Allow conversion of some IPv4 header fields to host byte order when serialized#640
Allow conversion of some IPv4 header fields to host byte order when serialized#640i-i-i-i-i-i-i-i-i-i wants to merge 1 commit intogoogle:masterfrom
Conversation
042493b to
7ea78af
Compare
|
It's worth noting that this will require extra attention on the header deserialization side. As reflected again in header.go, there are even more OS-dependent interpretations of IPv4 headers that must be accounted for. I'm happy to implement and test these, but first I'd like to see what approach seems best to others. I do think getting a serialization fix merged would be a priority for systems that need to construct packets with custom headers (e.g. for transparently forwarding packets with UDP). |
|
I'm not completely sure about this, since I use those OSes only on rare occasions, but does this affect both bpf sockets and raw sockets? (So far I was under the impression this only affects raw sockets - but I might be mistaken here). |
|
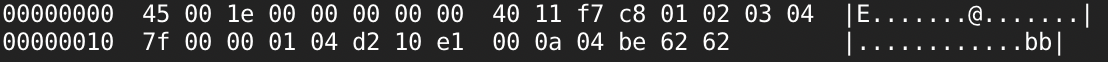
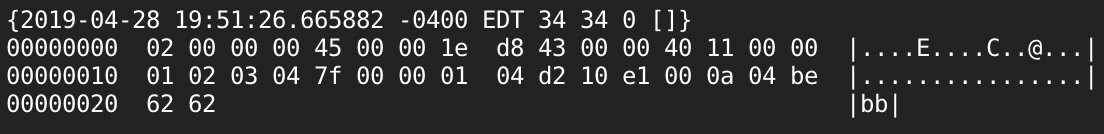
Good point - I don't believe this affects BPF sockets. Testing with gopacket's BPF sniffer, I get identical results with Wireshark, implying that maybe this byte order is only imposed by the kernel when reading from raw IP sockets. Test packet bytes after host endianness conversion, before sending on raw socket (length is 0x001e -> 0x1e00 for little endian): Results in Wireshark/gopacket (length is back to big endian): A bugfix in FreeBSD 11 seems to support this:
|

Just an unassuming fix for #150.
Just to describe the issue concisely:
darwin, dragonfly, netbsd, and freebsd<11.0 expect native byte ordering (only for length/fragmentation offset fields) when writing serialized IPv4 headers to raw IP sockets, as reflected by a fix for ipv4/header.go.
This strange assumption was removed since freebsd 11.0, but the other systems still have issues with this (as used to be the behaviour in freebsd with IP_HDRINCL, you will likely get EINVAL from the kernel due to incorrect packet length).
It would be nice to have a fix inside
SerializeTo, but this would probably require an extra global variable for native byte order along with the magic you see inheader.goto determine versions/endianness. I also assume changing such a critical method for this fix is not ideal.Here is an example from some code that lets you craft empty packets with custom source/destination fields. Later the buffer is used with a raw IP socket (this works on Darwin, whereas I got EINVAL before).
I have tested a good amount with Wireshark to ensure that the length, fragmentation offset, and flag fields are preserved properly in transit.
It would be easy enough to include a function that determines host endianness, but maybe that's best left to the user? Please let me know what you think!