-
Notifications
You must be signed in to change notification settings - Fork 62
Change spoof login response back to 200 + JSON #1785
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
| let mut response = http_response_see_other(String::from("/"))?; | ||
| let mut response = HttpResponseHeaders::new_unnamed(HttpResponseOk( | ||
| SpoofLoginResponse {}, | ||
| )); |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
This was kind of a weird API, had to look at the Dropshot source to find a way that works. But I get the feeling what I'm trying to do here is a little unusual.
|
Ah, sorry for the breakage. Thanks for fixing it. This is okay but I'm worried this solution leads to more confusion elsewhere... I'm not really sure so I'm thinking out loud here. It feels like the response codes for the login endpoints should be consistent, right? The SAML flow carries through state about where you were coming from so that the server can redirect you back there after login. I think that means If we do want to change to a 200-level code, would "204 No Content" (with an empty response body) work? We do that for some other endpoints so I'd expect clients to be okay with this. It seems cleaner than a 200 with a special type that happens to be empty. We could also return a 300 (with "Location" header) and still provide a JSON response body. I didn't do that because I wasn't sure what information we'd want to put in the response that's not already available in the status code and Location header. But HTTP encourages a response body and we can do that. But that raises the question: should the generator just handle 303s with no response better (i.e., similar to what it does for 204s)? What do you think? |
|
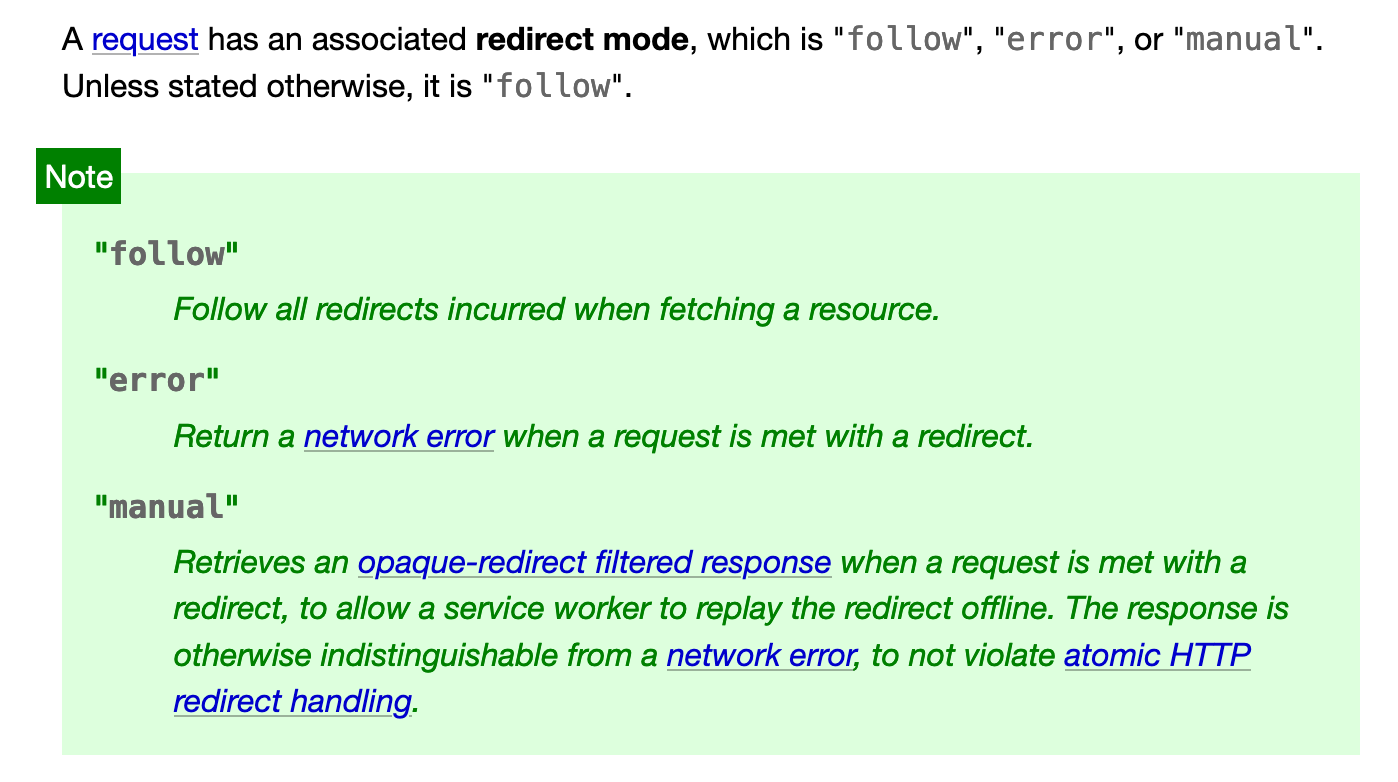
204 makes sense. I think I just forgot that was an option. I will make that change. I think these login endpoints are different for the reasons you give. The SAML login one is where you land after IdP login and we need it to do an actual browser redirect, so the 303 is appropriate there. But spoof login and username/password login are AFAIK going to be hit only as background API calls by the console client. So while, like I said, we certainly could make the generated client treat the 303 as a success and ignore its contents otherwise, I'm not sure it's worth doing because a) this would be the only endpoint we do that for, and b) I don't know of a situation where that 303 is going to be used properly as a 303 (i.e., let the browser handle it and follow the redirect). If you have a 303 that's always meant to be ignored/have its handling suppressed, to me that's at least as confusing as a lack of consistency among the login endpoint responses. On the other hand, if instead of simply pretending in the client that the 303 is a 204, we treat it as success and use the https://fetch.spec.whatwg.org/#concept-request-redirect-mode By default, in |
Crucible changes: Enforce write order of blocks and dirty bit (#1798) Remove unnecessary `unused_async` (#1795) Add `crucible-downstairs validate` subcommand (#1792) Remove incorrect `expect(unused)` annotation (#1789) Handle errors in get-up-state.sh (#1787) Handle final live-repair flush being skipped on all downstairs (#1783) Offline downstairs go to faulted when LR starts (#1777) update drift to pick up fix for OpenAPI type graph cycles (#1785) make Crucible APIs versioned (#1782) Propolis had no changes.
Just Crucible changes, propolis did not change (other than Crucible) Crucible changes: Enforce write order of blocks and dirty bit (#1798) Remove unnecessary `unused_async` (#1795) Add `crucible-downstairs validate` subcommand (#1792) Remove incorrect `expect(unused)` annotation (#1789) Handle errors in get-up-state.sh (#1787) Handle final live-repair flush being skipped on all downstairs (#1783) Offline downstairs go to faulted when LR starts (#1777) update drift to pick up fix for OpenAPI type graph cycles (#1785) make Crucible APIs versioned (#1782) --------- Co-authored-by: Alan Hanson <alan@oxide.computer>
This is 100% on me because I approved the 303 response after talking about it in great detail with @davepacheco, but the 303 is inconvenient for the console. The console makes the
POST /loginthrough the generated client like any other API call, and as such it freaks out if the response isn't JSON.https://github.com/oxidecomputer/oxide.ts/blob/1c4561c83e352513c904c5c5d5b53b65adde88e0/static/http-client.ts#L106
We could try to accommodate this in various ways in the console itself or the generated client, but since AFAIK this endpoint exists solely for the console to use (and may disappear soon enough), it seems a lot easier to just change it back to an empty JSON response.