugin_creation.toml - rules/macos/persistence_crontab_creation.toml - rules/macos/persistence_defense_evasion_hidden_launch_agent_deamon_logonitem_process.toml - rules/macos/persistence_directory_services_plugins_modification.toml - rules/macos/persistence_docker_shortcuts_plist_modification.toml - rules/macos/persistence_emond_rules_file_creation.toml - rules/macos/persistence_emond_rules_process_execution.toml - rules/macos/persistence_enable_root_account.toml - rules/macos/persistence_evasion_hidden_launch_agent_deamon_creation.toml - rules/macos/persistence_finder_sync_plugin_pluginkit.toml - rules/macos/persistence_folder_action_scripts_runtime.toml - rules/macos/persistence_login_logout_hooks_defaults.toml - rules/macos/persistence_loginwindow_plist_modification.toml - rules/macos/persistence_modification_sublime_app_plugin_or_script.toml - rules/macos/persistence_periodic_tasks_file_mdofiy.toml - rules/macos/persistence_screensaver_engine_unexpected_child_process.toml - rules/macos/persistence_screensaver_plist_file_modification.toml - rules/macos/persistence_suspicious_calendar_modification.toml - rules/macos/persistence_via_atom_init_file_modification.toml - rules/macos/privilege_escalation_applescript_with_admin_privs.toml - rules/macos/privilege_escalation_explicit_creds_via_scripting.toml - rules/macos/privilege_escalation_exploit_adobe_acrobat_updater.toml - rules/macos/privilege_escalation_local_user_added_to_admin.toml - rules/macos/privilege_escalation_root_crontab_filemod.toml - rules/windows/collection_email_outlook_mailbox_via_com.toml - rules/windows/collection_email_powershell_exchange_mailbox.toml - rules/windows/collection_mailbox_export_winlog.toml - rules/windows/collection_posh_audio_capture.toml - rules/windows/collection_posh_clipboard_capture.toml - rules/windows/collection_posh_keylogger.toml - rules/windows/collection_posh_mailbox.toml - rules/windows/collection_posh_screen_grabber.toml - rules/windows/collection_winrar_encryption.toml - rules/windows/command_and_control_certreq_postdata.toml - rules/windows/command_and_control_certutil_network_connection.toml - rules/windows/command_and_control_common_webservices.toml - rules/windows/command_and_control_dns_tunneling_nslookup.toml - rules/windows/command_and_control_encrypted_channel_freesslcert.toml - rules/windows/command_and_control_iexplore_via_com.toml - rules/windows/command_and_control_ingress_transfer_bits.toml - rules/windows/command_and_control_port_forwarding_added_registry.toml - rules/windows/command_and_control_rdp_tunnel_plink.toml - rules/windows/command_and_control_remote_file_copy_desktopimgdownldr.toml - rules/windows/command_and_control_remote_file_copy_mpcmdrun.toml - rules/windows/command_and_control_remote_file_copy_powershell.toml - rules/windows/command_and_control_remote_file_copy_scripts.toml - rules/windows/command_and_control_sunburst_c2_activity_detected.toml - rules/windows/command_and_control_teamviewer_remote_file_copy.toml - rules/windows/credential_access_bruteforce_admin_account.toml - rules/windows/credential_access_bruteforce_multiple_logon_failure_followed_by_success.toml - rules/windows/credential_access_bruteforce_multiple_logon_failure_same_srcip.toml - rules/windows/credential_access_cmdline_dump_tool.toml - rules/windows/credential_access_copy_ntds_sam_volshadowcp_cmdline.toml - rules/windows/credential_access_credential_dumping_msbuild.toml - rules/windows/credential_access_dcsync_newterm_subjectuser.toml - rules/windows/credential_access_dcsync_replication_rights.toml - rules/windows/credential_access_disable_kerberos_preauth.toml - rules/windows/credential_access_domain_backup_dpapi_private_keys.toml - rules/windows/credential_access_dump_registry_hives.toml - rules/windows/credential_access_generic_localdumps.toml - rules/windows/credential_access_iis_apppoolsa_pwd_appcmd.toml - rules/windows/credential_access_iis_connectionstrings_dumping.toml - rules/windows/credential_access_kerberoasting_unusual_process.toml - rules/windows/credential_access_ldap_attributes.toml - rules/windows/credential_access_lsass_handle_via_malseclogon.toml - rules/windows/credential_access_lsass_loaded_susp_dll.toml - rules/windows/credential_access_lsass_memdump_file_created.toml - rules/windows/credential_access_lsass_memdump_handle_access.toml - rules/windows/credential_access_mimikatz_memssp_default_logs.toml - rules/windows/credential_access_mimikatz_powershell_module.toml - rules/windows/credential_access_mod_wdigest_security_provider.toml - rules/windows/credential_access_moving_registry_hive_via_smb.toml - rules/windows/credential_access_persistence_network_logon_provider_modification.toml - rules/windows/credential_access_posh_invoke_ninjacopy.toml - rules/windows/credential_access_posh_minidump.toml - rules/windows/credential_access_posh_request_ticket.toml - rules/windows/credential_access_potential_lsa_memdump_via_mirrordump.toml - rules/windows/credential_access_relay_ntlm_auth_via_http_spoolss.toml - rules/windows/credential_access_remote_sam_secretsdump.toml - rules/windows/credential_access_saved_creds_vault_winlog.toml - rules/windows/credential_access_saved_creds_vaultcmd.toml - rules/windows/credential_access_seenabledelegationprivilege_assigned_to_user.toml - rules/windows/credential_access_shadow_credentials.toml - rules/windows/credential_access_spn_attribute_modified.toml - rules/windows/credential_access_suspicious_comsvcs_imageload.toml - rules/windows/credential_access_suspicious_lsass_access_generic.toml - rules/windows/credential_access_suspicious_lsass_access_memdump.toml - rules/windows/credential_access_suspicious_lsass_access_via_snapshot.toml - rules/windows/credential_access_suspicious_winreg_access_via_sebackup_priv.toml - rules/windows/credential_access_symbolic_link_to_shadow_copy_created.toml - rules/windows/credential_access_via_snapshot_lsass_clone_creation.toml - rules/windows/credential_access_wireless_creds_dumping.toml - rules/windows/defense_evasion_adding_the_hidden_file_attribute_with_via_attribexe.toml - rules/windows/defense_evasion_amsi_bypass_dllhijack.toml - rules/windows/defense_evasion_amsi_bypass_powershell.toml - rules/windows/defense_evasion_amsienable_key_mod.toml - rules/windows/defense_evasion_clearing_windows_console_history.toml - rules/windows/defense_evasion_clearing_windows_event_logs.toml - rules/windows/defense_evasion_clearing_windows_security_logs.toml - rules/windows/defense_evasion_code_signing_policy_modification_builtin_tools.toml - rules/windows/defense_evasion_code_signing_policy_modification_registry.toml - rules/windows/defense_evasion_create_mod_root_certificate.toml - rules/windows/defense_evasion_cve_2020_0601.toml - rules/windows/defense_evasion_defender_disabled_via_registry.toml - rules/windows/defense_evasion_defender_exclusion_via_powershell.toml - rules/windows/defense_evasion_delete_volume_usn_journal_with_fsutil.toml - rules/windows/defense_evasion_disable_posh_scriptblocklogging.toml - rules/windows/defense_evasion_disable_windows_firewall_rules_with_netsh.toml - rules/windows/defense_evasion_disabling_windows_defender_powershell.toml - rules/windows/defense_evasion_disabling_windows_logs.toml - rules/windows/defense_evasion_dns_over_https_enabled.toml - rules/windows/defense_evasion_dotnet_compiler_parent_process.toml - rules/windows/defense_evasion_enable_inbound_rdp_with_netsh.toml - rules/windows/defense_evasion_enable_network_discovery_with_netsh.toml - rules/windows/defense_evasion_execution_control_panel_suspicious_args.toml - rules/windows/defense_evasion_execution_lolbas_wuauclt.toml - rules/windows/defense_evasion_execution_msbuild_started_by_office_app.toml - rules/windows/defense_evasion_execution_msbuild_started_by_script.toml - rules/windows/defense_evasion_execution_msbuild_started_by_system_process.toml - rules/windows/defense_evasion_execution_msbuild_started_renamed.toml - rules/windows/defense_evasion_execution_msbuild_started_unusal_process.toml - rules/windows/defense_evasion_execution_suspicious_explorer_winword.toml - rules/windows/defense_evasion_execution_windefend_unusual_path.toml - rules/windows/defense_evasion_file_creation_mult_extension.toml - rules/windows/defense_evasion_from_unusual_directory.toml - rules/windows/defense_evasion_hide_encoded_executable_registry.toml - rules/windows/defense_evasion_iis_httplogging_disabled.toml - rules/windows/defense_evasion_injection_msbuild.toml - rules/windows/defense_evasion_installutil_beacon.toml - rules/windows/defense_evasion_masquerading_as_elastic_endpoint_process.toml - rules/windows/defense_evasion_masquerading_renamed_autoit.toml - rules/windows/defense_evasion_masquerading_suspicious_werfault_childproc.toml - rules/windows/defense_evasion_masquerading_trusted_directory.toml - rules/windows/defense_evasion_masquerading_werfault.toml - rules/windows/defense_evasion_microsoft_defender_tampering.toml - rules/windows/defense_evasion_misc_lolbin_connecting_to_the_internet.toml - rules/windows/defense_evasion_ms_office_suspicious_regmod.toml - rules/windows/defense_evasion_msbuild_making_network_connections.toml - rules/windows/defense_evasion_mshta_beacon.toml - rules/windows/defense_evasion_msxsl_network.toml - rules/windows/defense_evasion_network_connection_from_windows_binary.toml - rules/windows/defense_evasion_parent_process_pid_spoofing.toml - rules/windows/defense_evasion_persistence_account_tokenfilterpolicy.toml - rules/windows/defense_evasion_posh_assembly_load.toml - rules/windows/defense_evasion_posh_compressed.toml - rules/windows/defense_evasion_posh_encryption.toml - rules/windows/defense_evasion_posh_process_injection.toml - rules/windows/defense_evasion_potential_processherpaderping.toml - rules/windows/defense_evasion_powershell_windows_firewall_disabled.toml - rules/windows/defense_evasion_process_termination_followed_by_deletion.toml - rules/windows/defense_evasion_proxy_execution_via_msdt.toml - rules/windows/defense_evasion_rundll32_no_arguments.toml - rules/windows/defense_evasion_scheduledjobs_at_protocol_enabled.toml - rules/windows/defense_evasion_sdelete_like_filename_rename.toml - rules/windows/defense_evasion_sip_provider_mod.toml - rules/windows/defense_evasion_solarwinds_backdoor_service_disabled_via_registry.toml - rules/windows/defense_evasion_suspicious_certutil_commands.toml - rules/windows/defense_evasion_suspicious_execution_from_mounted_device.toml - rules/windows/defense_evasion_suspicious_managedcode_host_process.toml - rules/windows/defense_evasion_suspicious_process_access_direct_syscall.toml - rules/windows/defense_evasion_suspicious_process_creation_calltrace.toml - rules/windows/defense_evasion_suspicious_scrobj_load.toml - rules/windows/defense_evasion_suspicious_short_program_name.toml - rules/windows/defense_evasion_suspicious_wmi_script.toml - rules/windows/defense_evasion_suspicious_zoom_child_process.toml - rules/windows/defense_evasion_system_critical_proc_abnormal_file_activity.toml - rules/windows/defense_evasion_timestomp_sysmon.toml - rules/windows/defense_evasion_unsigned_dll_loaded_from_suspdir.toml - rules/windows/defense_evasion_untrusted_driver_loaded.toml - rules/windows/defense_evasion_unusual_ads_file_creation.toml - rules/windows/defense_evasion_unusual_dir_ads.toml - rules/windows/defense_evasion_unusual_network_connection_via_dllhost.toml - rules/windows/defense_evasion_unusual_network_connection_via_rundll32.toml - rules/windows/defense_evasion_unusual_process_network_connection.toml - rules/windows/defense_evasion_unusual_system_vp_child_program.toml - rules/windows/defense_evasion_via_filter_manager.toml - rules/windows/defense_evasion_workfolders_control_execution.toml - rules/windows/defense_evasion_wsl_bash_exec.toml - rules/windows/defense_evasion_wsl_child_process.toml - rules/windows/defense_evasion_wsl_enabled_via_dism.toml - rules/windows/defense_evasion_wsl_filesystem.toml - rules/windows/defense_evasion_wsl_kalilinux.toml - rules/windows/defense_evasion_wsl_registry_modification.toml - rules/windows/discovery_adfind_command_activity.toml - rules/windows/discovery_admin_recon.toml - rules/windows/discovery_command_system_account.toml - rules/windows/discovery_enumerating_domain_trusts_via_dsquery.toml - rules/windows/discovery_enumerating_domain_trusts_via_nltest.toml - rules/windows/discovery_files_dir_systeminfo_via_cmd.toml - rules/windows/discovery_group_policy_object_discovery.toml - rules/windows/discovery_net_view.toml - rules/windows/discovery_peripheral_device.toml - rules/windows/discovery_posh_invoke_sharefinder.toml - rules/windows/discovery_posh_suspicious_api_functions.toml - rules/windows/discovery_post_exploitation_external_ip_lookup.toml - rules/windows/discovery_privileged_localgroup_membership.toml - rules/windows/discovery_remote_system_discovery_commands_windows.toml - rules/windows/discovery_security_software_wmic.toml - rules/windows/discovery_system_service_discovery.toml - rules/windows/discovery_system_time_discovery.toml - rules/windows/discovery_whoami_command_activity.toml - rules/windows/execution_apt_solarwinds_backdoor_child_cmd_powershell.toml - rules/windows/execution_apt_solarwinds_backdoor_unusual_child_processes.toml - rules/windows/execution_com_object_xwizard.toml - rules/windows/execution_command_prompt_connecting_to_the_internet.toml - rules/windows/execution_command_shell_started_by_svchost.toml - rules/windows/execution_command_shell_started_by_unusual_process.toml - rules/windows/execution_command_shell_via_rundll32.toml - rules/windows/execution_enumeration_via_wmiprvse.toml - rules/windows/execution_from_unusual_path_cmdline.toml - rules/windows/execution_html_help_executable_program_connecting_to_the_internet.toml - rules/windows/execution_ms_office_written_file.toml - rules/windows/execution_pdf_written_file.toml - rules/windows/execution_posh_hacktool_functions.toml - rules/windows/execution_posh_portable_executable.toml - rules/windows/execution_posh_psreflect.toml - rules/windows/execution_psexec_lateral_movement_command.toml - rules/windows/execution_register_server_program_connecting_to_the_internet.toml - rules/windows/execution_scheduled_task_powershell_source.toml - rules/windows/execution_shared_modules_local_sxs_dll.toml - rules/windows/execution_suspicious_cmd_wmi.toml - rules/windows/execution_suspicious_image_load_wmi_ms_office.toml - rules/windows/execution_suspicious_pdf_reader.toml - rules/windows/execution_suspicious_powershell_imgload.toml - rules/windows/execution_suspicious_psexesvc.toml - rules/windows/execution_via_compiled_html_file.toml - rules/windows/execution_via_hidden_shell_conhost.toml - rules/windows/execution_via_xp_cmdshell_mssql_stored_procedure.toml - rules/windows/impact_backup_file_deletion.toml - rules/windows/impact_deleting_backup_catalogs_with_wbadmin.toml - rules/windows/impact_modification_of_boot_config.toml - rules/windows/impact_stop_process_service_threshold.toml - rules/windows/impact_volume_shadow_copy_deletion_or_resized_via_vssadmin.toml - rules/windows/impact_volume_shadow_copy_deletion_via_powershell.toml - rules/windows/impact_volume_shadow_copy_deletion_via_wmic.toml - rules/windows/initial_access_evasion_suspicious_htm_file_creation.toml - rules/windows/initial_access_script_executing_powershell.toml - rules/windows/initial_access_scripts_process_started_via_wmi.toml - rules/windows/initial_access_suspicious_ms_exchange_files.toml - rules/windows/initial_access_suspicious_ms_exchange_process.toml - rules/windows/initial_access_suspicious_ms_exchange_worker_child_process.toml - rules/windows/initial_access_suspicious_ms_office_child_process.toml - rules/windows/initial_access_suspicious_ms_outlook_child_process.toml - rules/windows/initial_access_unusual_dns_service_children.toml - rules/windows/initial_access_unusual_dns_service_file_writes.toml - rules/windows/initial_access_via_explorer_suspicious_child_parent_args.toml - rules/windows/lateral_movement_cmd_service.toml - rules/windows/lateral_movement_dcom_hta.toml - rules/windows/lateral_movement_dcom_mmc20.toml - rules/windows/lateral_movement_dcom_shellwindow_shellbrowserwindow.toml - rules/windows/lateral_movement_defense_evasion_lanman_nullsessionpipe_modification.toml - rules/windows/lateral_movement_direct_outbound_smb_connection.toml - rules/windows/lateral_movement_dns_server_overflow.toml - rules/windows/lateral_movement_evasion_rdp_shadowing.toml - rules/windows/lateral_movement_executable_tool_transfer_smb.toml - rules/windows/lateral_movement_execution_from_tsclient_mup.toml - rules/windows/lateral_movement_execution_via_file_shares_sequence.toml - rules/windows/lateral_movement_incoming_winrm_shell_execution.toml - rules/windows/lateral_movement_incoming_wmi.toml - rules/windows/lateral_movement_mount_hidden_or_webdav_share_net.toml - rules/windows/lateral_movement_powershell_remoting_target.toml - rules/windows/lateral_movement_rdp_enabled_registry.toml - rules/windows/lateral_movement_rdp_sharprdp_target.toml - rules/windows/lateral_movement_remote_file_copy_hidden_share.toml - rules/windows/lateral_movement_remote_service_installed_winlog.toml - rules/windows/lateral_movement_remote_services.toml - rules/windows/lateral_movement_remote_task_creation_winlog.toml - rules/windows/lateral_movement_scheduled_task_target.toml - rules/windows/lateral_movement_service_control_spawned_script_int.toml - rules/windows/lateral_movement_suspicious_rdp_client_imageload.toml - rules/windows/lateral_movement_via_startup_folder_rdp_smb.toml - rules/windows/persistence_ad_adminsdholder.toml - rules/windows/persistence_adobe_hijack_persistence.toml - rules/windows/persistence_app_compat_shim.toml - rules/windows/persistence_appcertdlls_registry.toml - rules/windows/persistence_appinitdlls_registry.toml - rules/windows/persistence_dontexpirepasswd_account.toml - rules/windows/persistence_driver_newterm_imphash.toml - rules/windows/persistence_evasion_hidden_local_account_creation.toml - rules/windows/persistence_evasion_registry_ifeo_injection.toml - rules/windows/persistence_evasion_registry_startup_shell_folder_modified.toml - rules/windows/persistence_gpo_schtask_service_creation.toml - rules/windows/persistence_local_scheduled_job_creation.toml - rules/windows/persistence_local_scheduled_task_creation.toml - rules/windows/persistence_local_scheduled_task_scripting.toml - rules/windows/persistence_ms_office_addins_file.toml - rules/windows/persistence_ms_outlook_vba_template.toml - rules/windows/persistence_msds_alloweddelegateto_krbtgt.toml - rules/windows/persistence_powershell_exch_mailbox_activesync_add_device.toml - rules/windows/persistence_powersshell_profiles.toml - rules/windows/persistence_priv_escalation_via_accessibility_features.toml - rules/windows/persistence_registry_uncommon.toml - rules/windows/persistence_remote_password_reset.toml - rules/windows/persistence_run_key_and_startup_broad.toml - rules/windows/persistence_runtime_run_key_startup_susp_procs.toml - rules/windows/persistence_scheduled_task_creation_winlog.toml - rules/windows/persistence_scheduled_task_updated.toml - rules/windows/persistence_sdprop_exclusion_dsheuristics.toml - rules/windows/persistence_service_dll_unsigned.toml - rules/windows/persistence_service_windows_service_winlog.toml - rules/windows/persistence_services_registry.toml - rules/windows/persistence_startup_folder_file_written_by_suspicious_process.toml - rules/windows/persistence_startup_folder_file_written_by_unsigned_process.toml - rules/windows/persistence_startup_folder_scripts.toml - rules/windows/persistence_suspicious_com_hijack_registry.toml - rules/windows/persistence_suspicious_image_load_scheduled_task_ms_office.toml - rules/windows/persistence_suspicious_scheduled_task_runtime.toml - rules/windows/persistence_suspicious_service_created_registry.toml - rules/windows/persistence_system_shells_via_services.toml - rules/windows/persistence_temp_scheduled_task.toml - rules/windows/persistence_time_provider_mod.toml - rules/windows/persistence_user_account_added_to_privileged_group_ad.toml - rules/windows/persistence_user_account_creation.toml - rules/windows/persistence_via_application_shimming.toml - rules/windows/persistence_via_bits_job_notify_command.toml - rules/windows/persistence_via_hidden_run_key_valuename.toml - rules/windows/persistence_via_lsa_security_support_provider_registry.toml - rules/windows/persistence_via_telemetrycontroller_scheduledtask_hijack.toml - rules/windows/persistence_via_update_orchestrator_service_hijack.toml - rules/windows/persistence_via_windows_management_instrumentation_event_subscription.toml - rules/windows/persistence_via_wmi_stdregprov_run_services.toml - rules/windows/persistence_webshell_detection.toml - rules/windows/privilege_escalation_create_process_as_different_user.toml - rules/windows/privilege_escalation_credroaming_ldap.toml - rules/windows/privilege_escalation_disable_uac_registry.toml - rules/windows/privilege_escalation_group_policy_iniscript.toml - rules/windows/privilege_escalation_group_policy_privileged_groups.toml - rules/windows/privilege_escalation_group_policy_scheduled_task.toml - rules/windows/privilege_escalation_installertakeover.toml - rules/windows/privilege_escalation_krbrelayup_service_creation.toml - rules/windows/privilege_escalation_lsa_auth_package.toml - rules/windows/privilege_escalation_named_pipe_impersonation.toml - rules/windows/privilege_escalation_persistence_phantom_dll.toml - rules/windows/privilege_escalation_port_monitor_print_pocessor_abuse.toml - rules/windows/privilege_escalation_posh_token_impersonation.toml - rules/windows/privilege_escalation_printspooler_registry_copyfiles.toml - rules/windows/privilege_escalation_printspooler_service_suspicious_file.toml - rules/windows/privilege_escalation_printspooler_suspicious_file_deletion.toml - rules/windows/privilege_escalation_printspooler_suspicious_spl_file.toml - rules/windows/privilege_escalation_rogue_windir_environment_var.toml - rules/windows/privilege_escalation_samaccountname_spoofing_attack.toml - rules/windows/privilege_escalation_suspicious_dnshostname_update.toml - rules/windows/privilege_escalation_tokenmanip_sedebugpriv_enabled.toml - rules/windows/privilege_escalation_uac_bypass_com_clipup.toml - rules/windows/privilege_escalation_uac_bypass_com_ieinstal.toml - rules/windows/privilege_escalation_uac_bypass_com_interface_icmluautil.toml - rules/windows/privilege_escalation_uac_bypass_diskcleanup_hijack.toml - rules/windows/privilege_escalation_uac_bypass_dll_sideloading.toml - rules/windows/privilege_escalation_uac_bypass_event_viewer.toml - rules/windows/privilege_escalation_uac_bypass_mock_windir.toml - rules/windows/privilege_escalation_uac_bypass_winfw_mmc_hijack.toml - rules/windows/privilege_escalation_unusual_parentchild_relationship.toml - rules/windows/privilege_escalation_unusual_printspooler_childprocess.toml - rules/windows/privilege_escalation_unusual_svchost_childproc_childless.toml - rules/windows/privilege_escalation_via_ppid_spoofing.toml - rules/windows/privilege_escalation_via_rogue_named_pipe.toml - rules/windows/privilege_escalation_via_token_theft.toml - rules/windows/privilege_escalation_windows_service_via_unusual_client.toml (selectively cherry picked from commit 59da2da)
