-
Notifications
You must be signed in to change notification settings - Fork 16.4k
Closed
Labels
affected_version:2.1Issues Reported for 2.1Issues Reported for 2.1area:corekind:bugThis is a clearly a bugThis is a clearly a bug
Description
Apache Airflow version
2.1.3
Operating System
AWS K8s
Versions of Apache Airflow Providers
airflow@airflow-worker-0:/opt/airflow$ pip freeze | grep apache-airflow-
apache-airflow-providers-amazon==2.1.0
apache-airflow-providers-celery==2.0.0
apache-airflow-providers-cncf-kubernetes==2.0.2
apache-airflow-providers-docker==2.1.0
apache-airflow-providers-elasticsearch==2.0.2
apache-airflow-providers-ftp==2.0.0
apache-airflow-providers-google==5.0.0
apache-airflow-providers-grpc==2.0.0
apache-airflow-providers-hashicorp==2.0.0
apache-airflow-providers-http==2.0.0
apache-airflow-providers-imap==2.0.0
apache-airflow-providers-microsoft-azure==3.1.0
apache-airflow-providers-mysql==2.1.0
apache-airflow-providers-postgres==2.0.0
apache-airflow-providers-redis==2.0.0
apache-airflow-providers-sendgrid==2.0.0
apache-airflow-providers-sftp==2.1.0
apache-airflow-providers-slack==4.0.0
apache-airflow-providers-sqlite==2.0.0
apache-airflow-providers-ssh==2.1.0
Deployment
Other 3rd-party Helm chart
Deployment details
the web pod installs extrapiplibrary
extraPipPackages:
- "authlib"
- "Flask-AppBuilder==3.1.1"
we have standard deployment on k8s and we have webconfig
webserverConfig:
stringOverride: |
"""Default configuration for the Airflow webserver"""
import logging
import os
import json
from airflow.configuration import conf
from airflow.www.security import AirflowSecurityManager
from flask_appbuilder.security.manager import AUTH_OAUTH
log = logging.getLogger(__name__)
basedir = os.path.abspath(os.path.dirname(__file__))
# The SQLAlchemy connection string.
SQLALCHEMY_DATABASE_URI = conf.get('core', 'SQL_ALCHEMY_CONN')
# Flask-WTF flag for CSRF
WTF_CSRF_ENABLED = True
CSRF_ENABLED = True
# ----------------------------------------------------
# AUTHENTICATION CONFIG
# ----------------------------------------------------
# For details on how to set up each of the following authentication, see
# http://flask-appbuilder.readthedocs.io/en/latest/security.html# authentication-methods
# for details.
# The authentication type
AUTH_TYPE = AUTH_OAUTH
# SECRET_KEY = os.environ.get("FLASK_SECRET_KEY")
# Uncomment to setup Full admin role name
# AUTH_ROLE_ADMIN = 'Admin'
# Uncomment to setup Public role name, no authentication needed
# AUTH_ROLE_PUBLIC = 'Public'
# Will allow user self registration
# AUTH_USER_REGISTRATION = True
# The default user self registration role
# AUTH_USER_REGISTRATION_ROLE = "Public"
OAUTH_PROVIDERS = [{
'name': 'aws_cognito',
# 'whitelist': ['@ga.gov.au'], # optional
'token_key': 'access_token',
'icon': 'fa-amazon',
'remote_app': {
'api_base_url': os.environ.get("OAUTH2_BASE_URL") + "/",
'client_kwargs': {
'scope': 'openid email aws.cognito.signin.user.admin'
},
'authorize_url': os.environ.get("OAUTH2_BASE_URL") + "/authorize",
'access_token_url': os.environ.get("OAUTH2_BASE_URL") + "/token",
'request_token_url': None,
'client_id': os.environ.get("COGNITO_CLIENT_ID"),
'client_secret': os.environ.get("COGNITO_CLIENT_SECRET"),
}
}]
class CognitoAirflowSecurityManager(AirflowSecurityManager):
def oauth_user_info(self, provider, resp):
# log.info("Requesting user info from AWS Cognito: {0}".format(resp))
assert provider == "aws_cognito"
# log.info("Requesting user info from AWS Cognito: {0}".format(resp))
me = self.appbuilder.sm.oauth_remotes[provider].get("userInfo")
return {
"username": me.json().get("username"),
"email": me.json().get("email"),
"first_name": me.json().get("given_name", ""),
"last_name": me.json().get("family_name", ""),
"id": me.json().get("sub", ""),
}
SECURITY_MANAGER_CLASS = CognitoAirflowSecurityManager
###################################
What happened
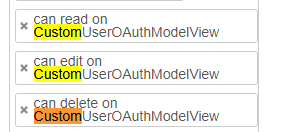
We are using CustomUserOAuthModelView and under roles, there are only three permission that can be add can read on CustomUserOAuthModelView, can edit on CustomUserOAuthModelView, can delete on CustomUserOAuthModelView
The add user button isnt available for Admins and the /Users/add endpoint isn't accessible by Admins.
What you expected to happen
Admin roles should have access to /Users/add endpoint and the add user button should be visible
How to reproduce
upgrade from v1.10.15 to v2.1.3
Anything else
No response
Are you willing to submit PR?
- Yes I am willing to submit a PR!
Code of Conduct
- I agree to follow this project's Code of Conduct
Metadata
Metadata
Assignees
Labels
affected_version:2.1Issues Reported for 2.1Issues Reported for 2.1area:corekind:bugThis is a clearly a bugThis is a clearly a bug