-
Notifications
You must be signed in to change notification settings - Fork 0
Force Two Factor #1
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
…pecific user roles.
…gistered REST constant
|
@joehoyle can I please get a review and test from you on this functionality? It's specifically setup for networks at the moment and also worth noting that I've written the code inline with the standards and style setup for the upstream repo. A lot of the style and architectural pattern is pretty gross, but hoping that we can get this upstreamed faster by going that route. |
|
@mikeselander functinalty wise: it's working great! Though the enable screen looks like this: Have those items at the bottom shown. I ran +1 for a non-multisite support too, as |
Odd, I have never seen those 🤔 I'll try to re-produce.
This is an architectural problem with the plugin itself that would require modifying a good bit of internals to fix. The plugin is built to only ever work on a save submission from a user panel and none of them return or throw errors :( Some of the methods (TOTP for example) do show an error message within their little pane if something has gone wrong.
Ya, I can mostly use the same functions and then registering the options for single sites. I'll add that in 👍 |
|
@joehoyle I've fixed this visual issues and added single site support. Mind taking another look through? |
|
Should this be PR'd directly to the upstream repo rather than merged? |
|
@mikeselander nice, it's looking pretty good to me. I don't know why the plugin shows the "Security Keys" section if you haven't selected U2F. Out of interest, does the plugin allow you to filter the options for 2fa? I guess it could be a site setting again, but it seems odd site administrators can't whitelist the allowed 2fa authentication methods. |
class.two-factor-core.php
Outdated
| $two_factor_forced_roles = self::get_forced_user_roles(); | ||
| $required_roles = array_filter( $user->roles, function( $role ) use ( $two_factor_forced_roles ) { | ||
| return in_array( $role, $two_factor_forced_roles, true ); | ||
| }, ARRAY_FILTER_USE_BOTH); |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Missing space at the end.
class.two-factor-core.php
Outdated
| * @return bool | ||
| */ | ||
| public static function get_universally_forced_option() { | ||
| $is_forced = is_multisite() ? get_site_option( self::FORCED_SITE_META_KEY, false ) : get_option( self::FORCED_SITE_META_KEY, false ); |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
