-
Notifications
You must be signed in to change notification settings - Fork 253
Update Expect-CT to use separator in spec #367
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
| @@ -1,15 +1,15 @@ | |||
| # frozen_string_literal: true | |||
| require "spec_helper" | |||
|
|
|||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I also updated the name of this test, as "expect certificate" was ever so slightly confusing 😄.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Thanks! I think this was my bad from when I had it renamed expect_ct_spec => expect_certificate_spec 😛
|
Nice find @ptoomey3! We've got this deployed using the commas and while I don't see anything in Is it just me? Or does the net internals not report on unenforced policies for Expect CT? |
|
@jacobbednarz - You on Chrome 61 (the first version to ship with it I think)? We haven't updated the deploy on github.com to use the patch here just yet, but will post back when we do. |
|
I'm on 64. Derpp, I just re-read (and read again!) to see GitHub is on the same delimiter as us so it is expected to be the same. |
|
Calling @estark37 - What should we be looking for on chrome://net-internals/#hsts 😄? |
|
Yeah..I manually forced our policy to use commas using an intercepting proxy, and don't see any results when using the "Query Expect-CT domain" in Chrome 64. |
|
Filed https://bugs.chromium.org/p/chromium/issues/detail?id=776658 to fix chrome://net-internals when I'm back next week. As a side note, a policy injected with an intercepting proxy won't work because, like HPKP, Expect-CT is ignored for invalid certificates or certificates that chain to locally-installed roots. |
I had one of those moments when you wake up and instantly have a thought from something you were doing yesterday. Today it was "Doh..I bet you anything Emily left a comment saing 'it won't work with an intercepting proxy because, like HPKP, ..." 😄. I'll double check this again once we have the update here deployed. |
Cool..yeah, I see that site working fine. I'm guessing all will be well once we push out the semicolon to comma change. Thanks! |
Looks like you can take one task off your todo list next week: |
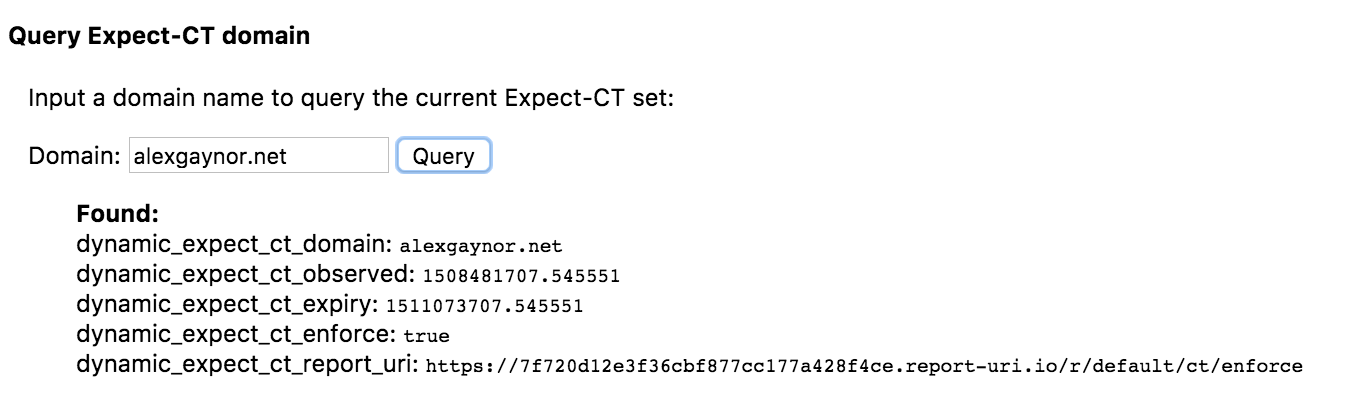
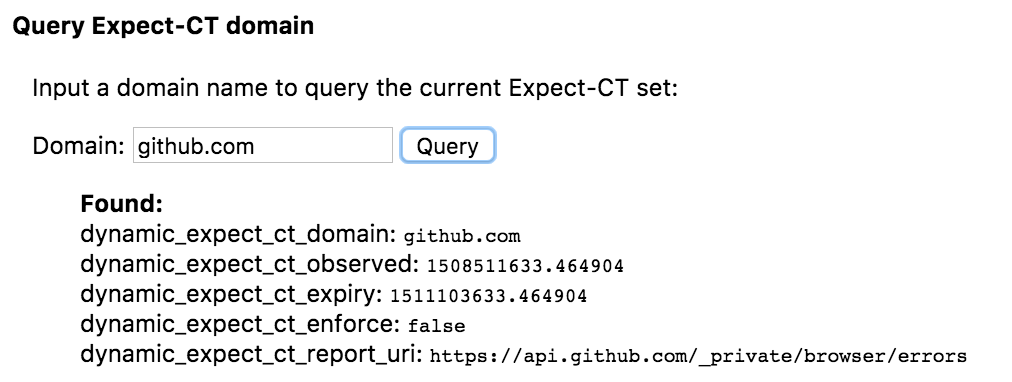
All PRs:
Update Expect-CT to use separator specified in the current spec
It seems like semicolons were maybe specified at some point, since various articles written (ex. https://scotthelme.co.uk/a-new-security-header-expect-ct/) use semicolon as the delimiter. But, in the current spec (https://tools.ietf.org/html/draft-ietf-httpbis-expect-ct), commas are used.
/cc @oreoshake - Since we just deployed this, I think I can confirm the semi-colons aren't working, as I didn't see any expect-ct related data when querying chrome://net-internals/#hsts.