This is an application that automates the issuance and renewal of ACME SSL/TLS certificates for Azure App Services.
- Support for multiple App Services
- Easy to deploy and configure
- Highly reliable implementation
- Ease of Monitoring (Application Insights, Webhook)
You can add multiple certificates to a single App Service.
If you need to use the certificate for a variety of services, consider using the Key Vault version of Acmebot v3.
https://github.com/shibayan/keyvault-acmebot
The Key Vault version can be used with services that support Key Vault certificates, such as App Service / Application Gateway / CDN / Front Door.
- Azure Web Apps and Azure Functions (Windows)
- Azure Web Apps (Linux) / Web App for Containers (Windows and Linux, requires Azure DNS)
- Azure App Service Environment (Windows and Linux)
- Issuing a certificate to the Deployment Slot
- Issuing Certificates for Zone Apex Domains
- Issuing certificates with SANs (subject alternative names) (one certificate for multiple domains)
- Wildcard certificate (requires Azure DNS)
- Support for multiple App Services in a single application
- ACME-compliant Certification Authorities
- Azure Subscription
- App Service with a registered custom domain
- Email address (required to register with Let's Encrypt)
For Azure Cloud
For Azure China
For Azure Government
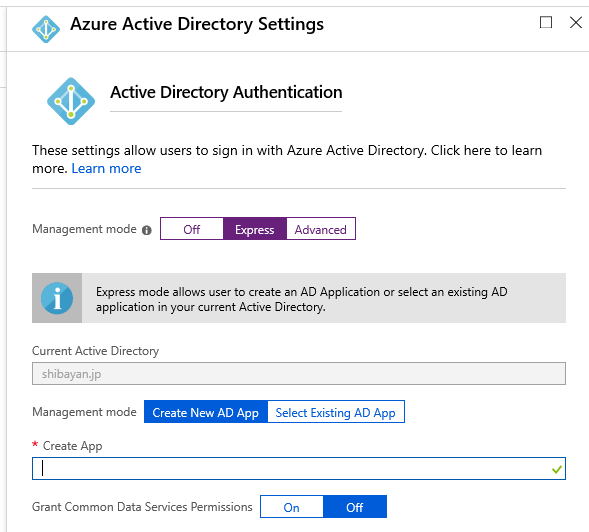
In the Azure Portal, open the Function blade then select the Authentication / Authorization menu and enable App Service authentication. Select the Login with Azure Active Directory as the action to perform if the request is not authenticated. We recommend using Azure Active Directory as your authentication provider, but it works with other providers as well, although it's not supported.
Select Azure Active Directory as the authentication provider, select Express as the management mode, and select OK.
Finally, you can save your previous settings to enable App Service authentication.
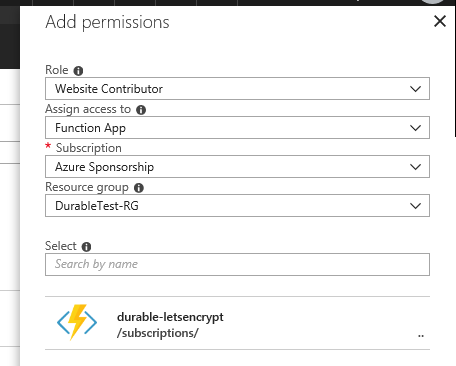
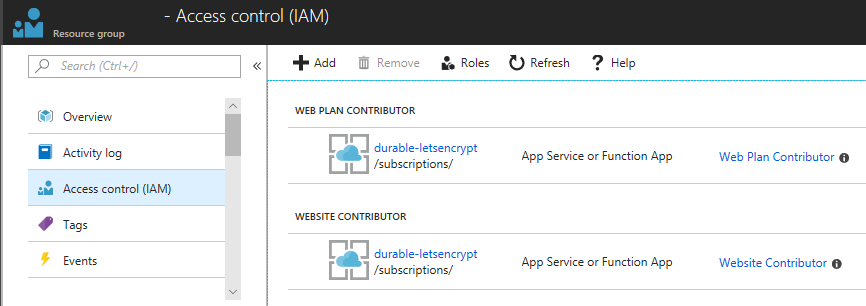
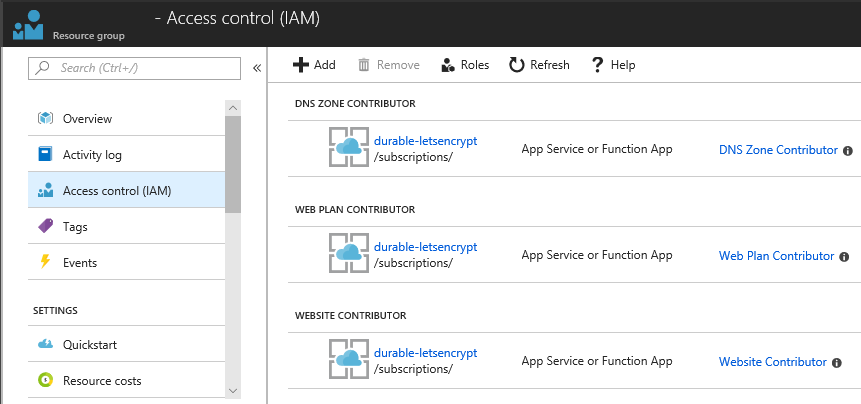
Open the Access control (IAM) of the target resource group and assign the roles Website Contributor and Web Plan Contributor to the deployed application.
