-
Notifications
You must be signed in to change notification settings - Fork 52
Remove primary key. #3086
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Remove primary key. #3086
Conversation
|
flowcrypt-browser/extension/js/common/core/crypto/key.ts Lines 75 to 80 in da921ab
flowcrypt-browser/test/source/platform/store/key-store.ts Lines 9 to 13 in a79419e
Is there any particular reason for duplicating these? |
|
I would remove the one in Thanks for noticing |
|
@tomholub I'm not getting this:
Could you please explain this in detail? |
|
I'm signing off till Monday. Just removed the |
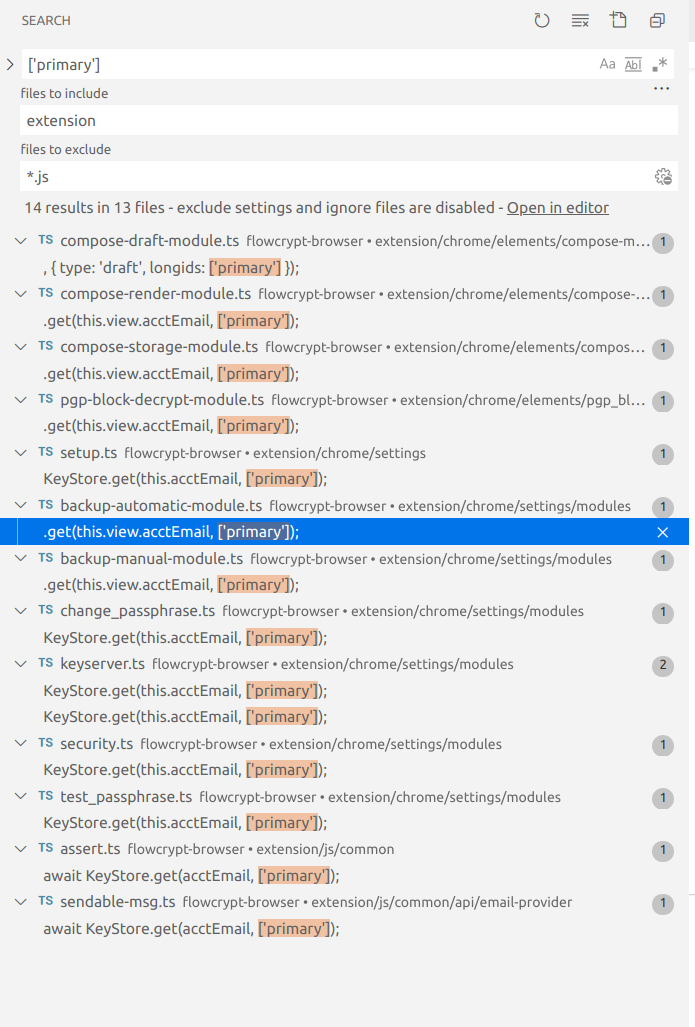
You found a code that you want to refactor which is the following: const allPrivateKeys = await KeyStore.get(this.acctEmail);
this.myPrivateKeys = allPrivateKeys
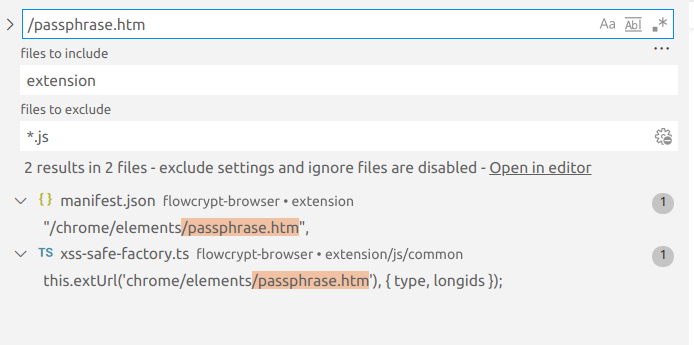
.filter(ki => this.longids.includes(ki.longid) || (ki.primary && this.longids.includes('primary')));You no longer want to deal with having a This is in this.longids = Assert.urlParamRequire.string(uncheckedUrlParams, 'longids').split(',');Some page is hosting / opening / rendering that Brings us to: public srcPassphraseDialog = (longids: string[] = [], type: PassphraseDialogType) => {
return this.frameSrc(this.extUrl('chrome/elements/passphrase.htm'), { type, longids });
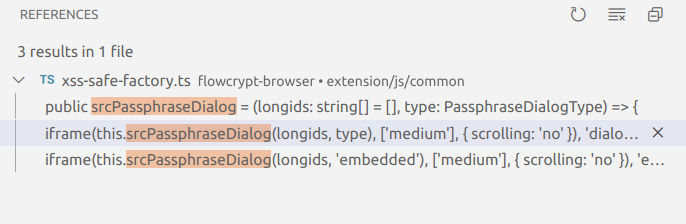
}Brings us to: Example public dialogPassphrase = (longids: string[], type: PassphraseDialogType) => {
return this.divDialog_DANGEROUS(this.iframe(this.srcPassphraseDialog(longids, type), ['medium'], { scrolling: 'no' }), 'dialog-passphrase'); // xss-safe-factory
}Notice the BrowserMsg.addListener('passphrase_dialog', async ({ longids, type }: Bm.PassphraseDialog) => {
if (!$('#cryptup_dialog').length) {
const factory = new XssSafeFactory(this.acctEmail!, this.tabId);
$('body').append(factory.dialogPassphrase(longids, type)); // xss-safe-factory
}
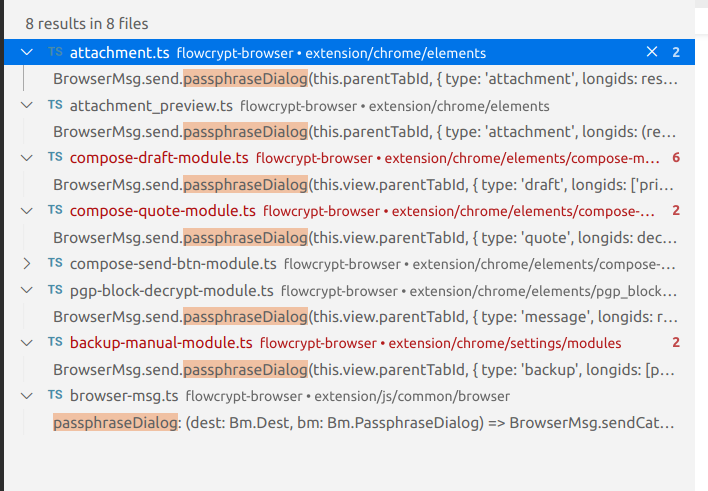
});still not there, now look for the passphraseDialog: (dest: Bm.Dest, bm: Bm.PassphraseDialog) => BrowserMsg.sendCatch(dest, 'passphrase_dialog', bm),See who calls that: Quite a few places (I'm just going along a single path here for example, you'll need to ivestigate all of the other code paths above where I'm just using one for demonstration). If I randomly pick one of them, what I'll see is eg this: BrowserMsg.send.passphraseDialog(this.view.parentTabId, { type: 'message', longids: result.longids.needPassphrase });That looks fine, At least I found one, but I'm only looking causally for this demo This code: this.view.S.cached('prompt').find('a.action_open_passphrase_dialog').click(this.view.setHandler(() => {
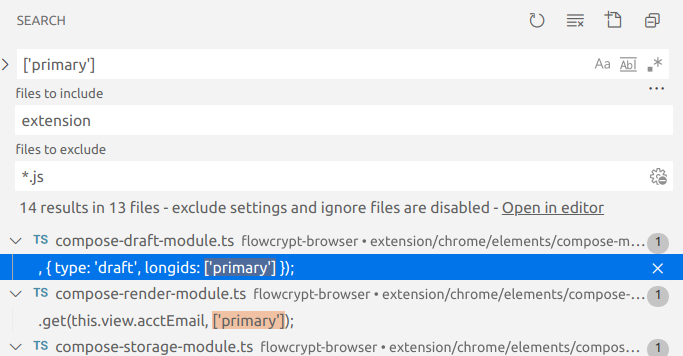
BrowserMsg.send.passphraseDialog(this.view.parentTabId, { type: 'draft', longids: ['primary'] });
}));You'd want to instead grab keys from local storage, and get the first one, then just say You don't want the |
|
There's one more problem we may like to address while we're at it. The public static get = async (acctEmail: string, fingerprints?: string[]): Promise<KeyInfo[]> => {
const stored = await AcctStore.get(acctEmail, ['keys']);
const keys: KeyInfo[] = stored.keys || [];
if (!fingerprints) {
return keys;
}
return keys.filter(ki => {
if (fingerprints.includes('primary') && ki.primary) {
return true;
}
if (fingerprints.includes(ki.fingerprint)) {
return true;
}
return false;
});
}Instead of all of the |
👍 good approach - definitely helps to see something specific. Enjoy your weekend. |
Refactor KeyStore.get(this.view.acctEmail, ['primary']) usages.
