-
-
Notifications
You must be signed in to change notification settings - Fork 508
Closed
Labels
Description
Describe the bug
Using this tool on /lib64/libgcc_s.so.1 (or many other system libraries) on RedHat 5, resulted corruption to the shared object.
After investigating the issue, I believe I have found the root-cause:
The roundup function, handles int values (32bit) while it is sometimes used with 64bit values:
void ElfFile<ElfFileParamNames>::rewriteSectionsLibrary()
{
/* For dynamic libraries, we just place the replacement sections
at the end of the file. They're mapped into memory by a
PT_LOAD segment located directly after the last virtual address
page of other segments. */
Elf_Addr startPage = 0;
for (unsigned int i = 0; i < phdrs.size(); ++i) {
Elf_Addr thisPage = roundUp(rdi(phdrs[i].p_vaddr) + rdi(phdrs[i].p_memsz), getPageSize());
if (thisPage > startPage) startPage = thisPage;
}
...
When phdrs[i].p_vaddr requires 64 bit representation, it leads to the corruption.
Steps To Reproduce
- Extract my files myElfs.zip
- Run
patchelf --debug --add-needed eytan.so ./libgcc_s.so.1 - File is now corrupted even if it finds eytans.so :)
- Output of following commands fails (needless to say libgcc is a dynamic executable):
[root@agentcos5smp3 wip]# ldd libgcc_s.so.1
not a dynamic executable
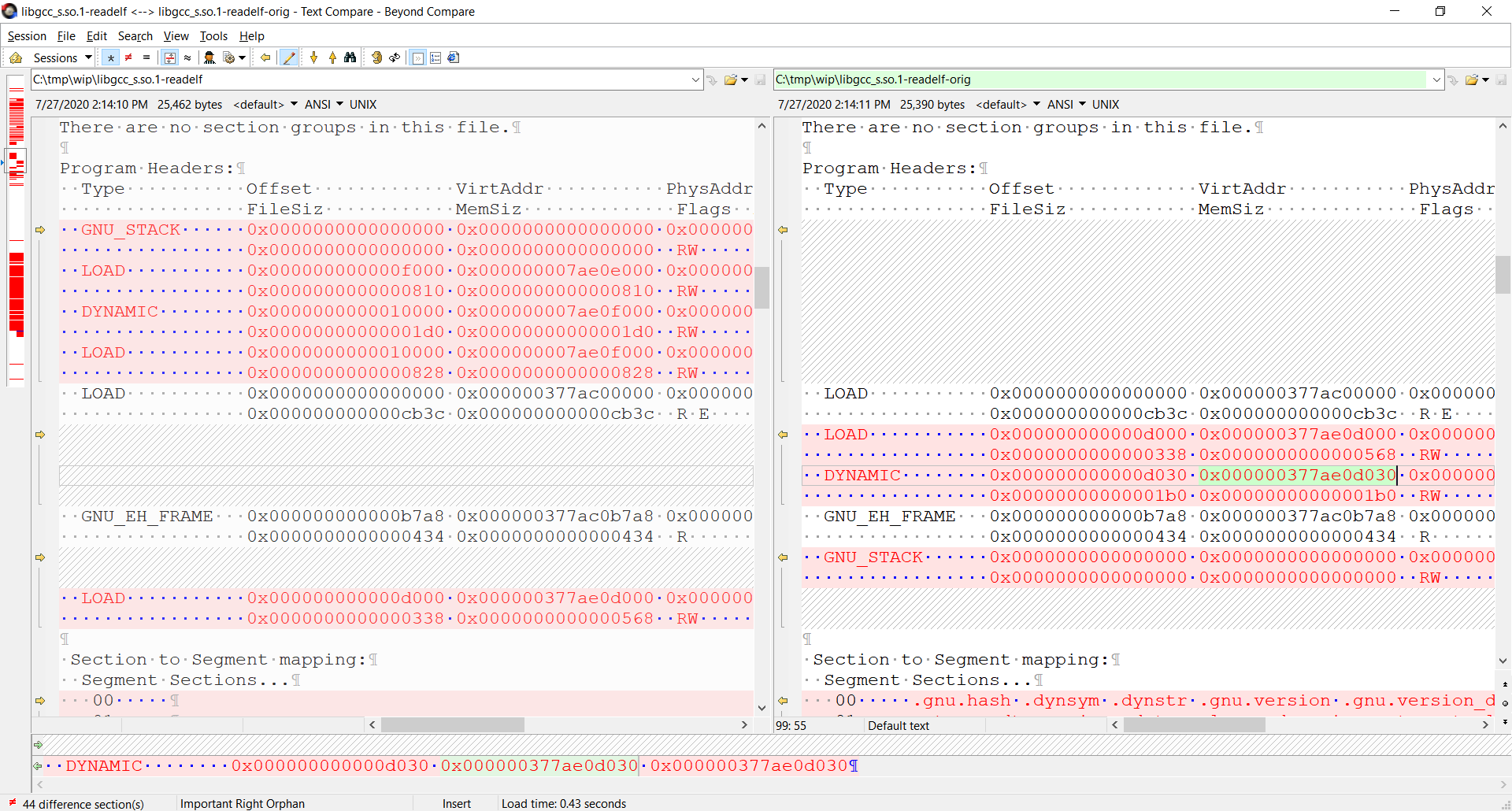
[root@agentcos5smp3 wip]# readelf -a libgcc_s.so.1 > /dev/null
readelf: Warning: Virtual address 0x377ac68168 not located in any PT_LOAD segment.
readelf: Error: Unable to read in dynamic data
Comparing the readelf output of before and after shows the issue:
The 64bit value of 0x000000377ae***** is being trimmed to 0x000000007ae***** due to a bad roundup
Expected behavior
File to valid
patchelf --version output
patchelf 0.11
Additional context
Add any other context about the problem here.