-
-
Notifications
You must be signed in to change notification settings - Fork 2.2k
Fix branch 1668 #1684
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Fix branch 1668 #1684
Conversation
|
Hi, thanks for the PR However I do not think that this is a proper fix to the issue. As wireshark gets the packets right, it sound like we are wrongly dissecting it. |
Codecov Report
@@ Coverage Diff @@
## master #1684 +/- ##
==========================================
+ Coverage 85.34% 85.38% +0.04%
==========================================
Files 180 180
Lines 42013 42009 -4
==========================================
+ Hits 35855 35871 +16
+ Misses 6158 6138 -20
|
|
Hi, you are right, wireshark gets the packets right, i had an older version (2.4.2) and in this version it was showing an error message. Now, I saw the problem in details, and the problem is with the extension of the handshake protocol helloclient / helloserver : "supported_versions". In the helloclient, there is a byte for the "Supported Versions Length", but not in the helloserver (in the helloclient we can give several versions, but if it is in the helloserver, we are just giving the one we want, so we don't need to give a length) helloclient: helloserver: So the problem is that we try to fill the structure for the helloclient which requires 1 more byte, and then we try to read 2 bytes when we have only 1 left. The result for the sample in the issue will be : The result in wireshark 2.6.3 : |
|
That’s more like it :) thanks. The implementation you provided is all right, however I’d rather have a unique single extension layer. It might be better to use a class TLS_Ext_SupportedVersions(TLS_Ext_Unknown):
name = "TLS Extension - Supported Versions"
fields_desc = [ShortEnumField("type", 0x2b, _tls_ext),
ShortField("len", None),
ConditionalField(
FieldLenField("versionslen", None, fmt='B',
length_of="versions"),
lambda x: x.len % 2),
FieldListField("versions", [],
ShortEnumField("version", None,
_tls_version),
length_from=lambda pkt: pkt.len - (pkt.len % 2))]You could also try to use And last but not lease, we need to have tests on his feature. They are already plenty in |
|
I saw that you added the changes in the pull request #1705 , so I'm closing my pull request. |
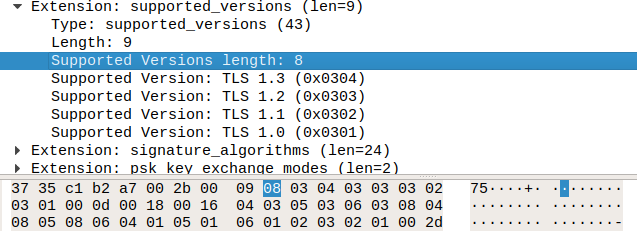
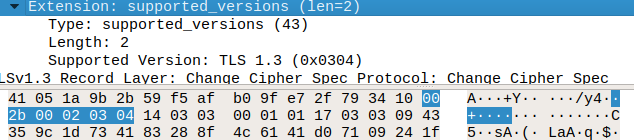
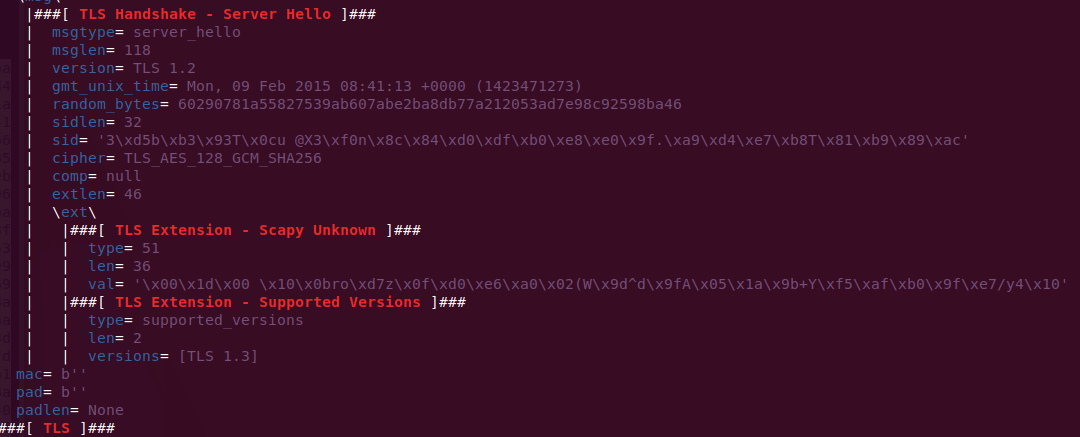
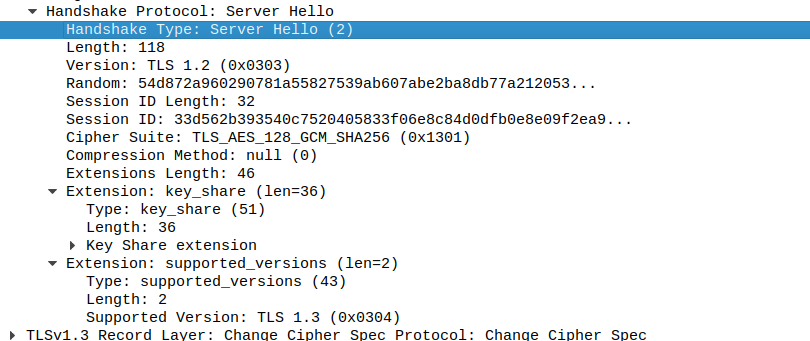
The problem was an extension of the handshake protocole "Server Hello" inside the TLS packet, named "supported_versions".
The length of the versions was supposed to be 3, but the real size was 1, so scapy was trying to parse more than it could, and because of that it was returning the raw data.
The fix is adding a test to know if the size is less than what it should be, and it also does like wireshark, which writes that there is an error/malformation, give the supposed length and the real one. But scapy will also show the raw data.
The result for the code in the issue will be :
###[ TLS ]###type= handshakeversion= TLS 1.2len= 122iv= b''\msg\|###[ TLS Handshake - Server Hello ]###| msgtype= server_hello| msglen= 118| version= TLS 1.2| gmt_unix_time= Mon, 09 Feb 2015 08:41:13 +0000 (1423471273)| random_bytes= 60290781a55827539ab607abe2ba8db77a212053ad7e98c92598ba46| sidlen= 32| sid= '3\xd5b\xb3\x93T\x0cu @X3\xf0n\x8c\x84\xd0\xdf\xb0\xe8\xe0\x9f.\xa9\xd4\xe7\xb8T\x81\xb9\x89\xac'| cipher= TLS_AES_128_GCM_SHA256| comp= null| extlen= 46| \ext\| |###[ TLS Extension - Scapy Unknown ]###| | type= 51| | len= 36| | val= '\x00\x1d\x00 \x10\x0bro\xd7z\x0f\xd0\xe6\xa0\x02(W\x9d^d\x9fA\x05\x1a\x9b+Y\xf5\xaf\xb0\x9f\xe7/y4\x10'| |###[ TLS Extension - Supported Versions ]###| | type= supported_versions| | len= 2| | versionslen= 3| | versions= [b'Error/Malformed: Vector length 3 is too large, truncating it to 1 original is : "\x04"']mac= b''pad= b''padlen= Nonefixes #1668