-
Notifications
You must be signed in to change notification settings - Fork 4
Avoid CSRF #2
Avoid CSRF #2
Conversation
 mzfr
left a comment
mzfr
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Hey, The fix looks good but I just think that instead of showing the complete debug message there should be some small error that won't give away internal paths etc.
|
@mzfr thanks for the comment, updated |
 mzfr
left a comment
mzfr
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Looks good now
 Mik317
left a comment
Mik317
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Hi @alromh87 😄,
thanks for the great fix 👍
Could you add the protection also for the Delete action?
Cheers,
Mik
|
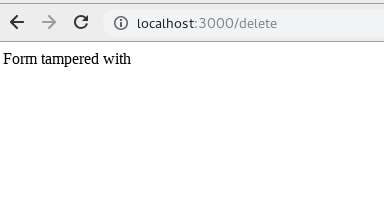
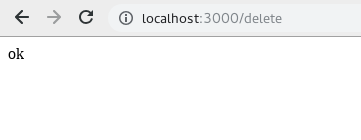
Hello @Mik317 I think delete action is already taken care of, unless I'm missing another endpoint, you can try with this POC: Let me know what you think |
|
Congratulations alromh87 - your fix has been selected! 🎉 Thanks for being part of the community & helping secure the world's open source code. |
📊 Metadata *
Bounty URL: https://www.huntr.dev/bounties/1-other-node-login
⚙️ Description *
node-login is a template for quickly building login systems on top of Node.js & MongoDB. It is vulnerable to CSRF attacks in Update and Delete profile actions
💻 Technical Description *
Avoid CSRF by using csrf token using csurf
🐛 Proof of Concept (PoC) *
🔥 Proof of Fix (PoF) *
After fix data is unafected as csrf token is requiered for post actions
👍 User Acceptance Testing (UAT)
All functinality is unafected