You don't need this ternary:
This function is almost identical to get_option(), except that in multisite, it returns the network-wide option. For non-multisite installs, it uses get_option.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Ah, TIL :)
class.two-factor-core.php
Outdated
| <tbody> | ||
| <tr> | ||
| <th scope="row"> | ||
| <?php esc_html_e( 'Universally force two-factor', 'two-factor' ); ?> |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I'm not sure of this working. "Force all users to enable two-factor"?
|
@mikeselander actually, I see for enable 2fa you are doing it inline, as opposed to redirecting to a specific URL. For whatever reason this means if I am on hte homepage, it shows like this: It might be better to have a discrete URL where this is shown (maybe wp-login.php?action=force-2fa for example), rather than trying to show it in-place on all URLs. |
|
Also noticed I have a fatal on the homepage screenshot:
|
Will look and re-produce 👍
Ya, that's just something that it does ¯\_(ツ)_/¯
It does allow you to filter the methods that are available - The filter is |
@rmccue I wanted to get Joe's feedback before opening a PR against the upstream repo. I also am wary of how long this could take to get merged into the upstream repo and my client needs it this week. |
Yeah, just wanted to check if we wanted to fork or not :) |
|
Linking the upstream PR: WordPress#239 Should we close this PR in favour of handling it over there? |
Allow user to remove forced 2fa on all roles
|
Opening back now, since upstream PR hasn't been merged. |
|
Travis install seems to be busted here, so will ignore and merge, tested the functionality and it seems to be working as expected. |
|
Yeah I think it's missing a git submodule for the xwp dev library |
|
What are your thoughts on the release version? 0.2.2? technically 0.2.1 introduced a bug by missing a bunch of this plugin :/ We can go for 0.3.0 but we'll need to backport that update through to v7 |
Update function.login-header.php to be compatible with WP 5.7
Update class-two-factor-email.php


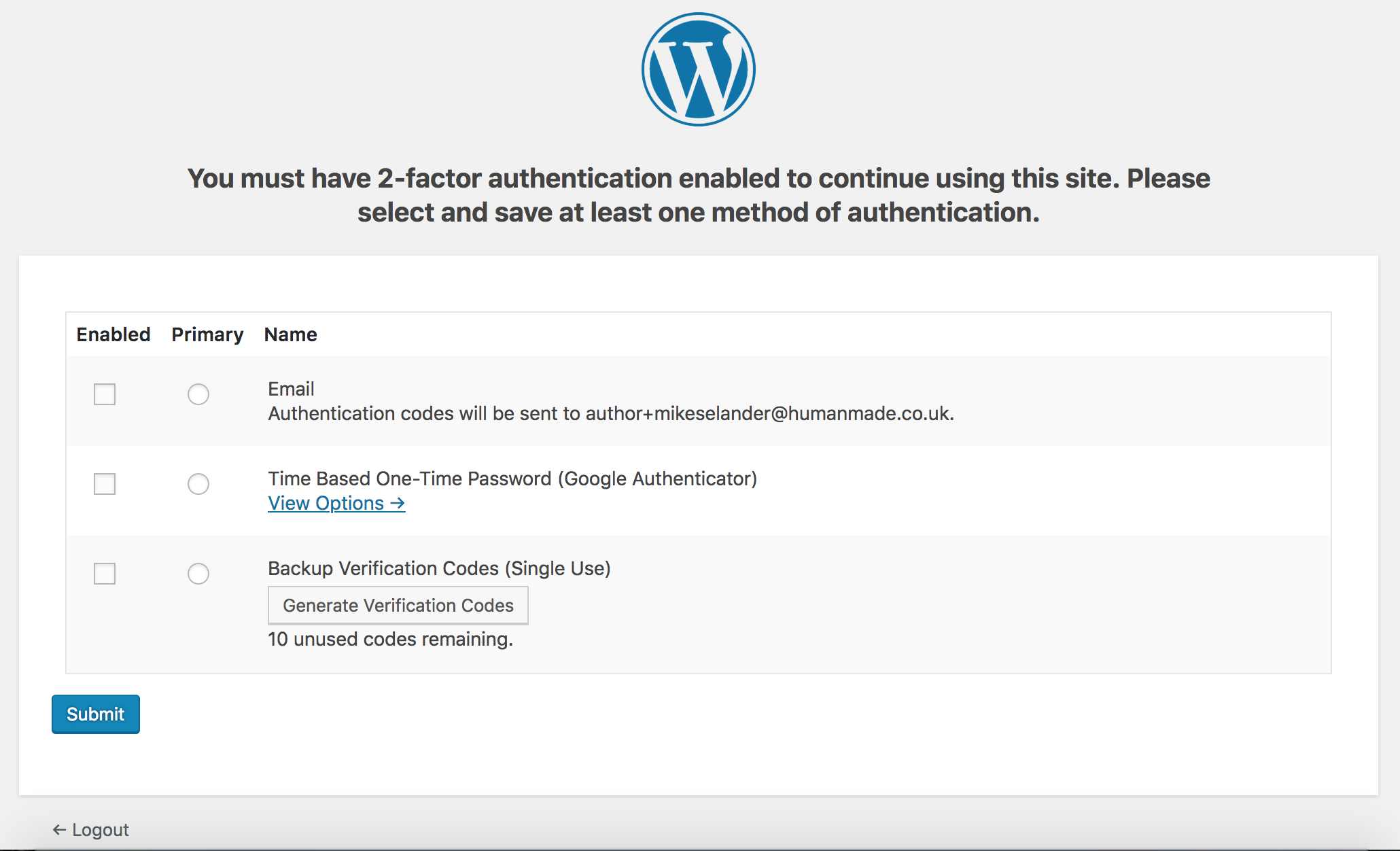
Adds a network-level setting to require two-factor authentication on a per-role or universal level. If 2fa forcing is on and a user matches the criteria, we force the user into a 2fa settings screen and they cannot use the site until they add valid 2fa to their account.
Super administrators can edit the settings with this interface via network settings:

Users who fall within the required buckets will see this interface: