-
Notifications
You must be signed in to change notification settings - Fork 1k
Description
Thank you for reporting an issue or suggesting an enhancement. We appreciate your feedback - to help the team to understand your needs, please complete the below template to ensure we have the necessary details to assist you.
Category
- [X ] Bug
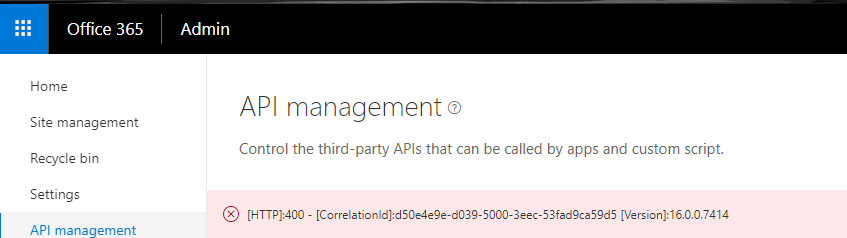
[HTTP]:400 - [CorrelationId] when trying to approve a MS Graph permission request in a SPFx package:
This is the straight tutorial from https://docs.microsoft.com/en-us/sharepoint/dev/spfx/use-aad-tutorial,
so it's pretty bad.
My tenant is on "Targeted released for all users."
Here's the package-soution.json
{
"$schema": "https://dev.office.com/json-schemas/spfx-build/package-solution.schema.json",
"solution": {
"name": "spfx-api-scopes-tutorial-client-side-solution",
"id": "f8e40c26-d627-4e26-b0b7-8d6666166e77",
"version": "1.0.0.0",
"includeClientSideAssets": true,
"webApiPermissionRequests": [
{
"resource": "Microsoft Graph",
"scope": "User.ReadBasic.All"
}
]
},
"paths": {
"zippedPackage": "solution/spfx-api-scopes-tutorial.sppkg"
}
}
Expected or Desired Behavior
I should be able to approve the permission request when I log in as a Global Admin. If there is some legitimate reason why the above package should not be manageable, there should be some way more informative message than below.
Observed Behavior
[HTTP]:400 - [CorrelationId]:d50e4e9e-d039-5000-3eec-53fad9ca59d5 [Version]:16.0.0.7414
When I looked up the ULS logs the most relevant stack tracke I could find was this:
Exception occured in scope Microsoft.Online.SharePoint.TenantAdministration.Internal.SPOWebAppServicePrincipalPermissionRequest.Approve. Exception=System.ArgumentException: A service principal with the name Microsoft Graph could not be found. Parameter name: resourceName
at Microsoft.Online.SharePoint.TenantAdministration.Internal.SPOWebAppServicePrincipal.Consent(SPOWebAppServicePrincipalPermissionRequest permissionRequest)
at Microsoft.Online.SharePoint.TenantAdministration.Internal.SPOWebAppServicePrincipalPermissionRequestCollection.Approve(SPOWebAppServicePrincipalPermissionRequest permissionRequest)
at Microsoft.Online.SharePoint.TenantAdministration.Internal.SPOWebAppServicePrincipalPermissionRequestServerStub.InvokeMethod(Object target, String methodName, ClientValueCollection xmlargs, ProxyContext proxyContext, Boolean& isVoid)
at Microsoft.SharePoint.Client.ServerStub.InvokeMethodWithMonitoredScope(Object target, String methodName, ClientValueCollection args, ProxyContext proxyContext, Boolean& isVoid)
...but the actually "unexpected" line had now exception message and was much more verbose with no obvious problem in the stack. It ends with:
aefae935-f2f6-44ef-9004-766519a1b86c Stack trace:
at Microsoft.SharePoint.SPListItemCollection.EnsureListItemsData()
at Microsoft.SharePoint.SPListItemCollection.get_Count()
Steps to Reproduce
Build the package exactly as described in https://docs.microsoft.com/en-us/sharepoint/dev/spfx/use-aad-tutorial.