-
Notifications
You must be signed in to change notification settings - Fork 125
Data Sniffing
Capture data over an Ethernet network may require some tricks in order to bypass the non-broadcasting behavior of some Ethernet Switches. Generally a switch directs incoming frames on selected ports, this is based on destination MAC address.
In this way an user connected on the LAN isn't in the "listening range" and cannot capture data that are directed to other in the network.
Data capture is useful for debugging and troubleshooting, a common case is missing connection to Souliss while relaying on connection that goes through NAT. Another example could be SoulissApp not receiving data when you don't know the point of failure.
Lets consider the following case: you would capture data between your Android device and a Souliss board, the Android device is connected using a mobile connection and the board is on your local LAN connected via a router to the internet.
To access the data stream between Android and Souliss you need an architecture similar to the one shown below, bridging WiFi and LAN adapters. This solution uses your PC as a bridge between the !WiFi network (connected to Internet) and Souliss. No special IP setup are required in this case.
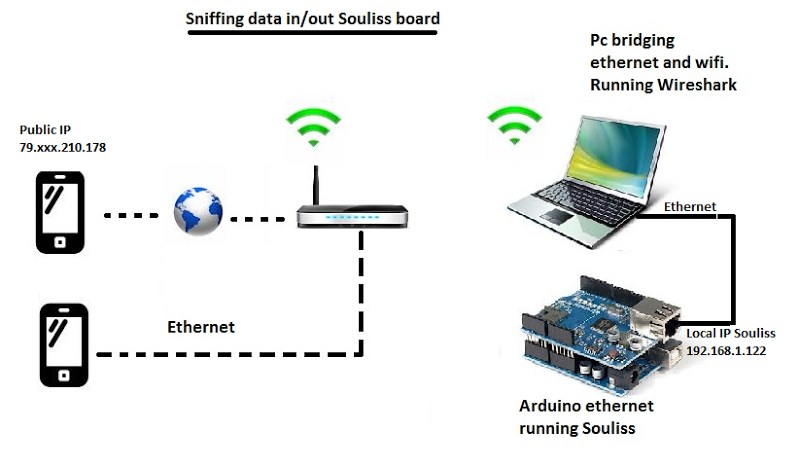
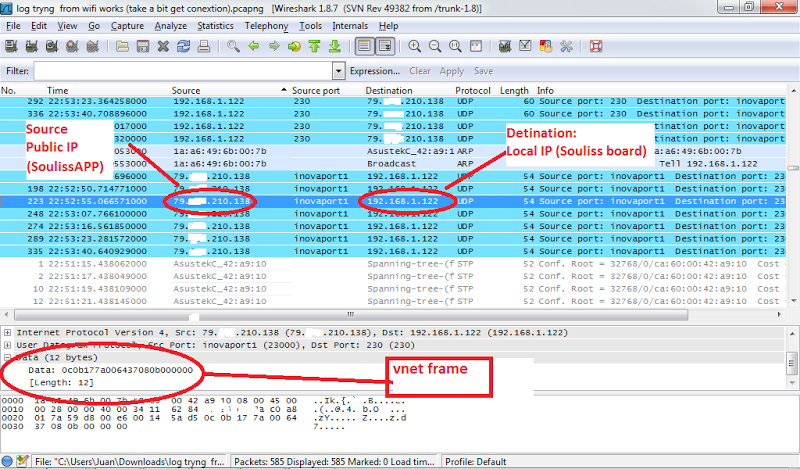
Running a capture software like WireShark let you sniff incoming and outgoing data from your PC, so you have full access to the stream. Souliss packets travel on UDP ports 230 (to boards) and 23000 (to Android)
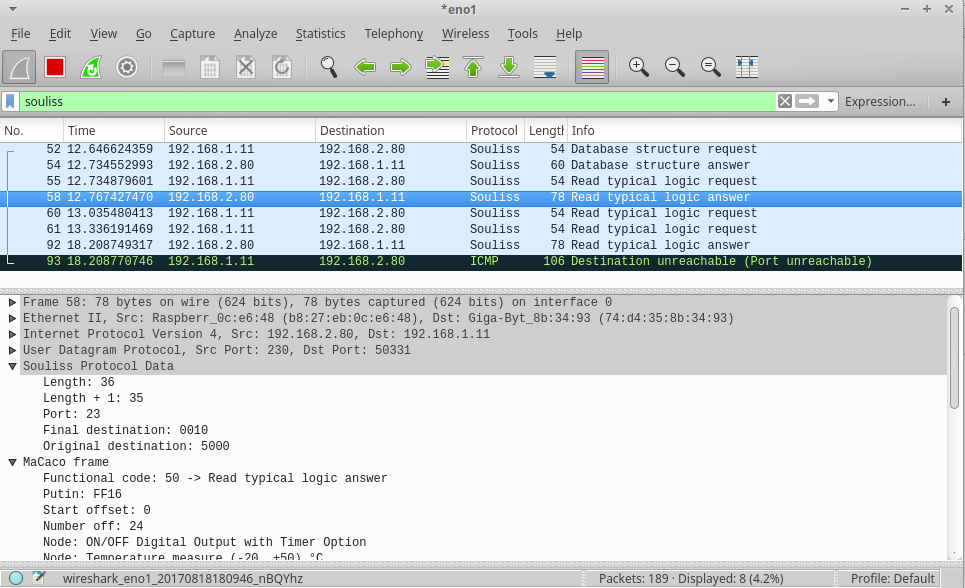
There is a little lua script for WireShark (a "dissector"). Once installed, it allows WireShark to show some information about the vNet frames and MaCaco protocol on Souliss data packets. There are instructions of how to install it on the header of the file.
Download souliss.lua
A different approach that may not work on all switches is the use of MAC Broadcast, this is a set of addresses that router should threat as broadcast, so that can be sniffed on any other device on the broadcast domain (switch).
Use the following inSketch statements to define a custom MAC address with DEBUG option enabled.
#define MAC_INSKETCH
uint8_t MAC_ADDRESS[] = {0x1A, 0xA6, 0x49, 0x6B, 0x00, 0x01};
#define AUTO_MAC 1
#define MAC_DEBUG 1There are other ways to get the data stream, for example you can use an Ethernet Hub as a man in the middle device between the router and Souliss. The hub could forward all incoming traffic to all ports, connecting the PC on the hub, there is full access to the data stream.
Additionally some switches (not the one designed for home using) allow data mirroring on a selected port.
The data stream uses port 230 (and 23000 as Android listening) over UDP frames, a filter by UDP and port lets identify the stream. The source and destination ports may be masqueraded if data goes through a NAT, based on the sniffing point.
The procedure explained before basically put a Personal Computer acting as bridge to the wireless network for your Souliss Gateway board. The traffic to your board is then available in the wireshark capture, but as alternative you can directly sniff traffic on your Android device.
You can look "wireshark" on GooglePlay and use several application, that generally require roots requirements. The result is a capture file that can be read on your computer using Wireshark.
- Introduction
- Getting started
- User Interfaces
- Build your Souliss
- Examples
- Boards
- Interfaces
- Hacks
- Advanced
- Source Code
- Downloads
- Community