Remarks
If the App Service Plan associated with the App Service exists in a separate resource group, you should assign a Website Contributor to the resource group where the App Service exists, and a Web Plan Contributor to the resource group where the App Service Plan exists.
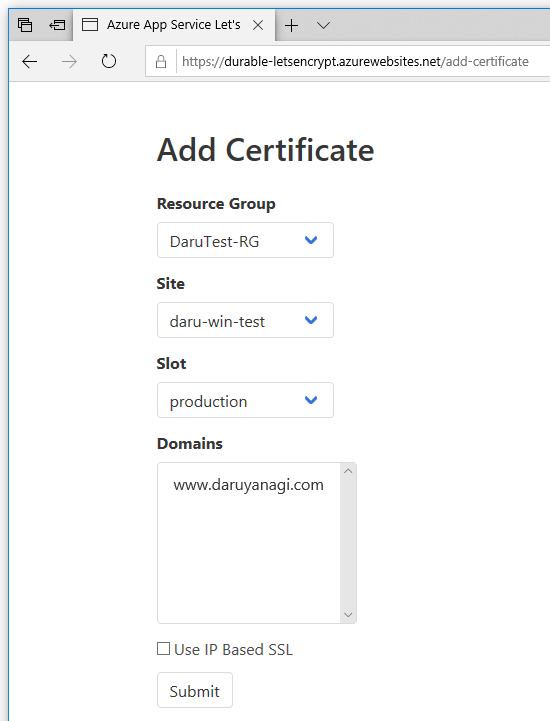
Access https://YOUR-FUNCTIONS.azurewebsites.net/add-certificate with a browser and authenticate with Azure Active Directory and the Web UI will be displayed. Select the target App Service and domain from that screen and run it, and after a few tens of seconds, the certificate will be issued.
If the Access control (IAM) setting is not correct, nothing will be shown in the drop-down list.
To automate the adding of certicates, you can use Acmebot's REST API.
POST /api/certificate
Content-Type: application/json
x-functions-key: asd+YourFunctionKeyHere+fgh==
{
"ResourceGroupName": "your-webapp-rg",
"AppName": "your-webapp",
"SlotName": "production",
"DnsNames": [
"example.com",
"www.example.com"
]
}
See also https://github.com/shibayan/keyvault-acmebot/wiki/REST-API
Because Azure DNS is required to issue wildcard certificates or certificates for Linux, assign the role of DNS Zone Contributor in the resource group containing the target DNS zone.
To issue certificates for "App Service on Linux" and "Web App for Container", Azure DNS is always required.
All existing ACME certificates are automatically renewed 30 days before their expiration.
The default check timing is 00:00 UTC. If you need to change the time zone, use WEBSITE_TIME_ZONE to set the time zone.
The application is automatically updated so that you are always up to date with the latest version. If you explicitly need to deploy the latest version, restart the Azure Function.
You can prevent Acmebot from creating a web.config by creating your own web.config and configured files in the site/.well-known directory.
The role assignment to the target resource group may be incorrect or not yet active. It may take up to 30 minutes for the IAM settings to take effect.
In order for the certificate to be created, the Acmebot needs to create a TXT DNS record for _acme-challenge in Azure DNS. This error occurs when the TXT record isn't being served. One cause of this may be that the nameservers for your domain may be pointing to the domain registrar, rather than Azure DNS. Make sure that you have properly delegated the domain to Azure DNS: Host your domain in Azure DNS
CheckHttpChallenge failed: http://{domain}/.well-known/acme-challenge/{challenge} is InternalServerError status code
This seems like an URL rewrite error. Try setting inheritInChildApplications="false" in the web.config under wwwroot.
- ACMESharp Core by @ebekker
- Durable Functions by @cgillum and contributors
- DnsClient.NET by @MichaCo
This project is licensed under the Apache License 2.0