) * add unit tests to ensure host type and platform are included * add host.os.name 'linux' to all linux rules * add host.os.name macos to mac rules * add host.os.name to windows rules; fix linux dates * update from host.os.name to host.os.type Co-authored-by: brokensound77 <brokensound77@users.noreply.github.com> Co-authored-by: Jonhnathan <26856693+w0rk3r@users.noreply.github.com> Removed changes from: - rules/linux/command_and_control_connection_attempt_by_non_ssh_root_session.toml - rules/linux/command_and_control_linux_iodine_activity.toml - rules/linux/command_and_control_tunneling_via_earthworm.toml - rules/linux/credential_access_bruteforce_password_guessing.toml - rules/linux/credential_access_collection_sensitive_files.toml - rules/linux/credential_access_credential_dumping.toml - rules/linux/credential_access_potential_linux_ssh_bruteforce.toml - rules/linux/credential_access_potential_linux_ssh_bruteforce_root.toml - rules/linux/credential_access_ssh_backdoor_log.toml - rules/linux/defense_evasion_attempt_to_disable_iptables_or_firewall.toml - rules/linux/defense_evasion_attempt_to_disable_syslog_service.toml - rules/linux/defense_evasion_base16_or_base32_encoding_or_decoding_activity.toml - rules/linux/defense_evasion_chattr_immutable_file.toml - rules/linux/defense_evasion_disable_selinux_attempt.toml - rules/linux/defense_evasion_file_deletion_via_shred.toml - rules/linux/defense_evasion_file_mod_writable_dir.toml - rules/linux/defense_evasion_hidden_file_dir_tmp.toml - rules/linux/defense_evasion_hidden_shared_object.toml - rules/linux/defense_evasion_kernel_module_removal.toml - rules/linux/defense_evasion_log_files_deleted.toml - rules/linux/discovery_kernel_module_enumeration.toml - rules/linux/discovery_linux_hping_activity.toml - rules/linux/discovery_linux_nping_activity.toml - rules/linux/discovery_virtual_machine_fingerprinting.toml - rules/linux/execution_abnormal_process_id_file_created.toml - rules/linux/execution_file_transfer_or_listener_established_via_netcat.toml - rules/linux/execution_perl_tty_shell.toml - rules/linux/execution_process_started_from_process_id_file.toml - rules/linux/execution_process_started_in_shared_memory_directory.toml - rules/linux/execution_python_tty_shell.toml - rules/linux/execution_reverse_shell_via_named_pipe.toml - rules/linux/execution_shell_evasion_linux_binary.toml - rules/linux/execution_tc_bpf_filter.toml - rules/linux/impact_process_kill_threshold.toml - rules/linux/lateral_movement_telnet_network_activity_external.toml - rules/linux/lateral_movement_telnet_network_activity_internal.toml - rules/linux/persistence_chkconfig_service_add.toml - rules/linux/persistence_credential_access_modify_ssh_binaries.toml - rules/linux/persistence_dynamic_linker_backup.toml - rules/linux/persistence_etc_file_creation.toml - rules/linux/persistence_insmod_kernel_module_load.toml - rules/linux/persistence_kde_autostart_modification.toml - rules/linux/persistence_shell_activity_by_web_server.toml - rules/linux/privilege_escalation_ld_preload_shared_object_modif.toml - rules/linux/privilege_escalation_pkexec_envar_hijack.toml - rules/linux/privilege_escalation_shadow_file_read.toml - rules/linux/privilege_escalation_unshare_namesapce_manipulation.toml - rules/macos/credential_access_access_to_browser_credentials_procargs.toml - rules/macos/credential_access_credentials_keychains.toml - rules/macos/credential_access_dumping_hashes_bi_cmds.toml - rules/macos/credential_access_dumping_keychain_security.toml - rules/macos/credential_access_kerberosdump_kcc.toml - rules/macos/credential_access_keychain_pwd_retrieval_security_cmd.toml - rules/macos/credential_access_mitm_localhost_webproxy.toml - rules/macos/credential_access_potential_macos_ssh_bruteforce.toml - rules/macos/credential_access_promt_for_pwd_via_osascript.toml - rules/macos/credential_access_systemkey_dumping.toml - rules/macos/defense_evasion_apple_softupdates_modification.toml - rules/macos/defense_evasion_attempt_del_quarantine_attrib.toml - rules/macos/defense_evasion_attempt_to_disable_gatekeeper.toml - rules/macos/defense_evasion_install_root_certificate.toml - rules/macos/defense_evasion_modify_environment_launchctl.toml - rules/macos/defense_evasion_privacy_controls_tcc_database_modification.toml - rules/macos/defense_evasion_privilege_escalation_privacy_pref_sshd_fulldiskaccess.toml - rules/macos/defense_evasion_safari_config_change.toml - rules/macos/defense_evasion_sandboxed_office_app_suspicious_zip_file.toml - rules/macos/defense_evasion_tcc_bypass_mounted_apfs_access.toml - rules/macos/defense_evasion_unload_endpointsecurity_kext.toml - rules/macos/discovery_users_domain_built_in_commands.toml - rules/macos/execution_defense_evasion_electron_app_childproc_node_js.toml - rules/macos/execution_initial_access_suspicious_browser_childproc.toml - rules/macos/execution_installer_package_spawned_network_event.toml - rules/macos/execution_script_via_automator_workflows.toml - rules/macos/execution_scripting_osascript_exec_followed_by_netcon.toml - rules/macos/execution_shell_execution_via_apple_scripting.toml - rules/macos/initial_access_suspicious_mac_ms_office_child_process.toml - rules/macos/lateral_movement_credential_access_kerberos_bifrostconsole.toml - rules/macos/lateral_movement_mounting_smb_share.toml - rules/macos/lateral_movement_remote_ssh_login_enabled.toml - rules/macos/lateral_movement_vpn_connection_attempt.toml - rules/macos/persistence_account_creation_hide_at_logon.toml - rules/macos/persistence_creation_change_launch_agents_file.toml - rules/macos/persistence_creation_hidden_login_item_osascript.toml - rules/macos/persistence_creation_modif_launch_deamon_sequence.toml - rules/macos/persistence_credential_access_authorization_plugin_creation.toml - rules/macos/persistence_crontab_creation.toml - rules/macos/persistence_defense_evasion_hidden_launch_agent_deamon_logonitem_process.toml - rules/macos/persistence_directory_services_plugins_modification.toml - rules/macos/persistence_docker_shortcuts_plist_modification.toml - rules/macos/persistence_emond_rules_file_creation.toml - rules/macos/persistence_emond_rules_process_execution.toml - rules/macos/persistence_enable_root_account.toml - rules/macos/persistence_evasion_hidden_launch_agent_deamon_creation.toml - rules/macos/persistence_finder_sync_plugin_pluginkit.toml - rules/macos/persistence_folder_action_scripts_runtime.toml - rules/macos/persistence_login_logout_hooks_defaults.toml - rules/macos/persistence_loginwindow_plist_modification.toml - rules/macos/persistence_modification_sublime_app_plugin_or_script.toml - rules/macos/persistence_periodic_tasks_file_mdofiy.toml - rules/macos/persistence_screensaver_engine_unexpected_child_process.toml - rules/macos/persistence_screensaver_plist_file_modification.toml - rules/macos/persistence_suspicious_calendar_modification.toml - rules/macos/persistence_via_atom_init_file_modification.toml - rules/macos/privilege_escalation_applescript_with_admin_privs.toml - rules/macos/privilege_escalation_explicit_creds_via_scripting.toml - rules/macos/privilege_escalation_exploit_adobe_acrobat_updater.toml - rules/macos/privilege_escalation_local_user_added_to_admin.toml - rules/macos/privilege_escalation_root_crontab_filemod.toml - rules/windows/collection_email_outlook_mailbox_via_com.toml - rules/windows/collection_email_powershell_exchange_mailbox.toml - rules/windows/collection_mailbox_export_winlog.toml - rules/windows/collection_posh_audio_capture.toml - rules/windows/collection_posh_clipboard_capture.toml - rules/windows/collection_posh_keylogger.toml - rules/windows/collection_posh_mailbox.toml - rules/windows/collection_posh_screen_grabber.toml - rules/windows/collection_winrar_encryption.toml - rules/windows/command_and_control_certreq_postdata.toml - rules/windows/command_and_control_certutil_network_connection.toml - rules/windows/command_and_control_common_webservices.toml - rules/windows/command_and_control_dns_tunneling_nslookup.toml - rules/windows/command_and_control_encrypted_channel_freesslcert.toml - rules/windows/command_and_control_iexplore_via_com.toml - rules/windows/command_and_control_ingress_transfer_bits.toml - rules/windows/command_and_control_port_forwarding_added_registry.toml - rules/windows/command_and_control_rdp_tunnel_plink.toml - rules/windows/command_and_control_remote_file_copy_desktopimgdownldr.toml - rules/windows/command_and_control_remote_file_copy_mpcmdrun.toml - rules/windows/command_and_control_remote_file_copy_powershell.toml - rules/windows/command_and_control_remote_file_copy_scripts.toml - rules/windows/command_and_control_sunburst_c2_activity_detected.toml - rules/windows/command_and_control_teamviewer_remote_file_copy.toml - rules/windows/credential_access_bruteforce_admin_account.toml - rules/windows/credential_access_bruteforce_multiple_logon_failure_followed_by_success.toml - rules/windows/credential_access_bruteforce_multiple_logon_failure_same_srcip.toml - rules/windows/credential_access_cmdline_dump_tool.toml - rules/windows/credential_access_copy_ntds_sam_volshadowcp_cmdline.toml - rules/windows/credential_access_credential_dumping_msbuild.toml - rules/windows/credential_access_dcsync_newterm_subjectuser.toml - rules/windows/credential_access_dcsync_replication_rights.toml - rules/windows/credential_access_disable_kerberos_preauth.toml - rules/windows/credential_access_domain_backup_dpapi_private_keys.toml - rules/windows/credential_access_dump_registry_hives.toml - rules/windows/credential_access_generic_localdumps.toml - rules/windows/credential_access_iis_apppoolsa_pwd_appcmd.toml - rules/windows/credential_access_iis_connectionstrings_dumping.toml - rules/windows/credential_access_kerberoasting_unusual_process.toml - rules/windows/credential_access_ldap_attributes.toml - rules/windows/credential_access_lsass_handle_via_malseclogon.toml - rules/windows/credential_access_lsass_loaded_susp_dll.toml - rules/windows/credential_access_lsass_memdump_file_created.toml - rules/windows/credential_access_lsass_memdump_handle_access.toml - rules/windows/credential_access_mimikatz_memssp_default_logs.toml - rules/windows/credential_access_mimikatz_powershell_module.toml - rules/windows/credential_access_mod_wdigest_security_provider.toml - rules/windows/credential_access_moving_registry_hive_via_smb.toml - rules/windows/credential_access_persistence_network_logon_provider_modification.toml - rules/windows/credential_access_posh_invoke_ninjacopy.toml - rules/windows/credential_access_posh_minidump.toml - rules/windows/credential_access_posh_request_ticket.toml - rules/windows/credential_access_potential_lsa_memdump_via_mirrordump.toml - rules/windows/credential_access_relay_ntlm_auth_via_http_spoolss.toml - rules/windows/credential_access_remote_sam_secretsdump.toml - rules/windows/credential_access_saved_creds_vault_winlog.toml - rules/windows/credential_access_saved_creds_vaultcmd.toml - rules/windows/credential_access_seenabledelegationprivilege_assigned_to_user.toml - rules/windows/credential_access_shadow_credentials.toml - rules/windows/credential_access_spn_attribute_modified.toml - rules/windows/credential_access_suspicious_comsvcs_imageload.toml - rules/windows/credential_access_suspicious_lsass_access_generic.toml - rules/windows/credential_access_suspicious_lsass_access_memdump.toml - rules/windows/credential_access_suspicious_lsass_access_via_snapshot.toml - rules/windows/credential_access_suspicious_winreg_access_via_sebackup_priv.toml - rules/windows/credential_access_symbolic_link_to_shadow_copy_created.toml - rules/windows/credential_access_via_snapshot_lsass_clone_creation.toml - rules/windows/credential_access_wireless_creds_dumping.toml - rules/windows/defense_evasion_adding_the_hidden_file_attribute_with_via_attribexe.toml - rules/windows/defense_evasion_amsi_bypass_dllhijack.toml - rules/windows/defense_evasion_amsi_bypass_powershell.toml - rules/windows/defense_evasion_amsienable_key_mod.toml - rules/windows/defense_evasion_clearing_windows_console_history.toml - rules/windows/defense_evasion_clearing_windows_event_logs.toml - rules/windows/defense_evasion_clearing_windows_security_logs.toml - rules/windows/defense_evasion_code_signing_policy_modification_builtin_tools.toml - rules/windows/defense_evasion_code_signing_policy_modification_registry.toml - rules/windows/defense_evasion_create_mod_root_certificate.toml - rules/windows/defense_evasion_cve_2020_0601.toml - rules/windows/defense_evasion_defender_disabled_via_registry.toml - rules/windows/defense_evasion_defender_exclusion_via_powershell.toml - rules/windows/defense_evasion_delete_volume_usn_journal_with_fsutil.toml - rules/windows/defense_evasion_disable_posh_scriptblocklogging.toml - rules/windows/defense_evasion_disable_windows_firewall_rules_with_netsh.toml - rules/windows/defense_evasion_disabling_windows_defender_powershell.toml - rules/windows/defense_evasion_disabling_windows_logs.toml - rules/windows/defense_evasion_dns_over_https_enabled.toml - rules/windows/defense_evasion_dotnet_compiler_parent_process.toml - rules/windows/defense_evasion_enable_inbound_rdp_with_netsh.toml - rules/windows/defense_evasion_enable_network_discovery_with_netsh.toml - rules/windows/defense_evasion_execution_control_panel_suspicious_args.toml - rules/windows/defense_evasion_execution_lolbas_wuauclt.toml - rules/windows/defense_evasion_execution_msbuild_started_by_office_app.toml - rules/windows/defense_evasion_execution_msbuild_started_by_script.toml - rules/windows/defense_evasion_execution_msbuild_started_by_system_process.toml - rules/windows/defense_evasion_execution_msbuild_started_renamed.toml - rules/windows/defense_evasion_execution_msbuild_started_unusal_process.toml - rules/windows/defense_evasion_execution_suspicious_explorer_winword.toml - rules/windows/defense_evasion_execution_windefend_unusual_path.toml - rules/windows/defense_evasion_file_creation_mult_extension.toml - rules/windows/defense_evasion_from_unusual_directory.toml - rules/windows/defense_evasion_hide_encoded_executable_registry.toml - rules/windows/defense_evasion_iis_httplogging_disabled.toml - rules/windows/defense_evasion_injection_msbuild.toml - rules/windows/defense_evasion_installutil_beacon.toml - rules/windows/defense_evasion_masquerading_as_elastic_endpoint_process.toml - rules/windows/defense_evasion_masquerading_renamed_autoit.toml - rules/windows/defense_evasion_masquerading_suspicious_werfault_childproc.toml - rules/windows/defense_evasion_masquerading_trusted_directory.toml - rules/windows/defense_evasion_masquerading_werfault.toml - rules/windows/defense_evasion_microsoft_defender_tampering.toml - rules/windows/defense_evasion_misc_lolbin_connecting_to_the_internet.toml - rules/windows/defense_evasion_ms_office_suspicious_regmod.toml - rules/windows/defense_evasion_msbuild_making_network_connections.toml - rules/windows/defense_evasion_mshta_beacon.toml - rules/windows/defense_evasion_msxsl_network.toml - rules/windows/defense_evasion_network_connection_from_windows_binary.toml - rules/windows/defense_evasion_parent_process_pid_spoofing.toml - rules/windows/defense_evasion_persistence_account_tokenfilterpolicy.toml - rules/windows/defense_evasion_posh_assembly_load.toml - rules/windows/defense_evasion_posh_compressed.toml - rules/windows/defense_evasion_posh_encryption.toml - rules/windows/defense_evasion_posh_process_injection.toml - rules/windows/defense_evasion_potential_processherpaderping.toml - rules/windows/defense_evasion_powershell_windows_firewall_disabled.toml - rules/windows/defense_evasion_process_termination_followed_by_deletion.toml - rules/windows/defense_evasion_proxy_execution_via_msdt.toml - rules/windows/defense_evasion_rundll32_no_arguments.toml - rules/windows/defense_evasion_scheduledjobs_at_protocol_enabled.toml - rules/windows/defense_evasion_sdelete_like_filename_rename.toml - rules/windows/defense_evasion_sip_provider_mod.toml - rules/windows/defense_evasion_solarwinds_backdoor_service_disabled_via_registry.toml - rules/windows/defense_evasion_suspicious_certutil_commands.toml - rules/windows/defense_evasion_suspicious_execution_from_mounted_device.toml - rules/windows/defense_evasion_suspicious_managedcode_host_process.toml - rules/windows/defense_evasion_suspicious_process_access_direct_syscall.toml - rules/windows/defense_evasion_suspicious_process_creation_calltrace.toml - rules/windows/defense_evasion_suspicious_scrobj_load.toml - rules/windows/defense_evasion_suspicious_short_program_name.toml - rules/windows/defense_evasion_suspicious_wmi_script.toml - rules/windows/defense_evasion_suspicious_zoom_child_process.toml - rules/windows/defense_evasion_system_critical_proc_abnormal_file_activity.toml - rules/windows/defense_evasion_timestomp_sysmon.toml - rules/windows/defense_evasion_unsigned_dll_loaded_from_suspdir.toml - rules/windows/defense_evasion_untrusted_driver_loaded.toml - rules/windows/defense_evasion_unusual_ads_file_creation.toml - rules/windows/defense_evasion_unusual_dir_ads.toml - rules/windows/defense_evasion_unusual_network_connection_via_dllhost.toml - rules/windows/defense_evasion_unusual_network_connection_via_rundll32.toml - rules/windows/defense_evasion_unusual_process_network_connection.toml - rules/windows/defense_evasion_unusual_system_vp_child_program.toml - rules/windows/defense_evasion_via_filter_manager.toml - rules/windows/defense_evasion_workfolders_control_execution.toml - rules/windows/defense_evasion_wsl_bash_exec.toml - rules/windows/defense_evasion_wsl_child_process.toml - rules/windows/defense_evasion_wsl_enabled_via_dism.toml - rules/windows/defense_evasion_wsl_filesystem.toml - rules/windows/defense_evasion_wsl_kalilinux.toml - rules/windows/defense_evasion_wsl_registry_modification.toml - rules/windows/discovery_adfind_command_activity.toml - rules/windows/discovery_admin_recon.toml - rules/windows/discovery_command_system_account.toml - rules/windows/discovery_enumerating_domain_trusts_via_dsquery.toml - rules/windows/discovery_enumerating_domain_trusts_via_nltest.toml - rules/windows/discovery_files_dir_systeminfo_via_cmd.toml - rules/windows/discovery_group_policy_object_discovery.toml - rules/windows/discovery_net_view.toml - rules/windows/discovery_peripheral_device.toml - rules/windows/discovery_posh_invoke_sharefinder.toml - rules/windows/discovery_posh_suspicious_api_functions.toml - rules/windows/discovery_post_exploitation_external_ip_lookup.toml - rules/windows/discovery_privileged_localgroup_membership.toml - rules/windows/discovery_remote_system_discovery_commands_windows.toml - rules/windows/discovery_security_software_wmic.toml - rules/windows/discovery_system_service_discovery.toml - rules/windows/discovery_system_time_discovery.toml - rules/windows/discovery_whoami_command_activity.toml - rules/windows/execution_apt_solarwinds_backdoor_child_cmd_powershell.toml - rules/windows/execution_apt_solarwinds_backdoor_unusual_child_processes.toml - rules/windows/execution_com_object_xwizard.toml - rules/windows/execution_command_prompt_connecting_to_the_internet.toml - rules/windows/execution_command_shell_started_by_svchost.toml - rules/windows/execution_command_shell_started_by_unusual_process.toml - rules/windows/execution_command_shell_via_rundll32.toml - rules/windows/execution_enumeration_via_wmiprvse.toml - rules/windows/execution_from_unusual_path_cmdline.toml - rules/windows/execution_html_help_executable_program_connecting_to_the_internet.toml - rules/windows/execution_ms_office_written_file.toml - rules/windows/execution_pdf_written_file.toml - rules/windows/execution_posh_hacktool_functions.toml - rules/windows/execution_posh_portable_executable.toml - rules/windows/execution_posh_psreflect.toml - rules/windows/execution_psexec_lateral_movement_command.toml - rules/windows/execution_register_server_program_connecting_to_the_internet.toml - rules/windows/execution_scheduled_task_powershell_source.toml - rules/windows/execution_shared_modules_local_sxs_dll.toml - rules/windows/execution_suspicious_cmd_wmi.toml - rules/windows/execution_suspicious_image_load_wmi_ms_office.toml - rules/windows/execution_suspicious_pdf_reader.toml - rules/windows/execution_suspicious_powershell_imgload.toml - rules/windows/execution_suspicious_psexesvc.toml - rules/windows/execution_via_compiled_html_file.toml - rules/windows/execution_via_hidden_shell_conhost.toml - rules/windows/execution_via_xp_cmdshell_mssql_stored_procedure.toml - rules/windows/impact_backup_file_deletion.toml - rules/windows/impact_deleting_backup_catalogs_with_wbadmin.toml - rules/windows/impact_modification_of_boot_config.toml - rules/windows/impact_stop_process_service_threshold.toml - rules/windows/impact_volume_shadow_copy_deletion_or_resized_via_vssadmin.toml - rules/windows/impact_volume_shadow_copy_deletion_via_powershell.toml - rules/windows/impact_volume_shadow_copy_deletion_via_wmic.toml - rules/windows/initial_access_evasion_suspicious_htm_file_creation.toml - rules/windows/initial_access_script_executing_powershell.toml - rules/windows/initial_access_scripts_process_started_via_wmi.toml - rules/windows/initial_access_suspicious_ms_exchange_files.toml - rules/windows/initial_access_suspicious_ms_exchange_process.toml - rules/windows/initial_access_suspicious_ms_exchange_worker_child_process.toml - rules/windows/initial_access_suspicious_ms_office_child_process.toml - rules/windows/initial_access_suspicious_ms_outlook_child_process.toml - rules/windows/initial_access_unusual_dns_service_children.toml - rules/windows/initial_access_unusual_dns_service_file_writes.toml - rules/windows/initial_access_via_explorer_suspicious_child_parent_args.toml - rules/windows/lateral_movement_cmd_service.toml - rules/windows/lateral_movement_dcom_hta.toml - rules/windows/lateral_movement_dcom_mmc20.toml - rules/windows/lateral_movement_dcom_shellwindow_shellbrowserwindow.toml - rules/windows/lateral_movement_defense_evasion_lanman_nullsessionpipe_modification.toml - rules/windows/lateral_movement_direct_outbound_smb_connection.toml - rules/windows/lateral_movement_dns_server_overflow.toml - rules/windows/lateral_movement_evasion_rdp_shadowing.toml - rules/windows/lateral_movement_executable_tool_transfer_smb.toml - rules/windows/lateral_movement_execution_from_tsclient_mup.toml - rules/windows/lateral_movement_execution_via_file_shares_sequence.toml - rules/windows/lateral_movement_incoming_winrm_shell_execution.toml - rules/windows/lateral_movement_incoming_wmi.toml - rules/windows/lateral_movement_mount_hidden_or_webdav_share_net.toml - rules/windows/lateral_movement_powershell_remoting_target.toml - rules/windows/lateral_movement_rdp_enabled_registry.toml - rules/windows/lateral_movement_rdp_sharprdp_target.toml - rules/windows/lateral_movement_remote_file_copy_hidden_share.toml - rules/windows/lateral_movement_remote_service_installed_winlog.toml - rules/windows/lateral_movement_remote_services.toml - rules/windows/lateral_movement_remote_task_creation_winlog.toml - rules/windows/lateral_movement_scheduled_task_target.toml - rules/windows/lateral_movement_service_control_spawned_script_int.toml - rules/windows/lateral_movement_suspicious_rdp_client_imageload.toml - rules/windows/lateral_movement_via_startup_folder_rdp_smb.toml - rules/windows/persistence_ad_adminsdholder.toml - rules/windows/persistence_adobe_hijack_persistence.toml - rules/windows/persistence_app_compat_shim.toml - rules/windows/persistence_appcertdlls_registry.toml - rules/windows/persistence_appinitdlls_registry.toml - rules/windows/persistence_dontexpirepasswd_account.toml - rules/windows/persistence_driver_newterm_imphash.toml - rules/windows/persistence_evasion_hidden_local_account_creation.toml - rules/windows/persistence_evasion_registry_ifeo_injection.toml - rules/windows/persistence_evasion_registry_startup_shell_folder_modified.toml - rules/windows/persistence_gpo_schtask_service_creation.toml - rules/windows/persistence_local_scheduled_job_creation.toml - rules/windows/persistence_local_scheduled_task_creation.toml - rules/windows/persistence_local_scheduled_task_scripting.toml - rules/windows/persistence_ms_office_addins_file.toml - rules/windows/persistence_ms_outlook_vba_template.toml - rules/windows/persistence_msds_alloweddelegateto_krbtgt.toml - rules/windows/persistence_powershell_exch_mailbox_activesync_add_device.toml - rules/windows/persistence_powersshell_profiles.toml - rules/windows/persistence_priv_escalation_via_accessibility_features.toml - rules/windows/persistence_registry_uncommon.toml - rules/windows/persistence_remote_password_reset.toml - rules/windows/persistence_run_key_and_startup_broad.toml - rules/windows/persistence_runtime_run_key_startup_susp_procs.toml - rules/windows/persistence_scheduled_task_creation_winlog.toml - rules/windows/persistence_scheduled_task_updated.toml - rules/windows/persistence_sdprop_exclusion_dsheuristics.toml - rules/windows/persistence_service_dll_unsigned.toml - rules/windows/persistence_service_windows_service_winlog.toml - rules/windows/persistence_services_registry.toml - rules/windows/persistence_startup_folder_file_written_by_suspicious_process.toml - rules/windows/persistence_startup_folder_file_written_by_unsigned_process.toml - rules/windows/persistence_startup_folder_scripts.toml - rules/windows/persistence_suspicious_com_hijack_registry.toml - rules/windows/persistence_suspicious_image_load_scheduled_task_ms_office.toml - rules/windows/persistence_suspicious_scheduled_task_runtime.toml - rules/windows/persistence_suspicious_service_created_registry.toml - rules/windows/persistence_system_shells_via_services.toml - rules/windows/persistence_temp_scheduled_task.toml - rules/windows/persistence_time_provider_mod.toml - rules/windows/persistence_user_account_added_to_privileged_group_ad.toml - rules/windows/persistence_user_account_creation.toml - rules/windows/persistence_via_application_shimming.toml - rules/windows/persistence_via_bits_job_notify_command.toml - rules/windows/persistence_via_hidden_run_key_valuename.toml - rules/windows/persistence_via_lsa_security_support_provider_registry.toml - rules/windows/persistence_via_telemetrycontroller_scheduledtask_hijack.toml - rules/windows/persistence_via_update_orchestrator_service_hijack.toml - rules/windows/persistence_via_windows_management_instrumentation_event_subscription.toml - rules/windows/persistence_via_wmi_stdregprov_run_services.toml - rules/windows/persistence_webshell_detection.toml - rules/windows/privilege_escalation_create_process_as_different_user.toml - rules/windows/privilege_escalation_credroaming_ldap.toml - rules/windows/privilege_escalation_disable_uac_registry.toml - rules/windows/privilege_escalation_group_policy_iniscript.toml - rules/windows/privilege_escalation_group_policy_privileged_groups.toml - rules/windows/privilege_escalation_group_policy_scheduled_task.toml - rules/windows/privilege_escalation_installertakeover.toml - rules/windows/privilege_escalation_krbrelayup_service_creation.toml - rules/windows/privilege_escalation_lsa_auth_package.toml - rules/windows/privilege_escalation_named_pipe_impersonation.toml - rules/windows/privilege_escalation_persistence_phantom_dll.toml - rules/windows/privilege_escalation_port_monitor_print_pocessor_abuse.toml - rules/windows/privilege_escalation_posh_token_impersonation.toml - rules/windows/privilege_escalation_printspooler_registry_copyfiles.toml - rules/windows/privilege_escalation_printspooler_service_suspicious_file.toml - rules/windows/privilege_escalation_printspooler_suspicious_file_deletion.toml - rules/windows/privilege_escalation_printspooler_suspicious_spl_file.toml - rules/windows/privilege_escalation_rogue_windir_environment_var.toml - rules/windows/privilege_escalation_samaccountname_spoofing_attack.toml - rules/windows/privilege_escalation_suspicious_dnshostname_update.toml - rules/windows/privilege_escalation_tokenmanip_sedebugpriv_enabled.toml - rules/windows/privilege_escalation_uac_bypass_com_clipup.toml - rules/windows/privilege_escalation_uac_bypass_com_ieinstal.toml - rules/windows/privilege_escalation_uac_bypass_com_interface_icmluautil.toml - rules/windows/privilege_escalation_uac_bypass_diskcleanup_hijack.toml - rules/windows/privilege_escalation_uac_bypass_dll_sideloading.toml - rules/windows/privilege_escalation_uac_bypass_event_viewer.toml - rules/windows/privilege_escalation_uac_bypass_mock_windir.toml - rules/windows/privilege_escalation_uac_bypass_winfw_mmc_hijack.toml - rules/windows/privilege_escalation_unusual_parentchild_relationship.toml - rules/windows/privilege_escalation_unusual_printspooler_childprocess.toml - rules/windows/privilege_escalation_unusual_svchost_childproc_childless.toml - rules/windows/privilege_escalation_via_ppid_spoofing.toml - rules/windows/privilege_escalation_via_rogue_named_pipe.toml - rules/windows/privilege_escalation_via_token_theft.toml - rules/windows/privilege_escalation_windows_service_via_unusual_client.toml (selectively cherry picked from commit 59da2da)
) * add unit tests to ensure host type and platform are included * add host.os.name 'linux' to all linux rules * add host.os.name macos to mac rules * add host.os.name to windows rules; fix linux dates * update from host.os.name to host.os.type Co-authored-by: brokensound77 <brokensound77@users.noreply.github.com> Co-authored-by: Jonhnathan <26856693+w0rk3r@users.noreply.github.com> Removed changes from: - rules/linux/command_and_control_connection_attempt_by_non_ssh_root_session.toml - rules/linux/command_and_control_linux_iodine_activity.toml - rules/linux/command_and_control_tunneling_via_earthworm.toml - rules/linux/credential_access_bruteforce_password_guessing.toml - rules/linux/credential_access_collection_sensitive_files.toml - rules/linux/credential_access_credential_dumping.toml - rules/linux/credential_access_potential_linux_ssh_bruteforce.toml - rules/linux/credential_access_potential_linux_ssh_bruteforce_root.toml - rules/linux/credential_access_ssh_backdoor_log.toml - rules/linux/defense_evasion_attempt_to_disable_iptables_or_firewall.toml - rules/linux/defense_evasion_attempt_to_disable_syslog_service.toml - rules/linux/defense_evasion_base16_or_base32_encoding_or_decoding_activity.toml - rules/linux/defense_evasion_chattr_immutable_file.toml - rules/linux/defense_evasion_disable_selinux_attempt.toml - rules/linux/defense_evasion_file_deletion_via_shred.toml - rules/linux/defense_evasion_file_mod_writable_dir.toml - rules/linux/defense_evasion_hidden_file_dir_tmp.toml - rules/linux/defense_evasion_hidden_shared_object.toml - rules/linux/defense_evasion_kernel_module_removal.toml - rules/linux/defense_evasion_log_files_deleted.toml - rules/linux/discovery_kernel_module_enumeration.toml - rules/linux/discovery_linux_hping_activity.toml - rules/linux/discovery_linux_nping_activity.toml - rules/linux/discovery_virtual_machine_fingerprinting.toml - rules/linux/execution_abnormal_process_id_file_created.toml - rules/linux/execution_file_transfer_or_listener_established_via_netcat.toml - rules/linux/execution_perl_tty_shell.toml - rules/linux/execution_process_started_from_process_id_file.toml - rules/linux/execution_process_started_in_shared_memory_directory.toml - rules/linux/execution_python_tty_shell.toml - rules/linux/execution_reverse_shell_via_named_pipe.toml - rules/linux/execution_shell_evasion_linux_binary.toml - rules/linux/execution_tc_bpf_filter.toml - rules/linux/impact_process_kill_threshold.toml - rules/linux/lateral_movement_telnet_network_activity_external.toml - rules/linux/lateral_movement_telnet_network_activity_internal.toml - rules/linux/persistence_chkconfig_service_add.toml - rules/linux/persistence_credential_access_modify_ssh_binaries.toml - rules/linux/persistence_dynamic_linker_backup.toml - rules/linux/persistence_etc_file_creation.toml - rules/linux/persistence_insmod_kernel_module_load.toml - rules/linux/persistence_kde_autostart_modification.toml - rules/linux/persistence_shell_activity_by_web_server.toml - rules/linux/privilege_escalation_ld_preload_shared_object_modif.toml - rules/linux/privilege_escalation_pkexec_envar_hijack.toml - rules/linux/privilege_escalation_shadow_file_read.toml - rules/linux/privilege_escalation_unshare_namesapce_manipulation.toml - rules/macos/credential_access_access_to_browser_credentials_procargs.toml - rules/macos/credential_access_credentials_keychains.toml - rules/macos/credential_access_dumping_hashes_bi_cmds.toml - rules/macos/credential_access_dumping_keychain_security.toml - rules/macos/credential_access_kerberosdump_kcc.toml - rules/macos/credential_access_keychain_pwd_retrieval_security_cmd.toml - rules/macos/credential_access_mitm_localhost_webproxy.toml - rules/macos/credential_access_potential_macos_ssh_bruteforce.toml - rules/macos/credential_access_promt_for_pwd_via_osascript.toml - rules/macos/credential_access_systemkey_dumping.toml - rules/macos/defense_evasion_apple_softupdates_modification.toml - rules/macos/defense_evasion_attempt_del_quarantine_attrib.toml - rules/macos/defense_evasion_attempt_to_disable_gatekeeper.toml - rules/macos/defense_evasion_install_root_certificate.toml - rules/macos/defense_evasion_modify_environment_launchctl.toml - rules/macos/defense_evasion_privacy_controls_tcc_database_modification.toml - rules/macos/defense_evasion_privilege_escalation_privacy_pref_sshd_fulldiskaccess.toml - rules/macos/defense_evasion_safari_config_change.toml - rules/macos/defense_evasion_sandboxed_office_app_suspicious_zip_file.toml - rules/macos/defense_evasion_tcc_bypass_mounted_apfs_access.toml - rules/macos/defense_evasion_unload_endpointsecurity_kext.toml - rules/macos/discovery_users_domain_built_in_commands.toml - rules/macos/execution_defense_evasion_electron_app_childproc_node_js.toml - rules/macos/execution_initial_access_suspicious_browser_childproc.toml - rules/macos/execution_installer_package_spawned_network_event.toml - rules/macos/execution_script_via_automator_workflows.toml - rules/macos/execution_scripting_osascript_exec_followed_by_netcon.toml - rules/macos/execution_shell_execution_via_apple_scripting.toml - rules/macos/initial_access_suspicious_mac_ms_office_child_process.toml - rules/macos/lateral_movement_credential_access_kerberos_bifrostconsole.toml - rules/macos/lateral_movement_mounting_smb_share.toml - rules/macos/lateral_movement_remote_ssh_login_enabled.toml - rules/macos/lateral_movement_vpn_connection_attempt.toml - rules/macos/persistence_account_creation_hide_at_logon.toml - rules/macos/persistence_creation_change_launch_agents_file.toml - rules/macos/persistence_creation_hidden_login_item_osascript.toml - rules/macos/persistence_creation_modif_launch_deamon_sequence.toml - rules/macos/persistence_credential_access_authorization_plugin_creation.toml - rules/macos/persistence_crontab_creation.toml - rules/macos/persistence_defense_evasion_hidden_launch_agent_deamon_logonitem_process.toml - rules/macos/persistence_directory_services_plugins_modification.toml - rules/macos/persistence_docker_shortcuts_plist_modification.toml - rules/macos/persistence_emond_rules_file_creation.toml - rules/macos/persistence_emond_rules_process_execution.toml - rules/macos/persistence_enable_root_account.toml - rules/macos/persistence_evasion_hidden_launch_agent_deamon_creation.toml - rules/macos/persistence_finder_sync_plugin_pluginkit.toml - rules/macos/persistence_folder_action_scripts_runtime.toml - rules/macos/persistence_login_logout_hooks_defaults.toml - rules/macos/persistence_loginwindow_plist_modification.toml - rules/macos/persistence_modification_sublime_app_plugin_or_script.toml - rules/macos/persistence_periodic_tasks_file_mdofiy.toml - rules/macos/persistence_screensaver_engine_unexpected_child_process.toml - rules/macos/persistence_screensaver_plist_file_modification.toml - rules/macos/persistence_suspicious_calendar_modification.toml - rules/macos/persistence_via_atom_init_file_modification.toml - rules/macos/privilege_escalation_applescript_with_admin_privs.toml - rules/macos/privilege_escalation_explicit_creds_via_scripting.toml - rules/macos/privilege_escalation_exploit_adobe_acrobat_updater.toml - rules/macos/privilege_escalation_local_user_added_to_admin.toml - rules/macos/privilege_escalation_root_crontab_filemod.toml - rules/windows/collection_email_outlook_mailbox_via_com.toml - rules/windows/collection_email_powershell_exchange_mailbox.toml - rules/windows/collection_mailbox_export_winlog.toml - rules/windows/collection_posh_audio_capture.toml - rules/windows/collection_posh_clipboard_capture.toml - rules/windows/collection_posh_keylogger.toml - rules/windows/collection_posh_mailbox.toml - rules/windows/collection_posh_screen_grabber.toml - rules/windows/collection_winrar_encryption.toml - rules/windows/command_and_control_certreq_postdata.toml - rules/windows/command_and_control_certutil_network_connection.toml - rules/windows/command_and_control_common_webservices.toml - rules/windows/command_and_control_dns_tunneling_nslookup.toml - rules/windows/command_and_control_encrypted_channel_freesslcert.toml - rules/windows/command_and_control_iexplore_via_com.toml - rules/windows/command_and_control_ingress_transfer_bits.toml - rules/windows/command_and_control_port_forwarding_added_registry.toml - rules/windows/command_and_control_rdp_tunnel_plink.toml - rules/windows/command_and_control_remote_file_copy_desktopimgdownldr.toml - rules/windows/command_and_control_remote_file_copy_mpcmdrun.toml - rules/windows/command_and_control_remote_file_copy_powershell.toml - rules/windows/command_and_control_remote_file_copy_scripts.toml - rules/windows/command_and_control_sunburst_c2_activity_detected.toml - rules/windows/command_and_control_teamviewer_remote_file_copy.toml - rules/windows/credential_access_bruteforce_admin_account.toml - rules/windows/credential_access_bruteforce_multiple_logon_failure_followed_by_success.toml - rules/windows/credential_access_bruteforce_multiple_logon_failure_same_srcip.toml - rules/windows/credential_access_cmdline_dump_tool.toml - rules/windows/credential_access_copy_ntds_sam_volshadowcp_cmdline.toml - rules/windows/credential_access_credential_dumping_msbuild.toml - rules/windows/credential_access_dcsync_newterm_subjectuser.toml - rules/windows/credential_access_dcsync_replication_rights.toml - rules/windows/credential_access_disable_kerberos_preauth.toml - rules/windows/credential_access_domain_backup_dpapi_private_keys.toml - rules/windows/credential_access_dump_registry_hives.toml - rules/windows/credential_access_generic_localdumps.toml - rules/windows/credential_access_iis_apppoolsa_pwd_appcmd.toml - rules/windows/credential_access_iis_connectionstrings_dumping.toml - rules/windows/credential_access_kerberoasting_unusual_process.toml - rules/windows/credential_access_ldap_attributes.toml - rules/windows/credential_access_lsass_handle_via_malseclogon.toml - rules/windows/credential_access_lsass_loaded_susp_dll.toml - rules/windows/credential_access_lsass_memdump_file_created.toml - rules/windows/credential_access_lsass_memdump_handle_access.toml - rules/windows/credential_access_mimikatz_memssp_default_logs.toml - rules/windows/credential_access_mimikatz_powershell_module.toml - rules/windows/credential_access_mod_wdigest_security_provider.toml - rules/windows/credential_access_moving_registry_hive_via_smb.toml - rules/windows/credential_access_persistence_network_logon_provider_modification.toml - rules/windows/credential_access_posh_invoke_ninjacopy.toml - rules/windows/credential_access_posh_minidump.toml - rules/windows/credential_access_posh_request_ticket.toml - rules/windows/credential_access_potential_lsa_memdump_via_mirrordump.toml - rules/windows/credential_access_relay_ntlm_auth_via_http_spoolss.toml - rules/windows/credential_access_remote_sam_secretsdump.toml - rules/windows/credential_access_saved_creds_vault_winlog.toml - rules/windows/credential_access_saved_creds_vaultcmd.toml - rules/windows/credential_access_seenabledelegationprivilege_assigned_to_user.toml - rules/windows/credential_access_shadow_credentials.toml - rules/windows/credential_access_spn_attribute_modified.toml - rules/windows/credential_access_suspicious_comsvcs_imageload.toml - rules/windows/credential_access_suspicious_lsass_access_generic.toml - rules/windows/credential_access_suspicious_lsass_access_memdump.toml - rules/windows/credential_access_suspicious_lsass_access_via_snapshot.toml - rules/windows/credential_access_suspicious_winreg_access_via_sebackup_priv.toml - rules/windows/credential_access_symbolic_link_to_shadow_copy_created.toml - rules/windows/credential_access_via_snapshot_lsass_clone_creation.toml - rules/windows/credential_access_wireless_creds_dumping.toml - rules/windows/defense_evasion_adding_the_hidden_file_attribute_with_via_attribexe.toml - rules/windows/defense_evasion_amsi_bypass_dllhijack.toml - rules/windows/defense_evasion_amsi_bypass_powershell.toml - rules/windows/defense_evasion_amsienable_key_mod.toml - rules/windows/defense_evasion_clearing_windows_console_history.toml - rules/windows/defense_evasion_clearing_windows_event_logs.toml - rules/windows/defense_evasion_clearing_windows_security_logs.toml - rules/windows/defense_evasion_code_signing_policy_modification_builtin_tools.toml - rules/windows/defense_evasion_code_signing_policy_modification_registry.toml - rules/windows/defense_evasion_create_mod_root_certificate.toml - rules/windows/defense_evasion_cve_2020_0601.toml - rules/windows/defense_evasion_defender_disabled_via_registry.toml - rules/windows/defense_evasion_defender_exclusion_via_powershell.toml - rules/windows/defense_evasion_delete_volume_usn_journal_with_fsutil.toml - rules/windows/defense_evasion_disable_posh_scriptblocklogging.toml - rules/windows/defense_evasion_disable_windows_firewall_rules_with_netsh.toml - rules/windows/defense_evasion_disabling_windows_defender_powershell.toml - rules/windows/defense_evasion_disabling_windows_logs.toml - rules/windows/defense_evasion_dns_over_https_enabled.toml - rules/windows/defense_evasion_dotnet_compiler_parent_process.toml - rules/windows/defense_evasion_enable_inbound_rdp_with_netsh.toml - rules/windows/defense_evasion_enable_network_discovery_with_netsh.toml - rules/windows/defense_evasion_execution_control_panel_suspicious_args.toml - rules/windows/defense_evasion_execution_lolbas_wuauclt.toml - rules/windows/defense_evasion_execution_msbuild_started_by_office_app.toml - rules/windows/defense_evasion_execution_msbuild_started_by_script.toml - rules/windows/defense_evasion_execution_msbuild_started_by_system_process.toml - rules/windows/defense_evasion_execution_msbuild_started_renamed.toml - rules/windows/defense_evasion_execution_msbuild_started_unusal_process.toml - rules/windows/defense_evasion_execution_suspicious_explorer_winword.toml - rules/windows/defense_evasion_execution_windefend_unusual_path.toml - rules/windows/defense_evasion_file_creation_mult_extension.toml - rules/windows/defense_evasion_from_unusual_directory.toml - rules/windows/defense_evasion_hide_encoded_executable_registry.toml - rules/windows/defense_evasion_iis_httplogging_disabled.toml - rules/windows/defense_evasion_injection_msbuild.toml - rules/windows/defense_evasion_installutil_beacon.toml - rules/windows/defense_evasion_masquerading_as_elastic_endpoint_process.toml - rules/windows/defense_evasion_masquerading_renamed_autoit.toml - rules/windows/defense_evasion_masquerading_suspicious_werfault_childproc.toml - rules/windows/defense_evasion_masquerading_trusted_directory.toml - rules/windows/defense_evasion_masquerading_werfault.toml - rules/windows/defense_evasion_microsoft_defender_tampering.toml - rules/windows/defense_evasion_misc_lolbin_connecting_to_the_internet.toml - rules/windows/defense_evasion_ms_office_suspicious_regmod.toml - rules/windows/defense_evasion_msbuild_making_network_connections.toml - rules/windows/defense_evasion_mshta_beacon.toml - rules/windows/defense_evasion_msxsl_network.toml - rules/windows/defense_evasion_network_connection_from_windows_binary.toml - rules/windows/defense_evasion_parent_process_pid_spoofing.toml - rules/windows/defense_evasion_persistence_account_tokenfilterpolicy.toml - rules/windows/defense_evasion_posh_assembly_load.toml - rules/windows/defense_evasion_posh_compressed.toml - rules/windows/defense_evasion_posh_encryption.toml - rules/windows/defense_evasion_posh_process_injection.toml - rules/windows/defense_evasion_potential_processherpaderping.toml - rules/windows/defense_evasion_powershell_windows_firewall_disabled.toml - rules/windows/defense_evasion_process_termination_followed_by_deletion.toml - rules/windows/defense_evasion_proxy_execution_via_msdt.toml - rules/windows/defense_evasion_rundll32_no_arguments.toml - rules/windows/defense_evasion_scheduledjobs_at_protocol_enabled.toml - rules/windows/defense_evasion_sdelete_like_filename_rename.toml - rules/windows/defense_evasion_sip_provider_mod.toml - rules/windows/defense_evasion_solarwinds_backdoor_service_disabled_via_registry.toml - rules/windows/defense_evasion_suspicious_certutil_commands.toml - rules/windows/defense_evasion_suspicious_execution_from_mounted_device.toml - rules/windows/defense_evasion_suspicious_managedcode_host_process.toml - rules/windows/defense_evasion_suspicious_process_access_direct_syscall.toml - rules/windows/defense_evasion_suspicious_process_creation_calltrace.toml - rules/windows/defense_evasion_suspicious_scrobj_load.toml - rules/windows/defense_evasion_suspicious_short_program_name.toml - rules/windows/defense_evasion_suspicious_wmi_script.toml - rules/windows/defense_evasion_suspicious_zoom_child_process.toml - rules/windows/defense_evasion_system_critical_proc_abnormal_file_activity.toml - rules/windows/defense_evasion_timestomp_sysmon.toml - rules/windows/defense_evasion_unsigned_dll_loaded_from_suspdir.toml - rules/windows/defense_evasion_untrusted_driver_loaded.toml - rules/windows/defense_evasion_unusual_ads_file_creation.toml - rules/windows/defense_evasion_unusual_dir_ads.toml - rules/windows/defense_evasion_unusual_network_connection_via_dllhost.toml - rules/windows/defense_evasion_unusual_network_connection_via_rundll32.toml - rules/windows/defense_evasion_unusual_process_network_connection.toml - rules/windows/defense_evasion_unusual_system_vp_child_program.toml - rules/windows/defense_evasion_via_filter_manager.toml - rules/windows/defense_evasion_workfolders_control_execution.toml - rules/windows/defense_evasion_wsl_bash_exec.toml - rules/windows/defense_evasion_wsl_child_process.toml - rules/windows/defense_evasion_wsl_enabled_via_dism.toml - rules/windows/defense_evasion_wsl_filesystem.toml - rules/windows/defense_evasion_wsl_kalilinux.toml - rules/windows/defense_evasion_wsl_registry_modification.toml - rules/windows/discovery_adfind_command_activity.toml - rules/windows/discovery_admin_recon.toml - rules/windows/discovery_command_system_account.toml - rules/windows/discovery_enumerating_domain_trusts_via_dsquery.toml - rules/windows/discovery_enumerating_domain_trusts_via_nltest.toml - rules/windows/discovery_files_dir_systeminfo_via_cmd.toml - rules/windows/discovery_group_policy_object_discovery.toml - rules/windows/discovery_net_view.toml - rules/windows/discovery_peripheral_device.toml - rules/windows/discovery_posh_invoke_sharefinder.toml - rules/windows/discovery_posh_suspicious_api_functions.toml - rules/windows/discovery_post_exploitation_external_ip_lookup.toml - rules/windows/discovery_privileged_localgroup_membership.toml - rules/windows/discovery_remote_system_discovery_commands_windows.toml - rules/windows/discovery_security_software_wmic.toml - rules/windows/discovery_system_service_discovery.toml - rules/windows/discovery_system_time_discovery.toml - rules/windows/discovery_whoami_command_activity.toml - rules/windows/execution_apt_solarwinds_backdoor_child_cmd_powershell.toml - rules/windows/execution_apt_solarwinds_backdoor_unusual_child_processes.toml - rules/windows/execution_com_object_xwizard.toml - rules/windows/execution_command_prompt_connecting_to_the_internet.toml - rules/windows/execution_command_shell_started_by_svchost.toml - rules/windows/execution_command_shell_started_by_unusual_process.toml - rules/windows/execution_command_shell_via_rundll32.toml - rules/windows/execution_enumeration_via_wmiprvse.toml - rules/windows/execution_from_unusual_path_cmdline.toml - rules/windows/execution_html_help_executable_program_connecting_to_the_internet.toml - rules/windows/execution_ms_office_written_file.toml - rules/windows/execution_pdf_written_file.toml - rules/windows/execution_posh_hacktool_functions.toml - rules/windows/execution_posh_portable_executable.toml - rules/windows/execution_posh_psreflect.toml - rules/windows/execution_psexec_lateral_movement_command.toml - rules/windows/execution_register_server_program_connecting_to_the_internet.toml - rules/windows/execution_scheduled_task_powershell_source.toml - rules/windows/execution_shared_modules_local_sxs_dll.toml - rules/windows/execution_suspicious_cmd_wmi.toml - rules/windows/execution_suspicious_image_load_wmi_ms_office.toml - rules/windows/execution_suspicious_pdf_reader.toml - rules/windows/execution_suspicious_powershell_imgload.toml - rules/windows/execution_suspicious_psexesvc.toml - rules/windows/execution_via_compiled_html_file.toml - rules/windows/execution_via_hidden_shell_conhost.toml - rules/windows/execution_via_xp_cmdshell_mssql_stored_procedure.toml - rules/windows/impact_backup_file_deletion.toml - rules/windows/impact_deleting_backup_catalogs_with_wbadmin.toml - rules/windows/impact_modification_of_boot_config.toml - rules/windows/impact_stop_process_service_threshold.toml - rules/windows/impact_volume_shadow_copy_deletion_or_resized_via_vssadmin.toml - rules/windows/impact_volume_shadow_copy_deletion_via_powershell.toml - rules/windows/impact_volume_shadow_copy_deletion_via_wmic.toml - rules/windows/initial_access_evasion_suspicious_htm_file_creation.toml - rules/windows/initial_access_script_executing_powershell.toml - rules/windows/initial_access_scripts_process_started_via_wmi.toml - rules/windows/initial_access_suspicious_ms_exchange_files.toml - rules/windows/initial_access_suspicious_ms_exchange_process.toml - rules/windows/initial_access_suspicious_ms_exchange_worker_child_process.toml - rules/windows/initial_access_suspicious_ms_office_child_process.toml - rules/windows/initial_access_suspicious_ms_outlook_child_process.toml - rules/windows/initial_access_unusual_dns_service_children.toml - rules/windows/initial_access_unusual_dns_service_file_writes.toml - rules/windows/initial_access_via_explorer_suspicious_child_parent_args.toml - rules/windows/lateral_movement_cmd_service.toml - rules/windows/lateral_movement_dcom_hta.toml - rules/windows/lateral_movement_dcom_mmc20.toml - rules/windows/lateral_movement_dcom_shellwindow_shellbrowserwindow.toml - rules/windows/lateral_movement_defense_evasion_lanman_nullsessionpipe_modification.toml - rules/windows/lateral_movement_direct_outbound_smb_connection.toml - rules/windows/lateral_movement_dns_server_overflow.toml - rules/windows/lateral_movement_evasion_rdp_shadowing.toml - rules/windows/lateral_movement_executable_tool_transfer_smb.toml - rules/windows/lateral_movement_execution_from_tsclient_mup.toml - rules/windows/lateral_movement_execution_via_file_shares_sequence.toml - rules/windows/lateral_movement_incoming_winrm_shell_execution.toml - rules/windows/lateral_movement_incoming_wmi.toml - rules/windows/lateral_movement_mount_hidden_or_webdav_share_net.toml - rules/windows/lateral_movement_powershell_remoting_target.toml - rules/windows/lateral_movement_rdp_enabled_registry.toml - rules/windows/lateral_movement_rdp_sharprdp_target.toml - rules/windows/lateral_movement_remote_file_copy_hidden_share.toml - rules/windows/lateral_movement_remote_service_installed_winlog.toml - rules/windows/lateral_movement_remote_services.toml - rules/windows/lateral_movement_remote_task_creation_winlog.toml - rules/windows/lateral_movement_scheduled_task_target.toml - rules/windows/lateral_movement_service_control_spawned_script_int.toml - rules/windows/lateral_movement_suspicious_rdp_client_imageload.toml - rules/windows/lateral_movement_via_startup_folder_rdp_smb.toml - rules/windows/persistence_ad_adminsdholder.toml - rules/windows/persistence_adobe_hijack_persistence.toml - rules/windows/persistence_app_compat_shim.toml - rules/windows/persistence_appcertdlls_registry.toml - rules/windows/persistence_appinitdlls_registry.toml - rules/windows/persistence_dontexpirepasswd_account.toml - rules/windows/persistence_driver_newterm_imphash.toml - rules/windows/persistence_evasion_hidden_local_account_creation.toml - rules/windows/persistence_evasion_registry_ifeo_injection.toml - rules/windows/persistence_evasion_registry_startup_shell_folder_modified.toml - rules/windows/persistence_gpo_schtask_service_creation.toml - rules/windows/persistence_local_scheduled_job_creation.toml - rules/windows/persistence_local_scheduled_task_creation.toml - rules/windows/persistence_local_scheduled_task_scripting.toml - rules/windows/persistence_ms_office_addins_file.toml - rules/windows/persistence_ms_outlook_vba_template.toml - rules/windows/persistence_msds_alloweddelegateto_krbtgt.toml - rules/windows/persistence_powershell_exch_mailbox_activesync_add_device.toml - rules/windows/persistence_powersshell_profiles.toml - rules/windows/persistence_priv_escalation_via_accessibility_features.toml - rules/windows/persistence_registry_uncommon.toml - rules/windows/persistence_remote_password_reset.toml - rules/windows/persistence_run_key_and_startup_broad.toml - rules/windows/persistence_runtime_run_key_startup_susp_procs.toml - rules/windows/persistence_scheduled_task_creation_winlog.toml - rules/windows/persistence_scheduled_task_updated.toml - rules/windows/persistence_sdprop_exclusion_dsheuristics.toml - rules/windows/persistence_service_dll_unsigned.toml - rules/windows/persistence_service_windows_service_winlog.toml - rules/windows/persistence_services_registry.toml - rules/windows/persistence_startup_folder_file_written_by_suspicious_process.toml - rules/windows/persistence_startup_folder_file_written_by_unsigned_process.toml - rules/windows/persistence_startup_folder_scripts.toml - rules/windows/persistence_suspicious_com_hijack_registry.toml - rules/windows/persistence_suspicious_image_load_scheduled_task_ms_office.toml - rules/windows/persistence_suspicious_scheduled_task_runtime.toml - rules/windows/persistence_suspicious_service_created_registry.toml - rules/windows/persistence_system_shells_via_services.toml - rules/windows/persistence_temp_scheduled_task.toml - rules/windows/persistence_time_provider_mod.toml - rules/windows/persistence_user_account_added_to_privileged_group_ad.toml - rules/windows/persistence_user_account_creation.toml - rules/windows/persistence_via_application_shimming.toml - rules/windows/persistence_via_bits_job_notify_command.toml - rules/windows/persistence_via_hidden_run_key_valuename.toml - rules/windows/persistence_via_lsa_security_support_provider_registry.toml - rules/windows/persistence_via_telemetrycontroller_scheduledtask_hijack.toml - rules/windows/persistence_via_update_orchestrator_service_hijack.toml - rules/windows/persistence_via_windows_management_instrumentation_event_subscription.toml - rules/windows/persistence_via_wmi_stdregprov_run_services.toml - rules/windows/persistence_webshell_detection.toml - rules/windows/privilege_escalation_create_process_as_different_user.toml - rules/windows/privilege_escalation_credroaming_ldap.toml - rules/windows/privilege_escalation_disable_uac_registry.toml - rules/windows/privilege_escalation_group_policy_iniscript.toml - rules/windows/privilege_escalation_group_policy_privileged_groups.toml - rules/windows/privilege_escalation_group_policy_scheduled_task.toml - rules/windows/privilege_escalation_installertakeover.toml - rules/windows/privilege_escalation_krbrelayup_service_creation.toml - rules/windows/privilege_escalation_lsa_auth_package.toml - rules/windows/privilege_escalation_named_pipe_impersonation.toml - rules/windows/privilege_escalation_persistence_phantom_dll.toml - rules/windows/privilege_escalation_port_monitor_print_pocessor_abuse.toml - rules/windows/privilege_escalation_posh_token_impersonation.toml - rules/windows/privilege_escalation_printspooler_registry_copyfiles.toml - rules/windows/privilege_escalation_printspooler_service_suspicious_file.toml - rules/windows/privilege_escalation_printspooler_suspicious_file_deletion.toml - rules/windows/privilege_escalation_printspooler_suspicious_spl_file.toml - rules/windows/privilege_escalation_rogue_windir_environment_var.toml - rules/windows/privilege_escalation_samaccountname_spoofing_attack.toml - rules/windows/privilege_escalation_suspicious_dnshostname_update.toml - rules/windows/privilege_escalation_tokenmanip_sedebugpriv_enabled.toml - rules/windows/privilege_escalation_uac_bypass_com_clipup.toml - rules/windows/privilege_escalation_uac_bypass_com_ieinstal.toml - rules/windows/privilege_escalation_uac_bypass_com_interface_icmluautil.toml - rules/windows/privilege_escalation_uac_bypass_diskcleanup_hijack.toml - rules/windows/privilege_escalation_uac_bypass_dll_sideloading.toml - rules/windows/privilege_escalation_uac_bypass_event_viewer.toml - rules/windows/privilege_escalation_uac_bypass_mock_windir.toml - rules/windows/privilege_escalation_uac_bypass_winfw_mmc_hijack.toml - rules/windows/privilege_escalation_unusual_parentchild_relationship.toml - rules/windows/privilege_escalation_unusual_printspooler_childprocess.toml - rules/windows/privilege_escalation_unusual_svchost_childproc_childless.toml - rules/windows/privilege_escalation_via_ppid_spoofing.toml - rules/windows/privilege_escalation_via_rogue_named_pipe.toml - rules/windows/privilege_escalation_via_token_theft.toml - rules/windows/privilege_escalation_windows_service_via_unusual_client.toml (selectively cherry picked from commit 59da2da)
) * add unit tests to ensure host type and platform are included * add host.os.name 'linux' to all linux rules * add host.os.name macos to mac rules * add host.os.name to windows rules; fix linux dates * update from host.os.name to host.os.type Co-authored-by: brokensound77 <brokensound77@users.noreply.github.com> Co-authored-by: Jonhnathan <26856693+w0rk3r@users.noreply.github.com> Removed changes from: - rules/windows/collection_email_outlook_mailbox_via_com.toml - rules/windows/credential_access_dcsync_newterm_subjectuser.toml - rules/windows/defense_evasion_unsigned_dll_loaded_from_suspdir.toml - rules/windows/persistence_driver_newterm_imphash.toml - rules/windows/persistence_service_dll_unsigned.toml - rules/windows/privilege_escalation_via_token_theft.toml (selectively cherry picked from commit 59da2da)
) * add unit tests to ensure host type and platform are included * add host.os.name 'linux' to all linux rules * add host.os.name macos to mac rules * add host.os.name to windows rules; fix linux dates * update from host.os.name to host.os.type Co-authored-by: brokensound77 <brokensound77@users.noreply.github.com> Co-authored-by: Jonhnathan <26856693+w0rk3r@users.noreply.github.com> Removed changes from: - rules/windows/persistence_driver_newterm_imphash.toml (selectively cherry picked from commit 59da2da)
) * add unit tests to ensure host type and platform are included * add host.os.name 'linux' to all linux rules * add host.os.name macos to mac rules * add host.os.name to windows rules; fix linux dates * update from host.os.name to host.os.type Co-authored-by: brokensound77 <brokensound77@users.noreply.github.com> Co-authored-by: Jonhnathan <26856693+w0rk3r@users.noreply.github.com> Removed changes from: - rules/windows/persistence_driver_newterm_imphash.toml (selectively cherry picked from commit 59da2da)
) * add unit tests to ensure host type and platform are included * add host.os.name 'linux' to all linux rules * add host.os.name macos to mac rules * add host.os.name to windows rules; fix linux dates * update from host.os.name to host.os.type Co-authored-by: brokensound77 <brokensound77@users.noreply.github.com> Co-authored-by: Jonhnathan <26856693+w0rk3r@users.noreply.github.com> (cherry picked from commit 59da2da)
) * add unit tests to ensure host type and platform are included * add host.os.name 'linux' to all linux rules * add host.os.name macos to mac rules * add host.os.name to windows rules; fix linux dates * update from host.os.name to host.os.type Co-authored-by: brokensound77 <brokensound77@users.noreply.github.com> Co-authored-by: Jonhnathan <26856693+w0rk3r@users.noreply.github.com> (cherry picked from commit 59da2da)
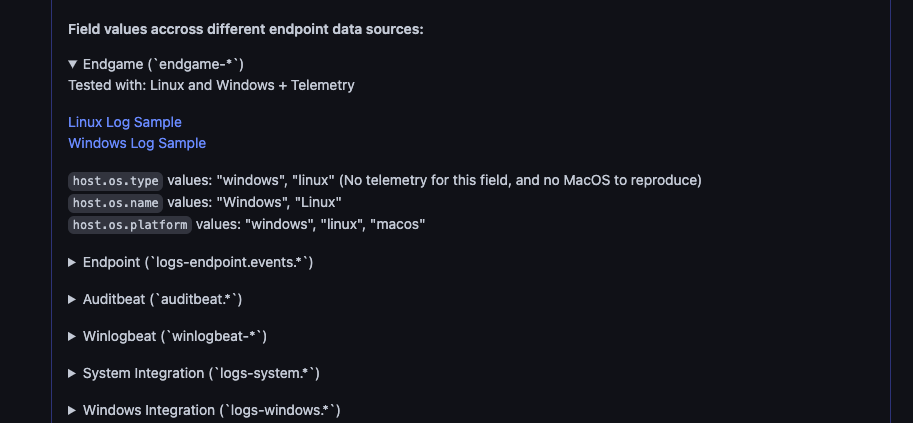
Issues
resolves #2286
Summary
Adds unit tests to ensure
host.os.nameis in endpoint rule queries andhost.os.platformis in Linux queries.Going to hold off adding
host.os.platformto linux rules until further discussionsField values accross different endpoint data sources:
Endgame (`endgame-*`)
Tested with: Linux and Windows + Telemetry
Linux Log Sample
Windows Log Sample
host.os.typevalues: "windows", "linux" (No telemetry for this field, and no MacOS to reproduce)host.os.namevalues: "Windows", "Linux"host.os.platformvalues: "windows", "linux", "macos"Endpoint (`logs-endpoint.events.*`)
Tested with: Linux and Windows + Telemetry
host.os.typevalues: "windows", "linux", "macos"host.os.platformvalues: "windows", "linux", "macos", "ubuntu", "centos", "unknown distribution", "debian", "red hat", "opensuse", "suse", "fedora", "oracle linux", "amazon linux", "sles", "Windows"Auditbeat (`auditbeat.*`)
Tested with: Linux + Telemetry (No MacOS telemetry)
Auditbeat Linux Log Sample
host.os.typevalues: "linux"host.os.namevalues: "Debian GNU/Linux", "Amazon Linux", "CentOS Linux", "Ubuntu", "Red Hat Enterprise Linux", "Sangoma Linux", "Rocky Linux", "Red Hat Enterprise Linux Server", "Kali GNU/Linux", "Amazon Linux AMI", "openSUSE Leap", "Oracle Linux Server", "Raspbian GNU/Linux", "AlmaLinux", "CentOS Stream", "Garuda Linux"host.os.platformvalues: "debian", "amzn", "centos", "ubuntu", "rhel", "sangoma", "rocky", "kali", "opensuse-leap", "ol", "raspbian", "almalinux", "garuda"Winlogbeat (`winlogbeat-*`)
Tested with: Windows and Telemetry
Windows Winlogbeat Log Sample
host.os.typevalues: "windows"host.os.namevalues: "Windows Server 2016 Datacenter Evaluation", "Windows Server 2012 R2 Datacenter", "Windows Server 2012 R2 Standard", "Windows Server 2019 Standard", "Windows Server 2016 Standard", "Windows Server 2016 Datacenter", "Windows 10 Enterprise", "Windows Server 2019 Datacenter", "Windows Server 2022 Standard", "Windows 10 Pro", "Windows Server 2012 Datacenter", "Windows Server 2008 R2 Enterprise", "Windows 7 Professional", "Windows Server 2008 R2 Standard", "Windows 11 Pro", "Windows Server 2022 Standard Evaluation", "Windows 11 Home Single Language", "Windows Server 2022 Datacenter", "Windows 11 Enterprise Evaluation", "Windows 10 Enterprise Evaluation", "Windows Server 2019 Standard Evaluation", "Windows 11 Home", "Windows 10 Home", "Windows Server 2012 R2 Datacenter Evaluation", "Windows Server 2022 Datacenter Azure Edition", "Windows 10 Enterprise LTSC 2021", "Windows Storage Server 2012 Standard", "Windows Server 2012 R2 Standard Evaluation", "Windows 10 Enterprise 2016 LTSB", "Windows 10 Pro N", "Windows Server 2012 Standard", "Windows 11 Enterprise", "Windows 10 Enterprise LTSC 2019", "Windows 7 Enterprise", "Windows 10 Pro for Workstations", "Windows 7 Home Premium", "Windows Server 2019 Datacenter Evaluation", "Windows 10 Education"host.os.platformvalues: "windows"System Integration (`logs-system.*`)
Tested with: Linux and Windows + Telemetry (No MacOS telem)
host.os.typevalues: "windows", "linux"host.os.namevalues: "Windows Server 2019 Standard", "Windows Server 2012 R2 Datacenter", "Windows 10 Enterprise", "Windows Server 2016 Standard", "Windows Server 2012 R2 Standard", "Windows 10 Enterprise for Virtual Desktops", "Windows Server 2019 Datacenter", "Windows Server 2016 Datacenter", "Windows 10 Pro", "Windows 11 Home", "Windows Server 2012 Datacenter", "Windows Server 2022 Standard", "Windows 11 Pro", "Windows 11 Enterprise", "Windows Server 2022 Datacenter", "Windows Server 2008 R2 Standard", "Ubuntu", "Windows Server 2022 Datacenter Azure Edition", "Windows Server 2012 Standard", "Debian GNU/Linux", "Windows Server 2022 Datacenter Evaluation", "Windows 10 Enterprise Evaluation", "Windows Server 2008 R2 Datacenter", "Azure Stack HCI", "CentOS Linux", "Windows 10 Pro N", "Windows 10 Home", "Red Hat Enterprise Linux Server", "Amazon Linux", "Windows Small Business Server 2011 Standard", "Windows 10 Pro for Workstations", "Windows Server 2019 Standard Evaluation", "Windows Server 2008 R2 Enterprise", "Windows Server 2022 Standard Evaluation", "Windows Server 2019 Essentials", "CentOS Stream", "Windows Server 2016 Standard Evaluation", "Red Hat Enterprise Linux", "Windows 11 Enterprise Evaluation", "Windows 10 Enterprise LTSC 2019", "Windows 11 Enterprise multi-session", "Windows Storage Server 2016 Standard", "Windows 10 Pro Education", "OceanX Linux", "Windows 11 Home Single Language", "Windows 10 Education", "Windows 10 Home Single Language", "Windows 8.1 Pro with Media Center", "Windows Server 2019 Datacenter Evaluation", "Hyper-V Server 2019", "Windows 8.1 Pro", "Windows 7 Professional", "SLES", "Windows 10 Enterprise N", "Windows 10 Enterprise 2016 LTSB", "Rocky Linux", "Oracle Linux Server", "CentOS", "Kali GNU/Linux", "Zorin OS", "AlmaLinux", "CloudLinux", "TencentOS Server", "Virtuozzo"host.os.platformvalues: "windows", "ubuntu", "debian", "centos", "rhel", "amzn", "oceanx", "sles", "rocky", "ol", "kali", "zorin", "almalinux", "cloudlinux", "tencentos", "virtuozzo"Windows Integration (`logs-windows.*`)
Tested with: Windows + Telemetry
host.os.typevalues: "windows"host.os.namevalues: "Windows 10 Enterprise", "Windows 10 Pro", "Windows Server 2016 Datacenter", "Windows Server 2012 R2 Standard", "Windows Server 2012 R2 Datacenter", "Windows Server 2022 Datacenter", "Windows Server 2019 Datacenter", "Windows Server 2016 Standard", "Windows Server 2012 Datacenter", "Windows Server 2019 Standard", "Windows 10 Enterprise for Virtual Desktops", "Windows Server 2022 Datacenter Azure Edition", "Windows 10 IoT Enterprise", "Windows 11 Enterprise", "Windows 10 Enterprise LTSC 2019", "Windows Server 2019 Standard Evaluation", "Windows 11 Pro", "Hyper-V Server 2019", "Windows 8.1 Pro with Media Center", "Windows 11 Home Single Language", "Windows 10 Enterprise Evaluation", "Windows Server 2022 Standard", "Windows Server 2012 Standard", "Windows 10 Home", "Windows 11 Enterprise multi-session", "Windows Server 2022 Standard Evaluation", "Windows 8.1 Pro", "Windows 10 Enterprise Evaluation", "Windows 10 Education", "Windows 10 Pro for Workstations", "Windows 11 Home", "Windows Server 2008 R2 Enterprise", "Azure Stack HCI", "Windows 11 Pro for Workstations", "Windows Server 2008 R2 Standard", "Windows 10 Pro Education", "Windows 7 Professional", "Windows Server 2008 R2 Datacenter", "Windows 7 Enterprise", "Windows Server 2016 Standard Evaluation", "Windows 10 Enterprise N", "Windows 10 Pro N", "Windows 7 Ultimate", "Windows Server 2019 Datacenter Evaluation", "Hyper-V Server 2012 R2", "Windows 10 Enterprise 2016 LTSB"host.os.platformvalues: "windows"Testing
To test, simply remove the
host.os.typefrom any endpoint rule and runmake test