-
-
Notifications
You must be signed in to change notification settings - Fork 2.2k
#2403 improvement: EXT MS TLS 1.2 #2797
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
18d2926 to
ef3e6a0
Compare
ef3e6a0 to
5e1554b
Compare
Codecov Report
@@ Coverage Diff @@
## master #2797 +/- ##
==========================================
+ Coverage 88.02% 88.36% +0.34%
==========================================
Files 252 252
Lines 53671 53701 +30
==========================================
+ Hits 47242 47455 +213
+ Misses 6429 6246 -183
|
scapy/layers/tls/handshake.py
Outdated
| super(TLSClientKeyExchange, self).tls_session_update(msg_str) | ||
|
|
||
| if self.tls_session.extms: | ||
| hash_object = self.tls_session.pwcs.hash |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Is it correctly fallback to MD5+SHA1 for TLS 1.0 - TLS 1.1 (as said chapter 3 of RFC 7627)?
I've got traffic examples for Extended-Master-Secret for TLS 1.0 & TLS 1.1 only with Encrypt-then-MAC.
So can't check it right now.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I'm not a 100% sure, will check that tonight. Should be defined over
scapy/scapy/layers/tls/session.py
Line 36 in 54da22f
| class connState(object): |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Checked. Current implementation works only for TLS 1.2.
Here fix: https://github.com/strayge/scapy/commit/b6a97dccb880c0285c893a644fc3e57a74f89192
Also for testing I wrote POC of Encrypt-Then-MAC: https://github.com/strayge/scapy/commit/aee5f5712f287256a94ea34a46f577b9434374ae
with both this commits successfully decrypted: TLS 1.0 - TLS 1.2 with EMS + ETM extensions
(checked on AES-CBC & AES-GCM suites)
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Thanks a lot for the PoC ! Looking good.
There are a few things that require changes (I'll go over that tommorow), such as the case where the server doesn't support ExtMS or EncryptThenMac, despite the client request, and everything related to building those packets, but it's a solid start.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Extensions detection placed in TLSServerHello class, so we detect it only if server support it (and client requested it).
Also in PoC missed implementation of Encrypt-Then-MAC for stream ciphers (for AEAD ciphers server must not send this extension, according to RFC).
3dd92a9 to
529a526
Compare
|
@gpotter2 should I made separated PR for Encrypt-then-MAC? |
|
That would probably be a good thing, thanks for the suggestion ! |
|
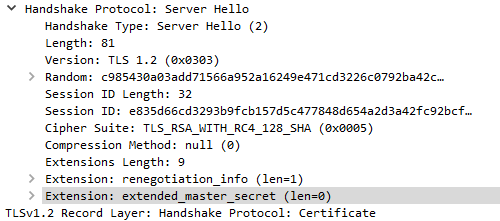
Also I found that current implementation of EMS does not work with TLS 1.2 + RC4. openssl 1.1.1g for client and server. load_layer("tls")
a = rdpcap("./tls12_rc4.pcap")
t1 = TLS(a[0].load)
t1.tls_session.server_rsa_key = PrivKey("./ssl.key")
t2 = TLS(a[1].load, tls_session=t1.tls_session.mirror())
t3 = TLS(a[2].load, tls_session=t2.tls_session.mirror()) |
529a526 to
3412433
Compare
3412433 to
6a797e2
Compare
|
The RC4 example your provided has |
|
I've provided a fix, feel free to try it out. |
0890e29 to
d5451c0
Compare
|
Thanks! Now it works for all my test cases. |
Uh oh!
There was an error while loading. Please reload this page.