 tomholub
left a comment
tomholub
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
All looks good - I have added last few adjustments to make. This change snowballed quite a bit, but it's good that this work is getting done.
|
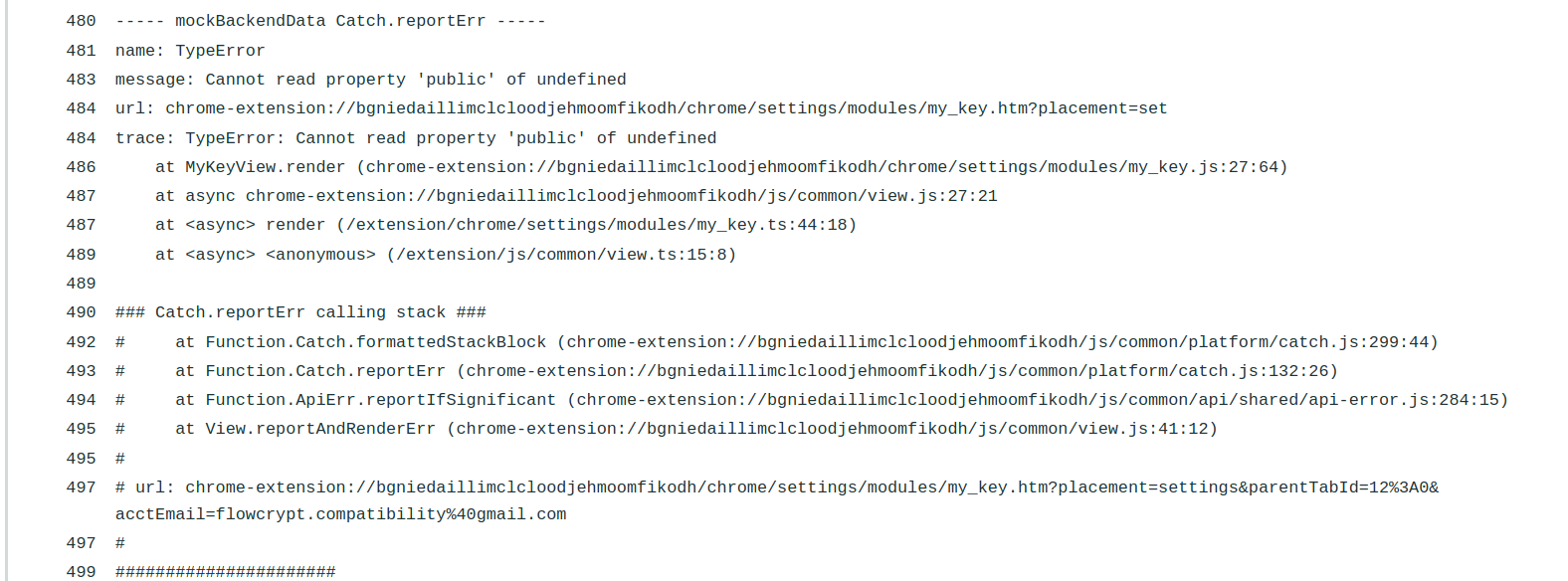
I've added you to semaphore so you can also address the failing tests. https://flowcrypt.semaphoreci.com/workflows/3cceb1b5-98bd-43ba-b064-a27d9dcd564d This is a result of the typing mismatch mentioned above. |
This error happens here:
This is the result of |
I see. I think you'll have to look at the context of the test, and understand why does it get to that state. Check this out: this.fingerprint = Assert.urlParamRequire.optionalString(uncheckedUrlParams, 'fingerprint') || 'primary';Maybe it's getting |
|
Or rather, primary is used as a default value, so you'd want to change that to a required string, and make sure it's provided by the page that renders it. |
|
@tomholub All tests pass. Please, check the code. |
 tomholub
left a comment
tomholub
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Almost there, some fixes left, and some stuff will be to create issues for later.
|
I'll go do some manual testing. Code looks good. There seems to still be one test failure left. |
|
Manual testing looks good |
|
I'll fix it |
Closes #409.