-
Couldn't load subscription status.
- Fork 1.8k
Description
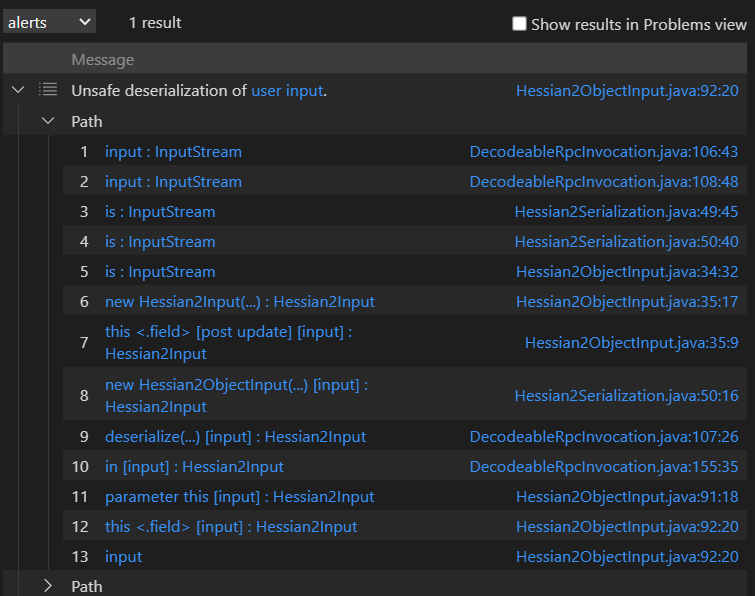
I'm trying to write codeql queries for the CVE-2021-43297 (unsafe toString call lead to deserialization of malicious object). The source of this is the InputStream input parameter of decode method at DecodeableRpcInvocation class. And the sink is obviously the implicit toString call.
I found that the taint tracking flow cannot get to the qualifier of readObject method (at readObject method of Hessian2ObjectInput class. I firstly think that there is barrier, so I using DataFlow to workaround with built-in taint tracking step features, but it still doesn't work. However, when I comment out the predicate defaultAdditionalTaintStep, the queries found the path from source to the qualifier as expected.
One more issue is that it works only with readObject method, but not readUTF method. I can't figure out what code snippet controls it.
I can't understand how that behavior happens! The defaultAdditionalTaintStep predicate is just an OR logic, it could not be a condition that cause fails in the query.
So, how does this happen this way? And is there anyway that allow taint tracking to reach the qualifier of the sink as expected
Link of query and database I used: https://drive.google.com/drive/folders/1ENs1isluvvlmjdpypjfrrxgdRSv6L2sJ?usp=sharing